In the course of a current virtualization research project, I was reviewing a lot of documentation on hypervisor security. While “hypervisor security” is a very wide field, hypervisor breakouts are usually one of the most (intensely) discussed topics. I don’t want to go down the road of rating the risk of hypervisor breakouts and giving appropriate recommendations (even though we do this on a regular base which, surprisingly often, leads to almost religious debates. I know I say this way too often:I’ll cover this topic in a future post ;)), but share a few observations of analyzing well-known examples of vulnerabilities that led to guest-to-host-escape scenarios. The following table provides an overview of the vulnerabilities in question:
Continue reading “Analysis of Hypervisor Breakouts”
Author: Matthias Luft
Thoughts on Cloud Governance, Part 1
Last week Rapid7 posted an interesting analysis of the Amazon S3 storage system: Apparently roughly one out of six S3 buckets (a bucket is, simply said, a kind of folder) is accessible without any authentication mechanism. Accessing those files, the Rapid7 guys were able to download a wide range of data, also comprising confidential information such as source code or employee information, comparable to past research for other platforms (see also this presentation I gave on some of the biggest Cloud #Fails)
Continue reading “Thoughts on Cloud Governance, Part 1”
BPDU Guard: Bringing Down Infrastructures
As you may already be familiar with some of our previous work which was mainly focused on isolation issues of hypervisors, we also want to present you an issue concerning availability in Cloud environments. This issue was already covered in some of our presentations, but will be explained in greater detail in this blog post.
Continue reading “BPDU Guard: Bringing Down Infrastructures”
BASTA! Spring 2013
Yesterday I was giving two presentations about Cloud security at the BASTA! Spring 2013 Security Day. While my presentations covered Microsoft Azure security considerations (which also included a part of the Cloud security approach covered in our workshops; slides available here) and some major Cloud incidents (suitable to transport different messages about Cloud security in general ;); slides available here), I also saw Dominick’s very interesting presentation about security aspects and changes in Windows 8. Inspired by that, we hope to be able to publish another blogpost on those aspects with regard to enterprise environments soon — most likely we won’t find any time for it before TROOPERS 😉
Have a good one,
Matthias
Continue readingVMDK Has Left the Building — Newsletter
We are pleased to announce that we summarized the results from our VMDK research in our latest newsletter.
We hope you enjoy the reading and will get some “food for thought”!
The newsletter can be found at:
ERNW_Newsletter_41_ExploitingVirtualFileFormats.pd
A digitally signed version can be found at:
ERNW_Newsletter_41_ExploitingVirtualFileFormats_signed.pdf
Enjoy your weekend,
