As a lot of people were asking for, here comes the code of your badge. All You need to customize your badge, is a micro controller programmer, like the Pickit (its around 30 to 40 euros) and the build environment, MPLAB which you can get for free. Then just download the code and implement your own super cool features. Let us know what you did, the best hacks will get into the TROOPERS hall of fame (-;
Continue reading “TROOPERS13 – The Badge Code”
Tag: tool
All Your Calls Are Still Belong to Us – continued
Hi again and a happy new year 2013!
Lets continue were I left you the last time.
The CTL
The CTL is basically a binary TLV file with 1 byte type, followed by 2 bytes length and finally the data. But as this is far to easy, some special fields omit the length field and just place the data after the type (I guess those are fields with a fixed length). Here is an example CTL file:
Red fields are the types (counting up), green fields are the length (note the missing length on some fileds) and the purple field contains the data (in this case data with a length of 8 bytes and a type 0x05, which is the signing cert serial number btw. [and yes, this is a real example; Cisco signs phone loads with this ‘random’ cert]).
The CTL contains a header with types from 0x01 to 0x0f which is padded with 0x0d. The same header is used for the signed files .sgn from the TFTP server later on. The header describes the file version, the header length, the certificate the file is signed by (further called Signing Cert), the corresponding Certificate Authority, the file name, the files time stamp and finally the signature. The header is followed by multiple cert entries, which again use types 0x01 to 0x0f. The cert entry contains a role field 0x04 which describes the use of the cert. We are interested in the CAPF cert (0x04) and the Call Manager cert (0x02).
Continue reading “All Your Calls Are Still Belong to Us – continued”
Loki for Windows released
Today is a great day, its the day, Loki finally runs on all big operating systems. Im proud to announce the first Loki release for Windows!
There are a few things not working (yet / at all) under Windows. Those are:
- The WLCCP Module – ive not yet managed to build and link against asleap on windows [but time may help (-; ]
- TCP-MD5 Auth for BGP – This will never work, as Windows has no TCP-MD5 impl. in the kernel
- The MPLS Module – Had some hassle here with WinPcap, may be working in the future
The most testing so far was done on Windows 7 were all the other functions work as they do on Linux and Mac.
Download the installer here [1ebf2edbb0cdb631dc2704e82d9c2d778fac703d].
cheers
/daniel
Continue readingReleasing dizzy version 0.6
Hi @all,
today im releasing a new version of our famous fuzzing framework, dizzy. The version counts 0.6 by now and youll get some brand new features!
see the CHANGELOG:
v0.6:
– ssl support
– server side fuzzing mode
– command output
– new dizz funktions: lambda_length, csum, lambda_csum, lambda2_csum
– recursive mutation mode
– new dizz objects: fill
– new interaction objects: null_dizz
– reconnect option
– additional fuzzing values
find the sources here (90397f9ec11c8ec3db7f14cb4d38dd39e30f9791)
cheers
/daniel
Continue readingPython Library for De- and Encoding of WCF-Binary streams
In a .NET environment WCF services can use the proprietary WCF binary XML protocol described here. Microsoft uses this protocol to save some time parsing the transmitted XML data. If you have to (pen-) test such services, it would be nice to read (and modify) the communication between (for example) clients and servers. One possibility is Fiddler.
Fiddler’s strengths include its extensibility and its WCF binary plugins. Sadly, these plugins can only decode and display the binary content as XML text.
Our first tool of choice for webapp pentests (Burp Suite) has also a plugin feature, and one can also find plugins for decoding (and encoding XML back to) WCF binary streams. But all WCF binary plugins out there are based on the .NET library which means one either has to work on MS Windows or with Mono. Another disadvantage is the validation and auto-correction feature of such libraries… not very useful for penetration testing 😉
That’s why we decided to write a small python library according to Microsoft’s Open Specification which enables us to decode and encode WCF binary streams. The library has a rudimentary commandline interface for converting XML to WCF binary and vice versa, as well as a plugin for our python-to-Burp plugin (pyBurp).
