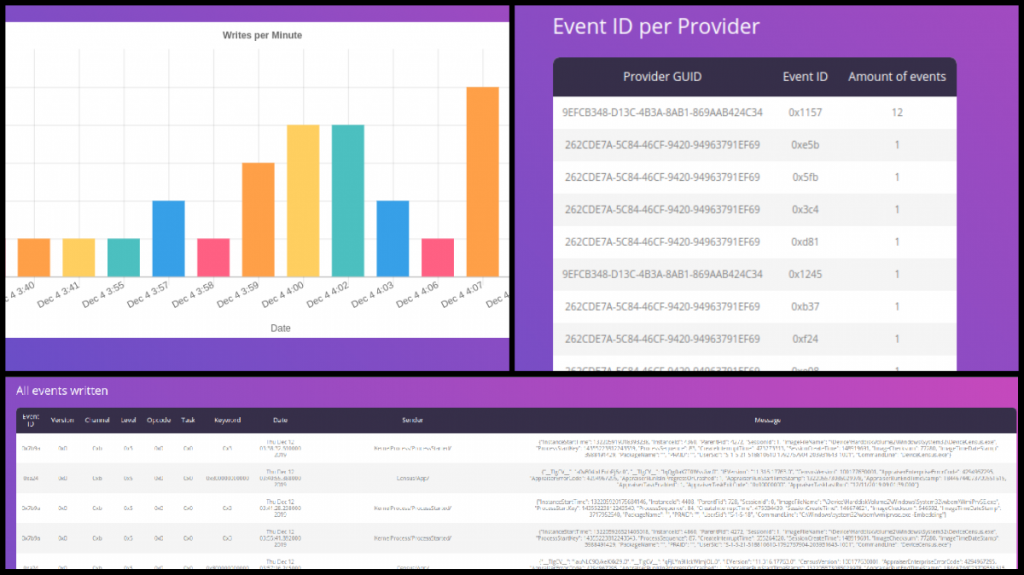
The German Federal Office for Information Security (orig., ger., Bundesamt für Sicherheit in der Informationstechnik – BSI) has published our report on Microsoft Office Telemetry.
Microsoft has released a set of privacy settings for Office, one of which enables users to configure the type and amount of diagnostic (i.e., telemetry) data that Office may send to Microsoft. When deployed, it is available in the form of a group policy setting. It allows users to configure one of the following diagnostic data levels: required, optional, or neither. The report we produced:
- analyzes the impact of the required, optional, and neither diagnostic data levels on the output of diagnostic data produced by Office; and
- provides and evaluates approaches for partially or fully disabling the output of diagnostic data produced by Office.
The report is available here (in English).
Continue reading “Microsoft Office Telemetry: Report Release”
Continue reading