Matthias
VMDK Has Left the Building — Denial of Service
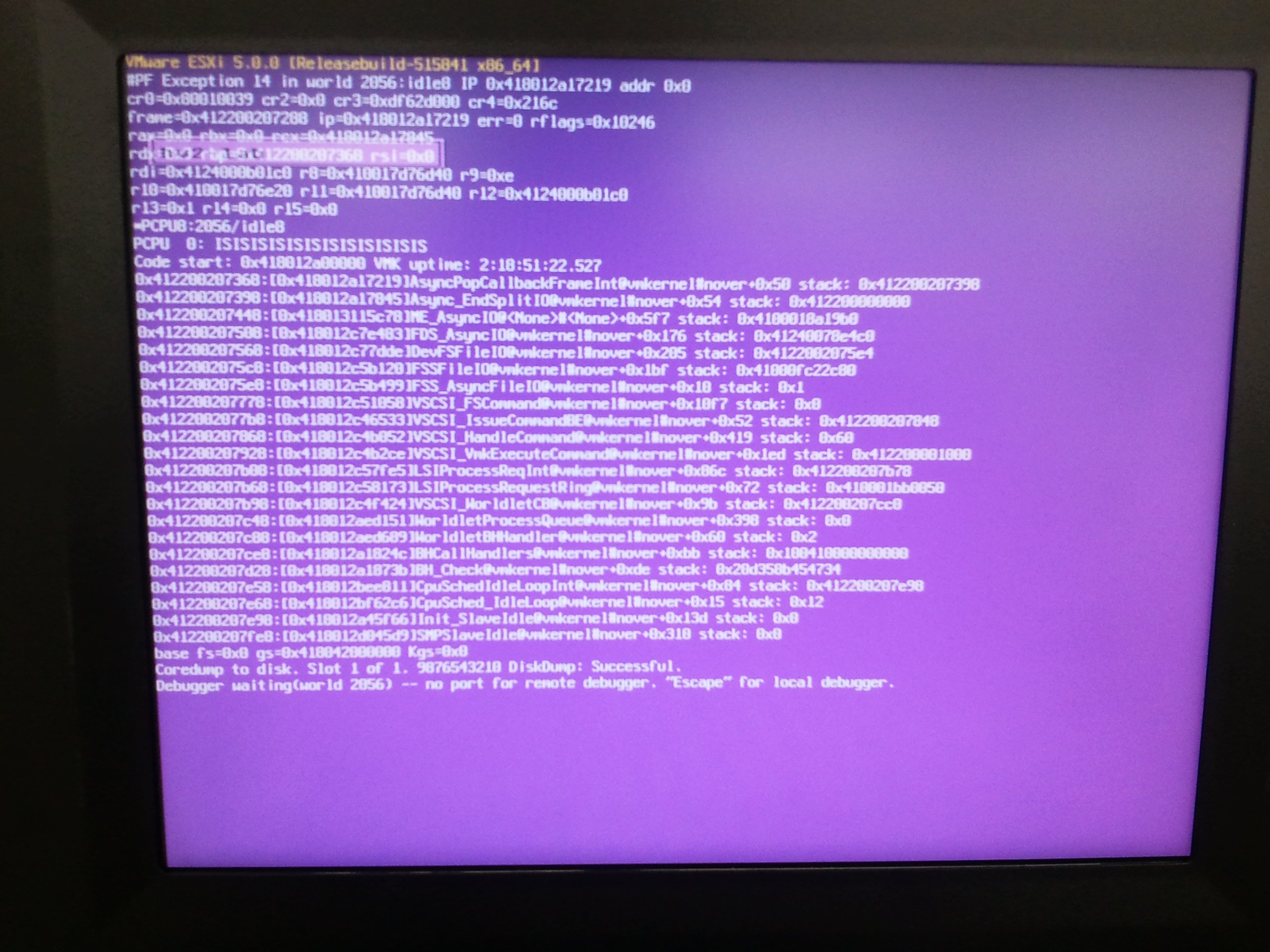
Almost all of our presentations and write-ups on the VMDK File Inclusion Vulnerability contained a slide stating something like
“we’re rather sure that DoS is possible as well ;-)”
including the following screenshot of the ESX purple screen of death:
So it seems like we still owe you that one — sorry for the delay! However the actual attack to trigger this purple screen was rather simple: Just include multiple VMDK raw files that cannot be aligned with 512 Byte blocks — e.g. several files of 512 * X + [0 < Y < 512] Bytes. Writing to a virtual hard drive composed of such single files for a short amount of time (typically one to three minutes, this is what we observed in our lab) triggered the purple screen on both ESXi4 and ESXi5 — at least for a patch level earlier than Releasebuild-515841/March 2012: it seems like this vulnerability was patched in Patch ESXi500-201203201-UG.
Enjoy,
Pascal & Matthias
Continue readingDAY-CON VI
As every year, we will be attending Day-Con, a one-day security summit in Dayton, OH — this year for its VIth edition. Even though the actual conference comprises “only” one day full with talks and discussions (please find the agenda here), the overall event consists of trainings before the conference and PacketWars battles (including an infamous party) afterwards. Since we will be leading and attending some of the training sessions, those might be of particular interest for people who missed our Troopers workshops — so you don’t have to wait a whole year but get another chance in October 😉
Summary:
- October 9th-11th: Training sessions (including the PacketWars Bootcamp — only for the tough ones!)
- October 12th: Conference (Agenda)
- October 13th: PacketWars (including the infamous party)
See you there & have a good one,
Matthias
Continue readingVMDK Has Left the Building — FAQ
As we are receiving a lot of questions about our VMDK has left the building post, we’re compiling this FAQ post — which will be updated as our research goes on.
How does the attack essentially work?
By bringing a specially crafted VMDK file into a VMware ESXi based virtualization environment. The specific attack path is described here.
What is a VMDK file?
A combination of two different types of VMDK files, the plain-text descriptor file containing meta data and the actual binary disk file, describes a VMware virtual hard disk. A detailed description can be found here.
Are the other similar file formats used in virtualization environments?
Yes, for example the following ones:
- VDI (used by e.g. Xen, VirtualBox)
- VHD (used by e.g. HyperV, VirtualBox)
- QCOW (used by e.g. KVM)
Are those vulnerable too?
We don’t know yet and are working on it.
Which part of VMDKs files is responsible for the attack/exposure?
The so-called descriptor file, describing attributes and structure of the virtual disk (See here for a detailed description).
How is this to be modified for a successful attack?
