We’ve been involved in some activities in this space recently and I thought it could be a good idea to share a couple of things we’ve discussed & displayed. Furthermore some time ago – in the Is IPv6 more Secure than IPv4? Or Less? post – I announced to come up with (something like) an “IPv6 threats & controls catalogue” at some point… so here we go: in an upcoming series of a few blogposts I will lay out some typical elements of an “Enterprise IPv6 Security Strategy” incl. several technical pieces (and I plan to give a talk on the exact topic at next year’s IPv6 Security Summit).
Let’s start with a little exercise, let’s look at the main threats in IPv4 networks!
From a practitioner’s perspective it might actually make sense to look at the current state of affairs first, in order to get a better understanding how things (more exactly: a network’s security posture) might change when IPv6 gets deployed and how/where to prioritize protection efforts. It might also help to get rid of the “well, we had security weaknesses before, in our IPv4 network, and we did nothing against those. So what’s your point?” attitude some people show once you start discussing IPv6 security issues. Let’s just be realistic and find out what can be ignored (wrt IPv6 sec issues) and what not.
Common Threats in IPv4 Networks
Taking a quick inventory here’s the, from our perspective, most common attacks in IPv4 networks:
- Traffic redirection attacks (stuff like ARP spoofing, DNS spoofing, route injection attacks etc.).
- Attacks against provisioning of configuration information (think DHCP-related stuff).
- Denial-of-Service (DoS) by abuse of protocol features (SYN flooding et.al.).
- Denial-of-Service exploiting (insufficient) implementations (“malformed packet causes device to reload”).
- Denial-of-Service based on load.
- Unauthorized access over the network (IP is about connectivity, so this can be abused…).
I’ll not discuss those in detail as we assume most readers are familiar with them anyway and this step is just about establishing some kind of baseline.
Main Technical Differences between IPv4 and IPv6 Which Affect Security
I’ve discussed some of those before in the above mentioned post but I’ll go a bit more into detail here.
Increased Complexity
Overall IPv6 as a protocol (family) displays a higher degree of complexity than IPv4 (see also here). It is in itself composed of several protocols and mechanisms (“core IPv6” as of RFC2460 et.al., Neighbor Discovery as of RFC 4861, MLD, ICMPv6-based functions like redirects and potentially even others [DHCPv6]). Many of those use multicast transport which inherently is more complex than broadcast based transmission.
This leads (when compared to IPv4) to an increased exposure for:
- Denial-of-Service attacks, in particular from the local-link.
- Human error.
- Undesired interaction between components and technologies (e.g. see this one for a “nice” example).
At this point it should also be kept in mind that storing/processing state information (such as entries in previously ARP/now neighbor caches table or on “stateful” security devices) will require more memory and/or CPU power in IPv6 networks due to the overall higher number of addresses and their properties.
IPv6 Extension Headers
One of the main differences (on the core protocol level) between IPv4 and IPv6 is the introduction of IPv6 Extension Headers which are described in detail in the main IPv6 specification document (RFC 2460) dating from 1998. They can be abused in many ways, namely for evasion of black-list based security controls (like IDPS systems or so-called Infrastructure ACLs supposed to protect devices themselves).
Different Provisioning Paradigm
In IPv4 networks the IP-related configuration of systems was usually done (in a mutually exclusive way) by DHCP or through manual configuration. IPv6 introduced another way of provisioning IP parameters to systems, that is through ICMPv6 router advertisement packets containing various types of configuration information. This is the default approach and it involves routers. Given the inherent trust model of IPv6 (as of the main specifications, management packets on the local-link don’t have any security attributes/properties and hence cannot be authenticated or integrity-protected) this can lead to severe security issues, originating either from human error or from attackers.
New Helper Protocol MLD
The Multicast Listener Discovery protocol (as defined in RFC 3810) plays a huge role for the proper functioning of IPv6 networks (see that unfortunate mention in RFC 4861, sect. 7.2.1 “Joining the solicited-node multicast address is done using a Multicast Listener Discovery such as [MLD] or [MLDv2] protocols.”) which is why all main operating systems both implement it and enable it by default (as opposed to its IPv4 predecessor IGMP). Unfortunately MLD is the source of a number of potential security issues as well (see here or here).