Continue reading “Python Library for De- and Encoding of WCF-Binary streams”
Continue readingUse Python for Burp plugins with pyBurp
One of our favorite tools for conducting penetration tests (especially, but not only, web application tests) is Portswiggers’s Burp Suite. Burp allows to extend its features by writing own plugins. But because Burp is written in Java, it only supports Java classes as plugins. Additionally, Burp only allows to use one plugin at the same time which has to be loaded on start-up.
Now we have written a Burp-Python proxy (called pyBurp) which adds some features to the plugin system:
- write plugins in Python
- load and unload plugins at every time
- load multiple plugins
Continue reading “Use Python for Burp plugins with pyBurp”
Continue readingLiferay Portlet Shell
During one of our pentests in some corporate environment we were to analyze an application-server called Liferay. Liferay comes with a lot of functionalities, runs on top of Apache Tomcat and includes a nice API that makes it very easy to add components or further functionality that are not part of the core. These (potentially selfmade) “addons” are called “portlets” and they can be inserted in any place in the frontend.
We quickly found an active default-account (test@liferay.com : test) which immediately led to the question: how to get access on the system-layer through the account on the application. Because we were not aware of any portlet which provided the desired functionality, we decided to write it on our own and created a straight-forward portlet for system level command execution.
As mentioned above, Liferay offers an API for adding portlets to the core. This can be done by creating a standard war-file which contains java-classes, including the desired functionality and some – in this case – Liferay-specific xml-based configuration files. War files are often used to expand the functionality of java-servers (e.g. Tomcat can also be extended via war-files) – it just needs to contain the application-specific xml-files.
Our java-class includes a html-form consisting of an input-field and a button, which sends commands (via GET) to the server. On the server the input gets executed in a shell – a new java HTTP-Shell is born. After some adjustments regarding to the operating system and the java compiler (1) we had a GET-Parameter-based HTTP-Shell.
The following steps are necessary to deploy the shell portlet:
How to create the war-file?
2.) Unzip
3.) Execute create.bat / create.sh [Note: javac and jar must be installed in the PATH.]
4.) Have fun with the ShellPortlet.war
How to deploy the war-file?
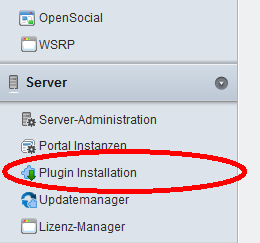
1.) Login to your Liferay-System with a privileged user-account and open http://yourdomain.com/group/control_panel/manage
2.) You should find a category called “Server” on the left side in the navigation. Click “Install Plugin” and on the next site click “Install more plugins” followed by “Fileupload”
3.) Upload the war-file and use “tail -f $CATALINA_HOME/logs/catalina.out” or (on Windows) the Tomcat-console to observe the logs for any error/exception. When everything worked you’ll find an entry like “1 Portlet for ShellPortlet is available for use”
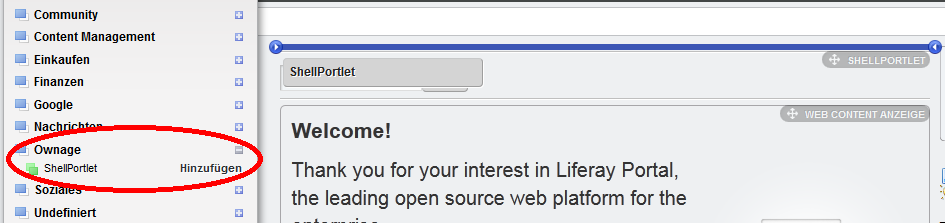
4.) Now go back to your mainpage via the link in the upper area “Back to Liferay”. Then click “Add” -> “More” and you will see all categories in which the portlets are sorted.
5.) If everything went right you will find a category named “Ownage” in this list. Click on it and drag&drop the shellportlet anywhere on your website.