The descriptor file contains paths to filenames which, combined, resemble the actual disk. This path must be modified so that a file on the hypervisor is included (See here for a detailed description).
How would you call this type of attack?
In reference to web hacking vulnerabilities, we would call it a local file inclusion attack.
What is, in your opinion, the root cause for this vulnerability?
Insufficient input validation at both cloud providers and the ESXi hypervisor, and a, from our point of view, misunderstanding of trust boundaries, such as that one should “not import virtual machines from untrusted sources”.
Does this type of attack work in all VMware ESX/vSphere environments?
Basically, the ESXi5 and ESXi4 hypervisor are vulnerable to the described attack as of June 2012. Still, the actual exploitability depends on several additional factors described here.
Can this type of attack be performed if there’s no VMDK upload capability?
No.
Which are typical methods of uploading VMDK files in (public) cloud environments?
E.g. Web-Interface, FTP, API, …
Which are typical methods of uploading VMDK files in corporate environments?
In addition to the mentioned ones, direct deployment to storage, vCloudDirector, …
Will sanitizing the VMDK (descriptor file) mitigate the vulnerability?
Yes, absolutely.
From our perspective this should not be too difficult to implement. There are basically two steps:
- Striping leading directory paths/relative paths from the path to be included
- Restricting included files to customer-owned directories
However a certain knowledge about the specific storage/deployment architecture is necessary in order to sanitize the VMDK descriptor file and not break functionality.
Will VMware patch this vulnerability?
Probably yes. They might do so “silently” though (that is without explicitly mentioning it in an associated VMSA) as they have done in the past for other severe vulnerabilities (e.g. for this one).
Could you please describe the full attack path?
All steps are described here.
More details can be found in a whitepaper to be published soon. Furthermore we will provide a demo with a simplified cloud provider like lab (including, amongst others, an FTP interface to upload files and a web interface to start machines) at upcoming conferences.
Do you need system/root access to the hypervisor in order to successfully carry out the attack?
No. All necessary information can be gathered during the attack.
What is the potential impact of a successful attack?
Read access to the physical hard drives of the hypervisor and thus access to all data/virtual machines on the hypervisor. We’re still researching on the write access.
Which platforms are vulnerable?
As of our current state of research, we can perform the complete attack path exclusively against the ESXi5 and ESXi4 hypervisors.
In case vCloud Director is used for customer access, are these platforms still vulnerable?
To our current knowledge, no. But our research on that is still in progress.
Are OVF uploads/other virtual disk formats vulnerable?
Our research on OVF is still in progress. At the moment, we cannot make a substantiated statement about that.
Is AWS/$MAJOR_CLOUD_PROVIDER vulnerable?
Since we did not perform any in the wild testing, we don’t know this yet. However, we have been contacted by cloud providers in order to discuss the described attack.
Given AWS does not run VMware anyways they will most probably not be vulnerable.
Is it necessary to start the virtual machine in a special way/using a special/uncommon API?
No.
Which VMware products are affected?
At the moment, we can only confirm the vulnerability for the ESXi5 and ESXi4 hypervisors. Still, our research is going on 😉
Stay tuned,
Matthias and Pascal
Continue reading
VMDK Has Left the Building — Some Nasty Attacks Against VMware vSphere 5 Based Cloud Infrastructures
Update #1: Slides are available for download here.
In the course of our ongoing cloud security research, we’re continuously thinking about potential attack vectors against public cloud infrastructures. Approaching this enumeration from an external customer’s (speak: attacker’s 😉 ) perspective, there are the following possibilities to communicate with and thus send malicious input to typical cloud infrastructures:
- Management interfaces
- Guest/hypervisor interaction
- Network communication
- File uploads
As there are already several successful exploits against management interfaces (e.g. here and here) and guest/hypervisor interaction (see for example this one; yes, this is the funny one with that ridiculous recommendation “Do not allow untrusted users access to your virtual machines.” ;-)), we’re focusing on the upload of files to cloud infrastructures in this post. According to our experience with major Infrastructure-as-a-Service (IaaS) cloud providers, the most relevant file upload possibility is the deployment of already existing virtual machines to the provided cloud infrastructure. However, since a quick additional research shows that most of those allow the upload of VMware-based virtual machines and, to the best of our knowledge, the VMware virtualization file format was not analyzed as for potential vulnerabilities yet, we want to provide an analysis of the relevant file types and present resulting attack vectors.