Different/Larger Attack Surface Due to Different (Kernel) Behavior
Implementations of IPv6 in the kernel of operating systems might exhibit more network-level vulnerabilities (due to the higher complexity of the protocol itself, see above) and, more importantly, they might treat specific types of network traffic in a different way than their IPv4 counterparts have done in the past. This might lead to unexpected behavior and/or an increased attack surface. For example several operating systems actually process(ed) packets with an IPv6 source address of ::1 as valid packets whereas they drop IPv4 packets with a source address of 127.0.0.1 once those are received from an external network interface. Another example is the “ICMP[v6] Ping of Death” which was considered to have disappeared a long time ago but reappeared in Microsoft space in 2013.
What Does All This Mean?
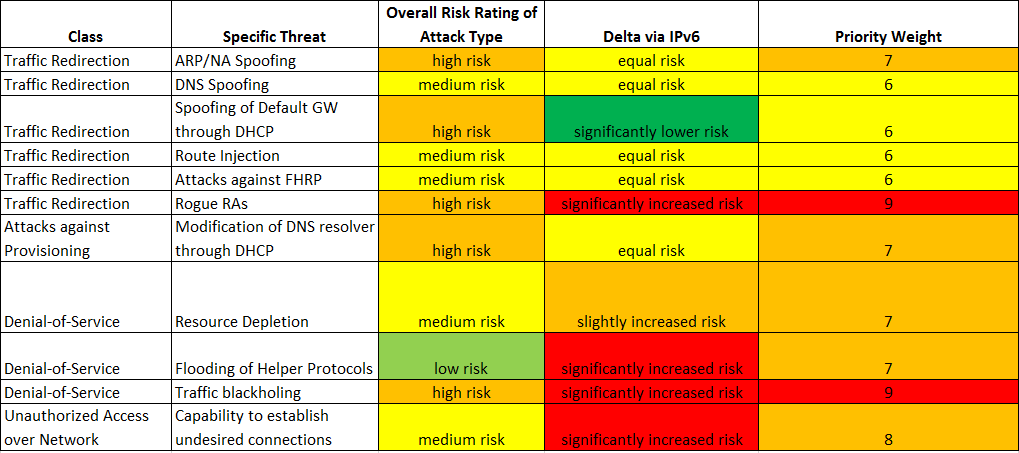
Here’s a small table compiled on the basis of the above discussion. It’s meant to give an indication what actually matters once IPv6 will come to your network (and what not so much).
So, roughly speaking, when comparing threats in IPv4 networks with their IPv6 counterparts, there are mainly three different categories:
- Attacks which result in a lower risk in IPv6 networks compared to the risk in IPv4 networks. The reason for that is either that the attack is more difficult to execute in IPv6 networks or that the impact of a succeeded attack is lower. This is true e.g. for the attack ”Redirection of network traffic through DHCP spoofing“ because a default gateway cannot be distributed through DHCPv6 and therefore not be manipulated by an attacker in an IPv6 network.
- Attacks which result in an equal risk in IPv6 networks compared to the risk in IPv4 networks. Here all risks that have at least a medium risk might be of interest. Still it has to be questioned if there are mitigating measures in the IPv4 network and, if this is not the case, if the security level is actually expected/supposed to be higher in the IPv6 network.
- Attacks which result in a higher risk in IPv6 networks compared to the risk in IPv4 networks. The reason might be that the particular attack (e.g. because of the higher complexity of IPv6) is easier to execute or that the impact for the IPv6 network is higher. In this category attacks in the context of rogue router advertisements are most relevant, because first there is no similar mechanism in IPv4 networks (except for IRDP) and secondly this type of attacks can have a significant impact in IPv6 networks.
Thanks for reading so far ;-); in the second part I will cover mitigation/protection approaches based on the insight (hopefully) gained in this part.
Stay tuned and have a great day,
Enno
Great post, Enno. I will be waiting the second part.