6.) Have fun playing! 🙂
This shows – once again – that it’s not that hard to gain system-access over a (web-) application. Everyone who uses web-applications should secure the higher-privileged accounts by strong passwords or better deactivate them in case they are not needed. It also shows that – once again – comprehensive and reasonable hardening would have prevented the compromise of yet another system.
(1): The java-class must be compiled by the same compiler-version which the tomcat-server is using. (E.g.: If the tomcat uses jre1.6, the java-class in the war-file must be compiled by a javac which is out of the jdk1.6)
SHA1-Hash: f6a7764f098ecc516479dbf6da2ff0017414de00
Continue readingtsakwaf 0.9.1 released
A few weeks ago, I released version 0.9 of a web application testing tool called tsakwaf (The Swiss Army Knife for Web Application Firewalls) together with an ERNW Newsletter about web application firewalls. tsakwaf is based on perl and supports fingerprinting of some supported WAFs and code generation methods to circumvent filter rules. Today, version 0.9.1 will be released, which adds SSL support for the WAF fingerprinting function (Big thanks to Simon Rich!) and a bug fix regarding the detection of WAF reactions which may lead to false positives. Additionally, I’m happy to announce that at least one talk at next year’s Troopers will cover attacks against WAFs (like this one from the 2009 edition) . So mark your calendar – Troopers12 will happen on 21st and 22nd March 2012, with the usual workshops before the conference and the round table sessions the day after – and enjoy playing with tsakwaf!
Download here.
thanks
Frank
Continue readingWeek of releases – apnbf
Another day, another tool 😉
Today I’m proudly releasing the first version of apnbf, a small python script designed for enumerating valid APNs (Access Point Name) on a GTP-C speaking device. It tries to establish a new PDP session with the endpoint via sending a createPDPContextRequest. This request needs to include a valid APN, so one can easily distinguish from a valid APN (which will be answered with a createPDPContextResponse) and an invalid APN (which will be answered with an error indication message). In addition the tool also parses the error indication and displays the reason (which should be “Missing or unknown APN” in case of an invalid APN).
Don’t waste time, get the source here (5a122f198ea35b1501bc3859fd7e87aa57ef853a)
cheers
/daniel
Continue readingWeek of releases – loki-0.2.7
Today I’m going to open up the ‘Week of releases’, which means there will be some new software in the next days.
Lets start with a new version of loki. The version goes up to 0.2.7 and there are a lot of new features:
- SCTP support in the base.
- Invalid option and invalid header scan in the ICMP6 module.
- On-line msg updates for neighbor messages in the RIP module.
- New module for rewriting 802.1Q labels
- Lots of small improvements and bug-fixes
- Some new features I won’t tell right now, get the source and find them yourself 😉
Also there are new packages for gentoo, ubuntu-11.04 and fedora-15, also its the first time, packages for amd64 systems are available.
- Package for gentoo – c29a6cca7a1f7394a473d4b50a1766e9f13fd5a5
Dependencies:
- Manifest – 9338ebcc6a3cb58478671f00cac3114efe5df337
- Package for ubuntu 11.04 i386 – bf9fa05aa20677ac209126b78c3829940daaa8ee
Dependencies:
- pylibpcap – e30c9c8ab1a8e1ee3ddedd05475767dc9f85b526
- Package for ubuntu 11.04 amd64 – 50f5c784f039a15613affd52e304e61fd2a16a58
Dependencies:
- pylibpcap – 9457644ef52fd6bfdb0da8790eee759cc4f76c8b
- Package for fedora 15 i686 – 06398d9c8ca5fd0d80b0da65756b01bfe07652b4
Dependencies:
- pylibpcap – d7e2a9249cba4362d4e435643257ee6a89a412cf
- libdnet-python – 83bbe3895a58d264190afaef586aba8c2bd921f4
- Package for fedora 15 amd64 – 06c1fca3f8390cbe00e8e5c427327379c30222d6
Dependencies:
- pylibpcap – 62d8cc32ef42211584df439ace8f453a3822d5b1
- libdnet-python – d8e969b35b2b5613f364525f21c8e0738a42e061
enjoy!
/daniel
Continue reading