As there are a lot of VMware related file types, a typical virtual machine upload functionality comprises at least two file types:
- VMX
- VMDK
The VMX file is the configuration file for the characteristics of the virtual machine, such as included devices, names, or network interfaces. VMDK files specify the hard disk of a virtual machine and mainly contain two types of files: The descriptor file, which describes the specific setup of the actual disk file, and several disk files containing the actual file system for the virtual machine. The following listing shows a sample VMDK descriptor file:
# Disk DescriptorFile
version=1
encoding="UTF-8"
CID=a5c61889
parentCID=ffffffff
isNativeSnapshot="no"
createType="vmfs"
# Extent description
RW 33554432 VMFS "machine-flat01.vmdk"
RW 33554432 VMFS "machine-flat02.vmdk"
[...]
For this post, it is of particular importance that the inclusion of the actual disk file containing the raw device data allows the inclusion of multiple files or devices (in the listing, the so-called “Extent description”). The deployment of these files into a (public) cloud/virtualized environment can be broken down into several steps:
- Upload to the cloud environment: e.g. by using FTP, web interfaces, $WEB_SERVICE_API (such as the Amazon SOAP API, which admittedly does not allow the upload of virtual machines at the moment).
- Move to the data store: The uploaded virtual machine must be moved to the data store, which is typically some kind of back end storage system/SAN where shares can be attached to hypervisors and guests.
- Deployment on the hypervisor (“starting the virtual machine”): This can include an additional step of “cloning” the virtual machine from the back end storage system to local hypervisor hard drives.
To analyze this process more thoroughly, we built a small lab based on VMware vSphere 5 including
- an ESXi5 hypervisor,
- NFS-based storage, and
- vCenter,
everything fully patched as of 2012/05/24. The deployment process we used was based on common practices we know from different customer projects: The virtual machine was copied to the storage, which is accessible from the hypervisor, and was deployed on the ESXi5 using the vmware-cmd utility utilizing the VMware API. Thinking about actual attacks in this environment, two main approaches come to mind:
- Fuzzing attacks: Given ERNW’s long tradition in the area of fuzzing, this seems to be a viable option. Still this is not in scope of this post, but we’ll lay out some things tomorrow in our workshop at #HITB2012AMS.
- File Inclusion Attacks.
Focusing on the latter, the descriptor file (see above) contains several fields which are worth a closer look. Even though the specification of the VMDK descriptor file will not be discussed here in detail, the most important field for this post is the so-called Extent Description. The extent descriptions basically contain paths to the actual raw disk files containing the file system of the virtual machine and were included in the listing above.
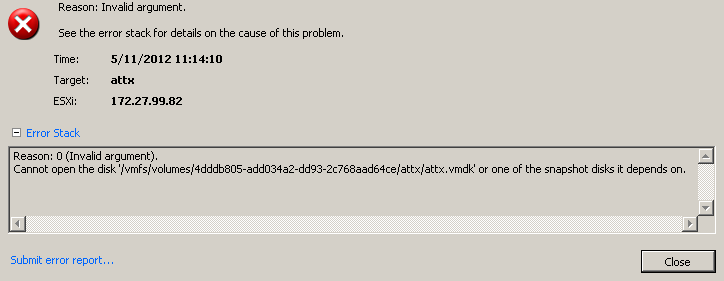
The most obvious idea is to change the path to the actual disk file to another path, somewhere in the ESX file system, like the good ol’ /etc/passwd:
# Disk DescriptorFile
version=1
encoding="UTF-8"
CID=a5c61889
parentCID=ffffffff
isNativeSnapshot="no"
createType="vmfs"
# Extent description
RW 33554432 VMFS "machine-flat01.vmdk"
RW 0 VMFSRAW "/etc/passwd"
Unfortunately, this does not seem to work and results in an error message as the next screenshot shows:
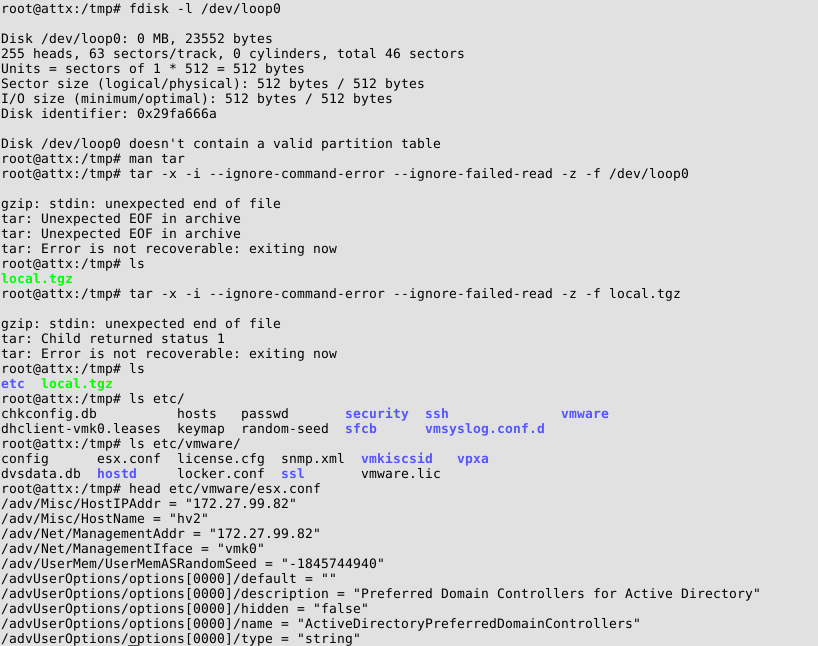
As we are highly convinced that a healthy dose of perseverance (not to say stubbornness 😉 ) is part of any hackers/pentesters attributes, we gave it several other tries. As the file to be included was a raw disk file, we focused on files in binary formats. After some enumeration, we were actually able to include gzip-compressed log files. Since we are now able to access files included in the VMDK files inside the guest virtual machine, this must be clearly stated: We have/can get access to the log files of the ESX hypervisor by deploying a guest virtual machine – a very nice first step! Including further compressed log files, we also included the /bootbank/state.tgz file. This file contains a complete backup of the /etc directory of the hypervisor, including e.g. /etc/shadow – once again, this inclusion was possible from a GUEST machine! As the following screenshot visualizes, the necessary steps to include files from the ESXi5 host include the creation of a loopback device which points to the actual file location (since it is part of the overall VMDK file) and extracting the contents of this loopback device:
