While waiting for a download to complete, I stumbled across an interesting blogpost. The author describes a flaw in LibreOffice that allowed an attacker to execute code. Since this was quite recent, I was interested if my version is vulnerable to this attack and how they fixed it. Thus, I looked at the sources and luckily it was fixed. What I didn’t know before however was, that macros shipped with LibreOffice are executed without prompting the user, even on the highest macro security setting. So, if there would be a system macro from LibreOffice with a bug that allows to execute code, the user would not even get a prompt and the code would be executed right away. Therefor, I started to have a closer look at the source code and found out that exactly this is the case!
Description
LibreOffice is shipped by default with LibreLogo, a macro to programmable move a turtle vector graphic. To move the turtle, LibreLogo executes custom script code that is internally translated to python code and executed. The big problem here is that the code in not translated well and just supplying python code as the script code often results in the same code after translation.
PoC
A document with the following content
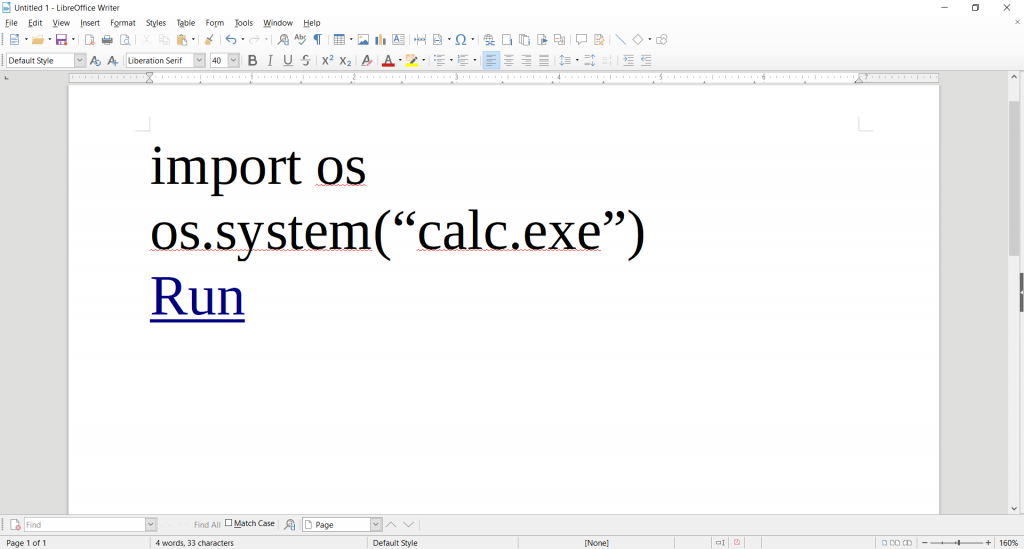
import os os.system(“calc.exe”) Run
where Run is a hyperlink executing LibreLogo:run on a mouseover event, as shown below,
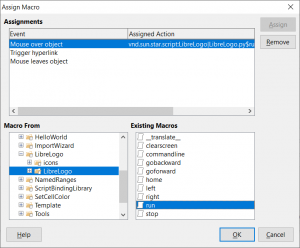
will in fact execute the provided command when when hovering the Run link on a Windows machine, and in our case, open a calculator, as depicted here:
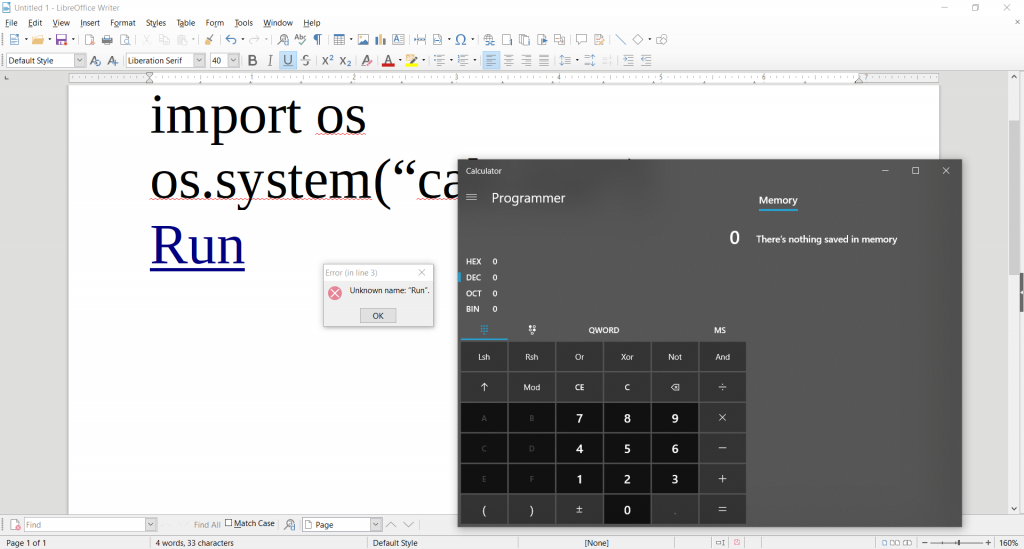
There is no prompt to the user asking to run the code, it is just executed. Using forms and the OnFocus event it is even possible to get code execution when the document is opened, without the need for a mouseover event.
Disclosure Timeline
We responsibly disclosed this vulnerability and in the current version of LibreOffice, it has been fixed and the according CVE-2019-9848 has been published. The disclosure timeline was as follows:
- 16.07.2019 – Public disclosure of vulnerability
- 01.07.2019 – Published fixed version 6.2.5
- 05.06.2019 – Vulnerability was assigned CVE-2019-9848.
- 04.06.2019 – Report of the vulnerability
Conclusions
Macros and the code handling them still have a big attack surface and are likely to have some bugs, therefore I recommend updating LibreOffice and install it without macros or at least without LibreLogo.
Best,
Nils
oi
vou pesquisar como instalar o LibreOffice
sem o Logo e sem macros.
Obrigado Nils.
In the Installation Wizard it is possible to remove LibreLogo. Another solution is to remove or rename pythonscript.py from the installation folder C:\Program Files\LibreOffice\program. This disables all the python macros but might come back with an update. However, I don’t know a cleaner solution to disable all macros.
What does it do on a Linux system? Or does malicious code have to be targeting a specific platform?
If the Version running on the Linux distribution is vulnerable to this attack (has LibreLogo installed and a Version < 6.2.5), Python code can be executed. Python is platform independent and the document could just use
if platform.system()=='Linux':to detect the platform it is on and in turn running different binaries. So, it would be possible to create a document that behaves different on Windows/Linux but runs code on both platforms.