The screenshot also shows how it is possible to access information which is clearly belonging to the ESXi5 host from within the guest system. Even though this allows a whole bunch of possible attacks, coming back to the original inclusion of raw disk files, the physical hard drives of the hypervisor qualify as a very interesting target. A look at the device files of the hypervisor (see next screenshot) reveals that the device names are generated in a not-easily-guessable-way:
Using this knowledge we gathered from the hypervisor (this is heavily noted at this point, we’re relying on knowledge that we gathered from our administrative hypervisor access), it was also possible to include the physical hard drives of the hypervisor. Even though we needed additional knowledge for this inclusion, the sheer fact that it is possible for a GUEST virtual machine to access the physical hard drives of the hypervisor is a pretty big deal! As you still might have our stubbornness in mind, it is obvious that we needed to make this inclusion work without knowledge about the hypervisor. Thus let’s provide you with a way to access to any data in a vSphere based cloud environment without further knowledge:
- Ensure that the following requirements are met:
- ESXi5 hypervisor in use (we’re still researching how to port these vulnerabilities to ESX4)
- Deployment of externally provided (in our case, speak: malicious 😉 ) VMDK files is possible
- The cloud provider performs the deployment using the VMware API (e.g. in combination with external storage, which is, as laid out above, a common practice) without further sanitization/input validation/VMDK rewriting.
- Deploy a virtual machine referencing /scratch/log/hostd.0.gz
- Access the included /scratch/log/hostd.0.gz within the guest system and grep for ESXi5 device names 😉
- Deploy another virtual machine referencing the extracted device names
- Enjoy access to all physical hard drives of the hypervisor 😉
It must be noted that the hypervisor hard drives contain the so-called VMFS, which cannot be easily mounted within e.g. a Linux guest machines, but it can be parsed for data, accessed using VMware specific tools, or exported to be mounted on another hypervisor under our own administrative control.
Summarizing the most relevant and devastating message in short:
VMware vSphere 5 based IaaS cloud environments potentially contain possibilities to access other customers’ data…
We’ll conduct some “testing in the field” in the upcoming weeks and get back to you with the results in a whitepaper to be found on this blog. In any case this type of attacks might provide yet-another path for accessing other tenants’ data in multi-tenant environments, even though more research work is needed here. If you have the opportunity you might join our workshop at #HITB2012AMS.
Have a great day,
Pascal, Enno, Matthias, Daniel
Continue readingNo Connectivity — No Malware Protection
During a recent penetration test, we evaluated the security of a typical corporate employee notebook. It was to be assessed whether employees with a default corporate user account would be able to gain administrative access and subsequently abuse the system for attacks against a certain high value database system. When evaluating this problem set, the first step is to find ways to bring tools and exploit code on the system. Usually this task requires the bypassing of the malware protection agent of the system. At some point, we thought we figured a way to encode exploits and payloads in a way that would not be detected by the malware protection solution. Continue reading “No Connectivity — No Malware Protection”
Continue reading