Hello fellow Troopers and Happy new Year!
35C3 is over, and the recordings are available so in case you did not have the chance or the time to watch the live streams during the holidays or overwhelmed with the number of talks, see in the following a list of recommended talks to fill your evenings or weekends. Apart from the broad coverage of topics in different areas (Ethics, Society & Politics, Hardware & Making, Resilience, Art and Culture, Security, Science, Resilience), foundation talks were aiming for the very basics following this year’s motto “Refreshing Memories.”
So, let’s dive into the recommended talks and start with foundation talks to start refreshing our memories with a bit of TCP/IP and TLS1.3 continuing with an overview of the Spectre and Meltdown disaster going over DPRK’s Anti-Virus Solution to finish with the philosophy of mind and artificial intelligence.
Introduction into the Transmission Control Protocol
The talk by Hannes Mehnert provides a rough overview of communication protocols focusing on the transport protocol TCP. Hannes Mehnert, which held an excellent foundation talk about the basics of network communication and TCP, works for a non-profit organization in Berlin called ‘Center for the Cultivation of Technology.’
Using the example of a common HTTP-Request, he described the four most important layers:
- Data Link Layer
- Internet Layer
- Transport Layer
- Application Layer
First, he described the tasks of each layer and named some commonly used protocols on this layer. He talked about the data encapsulation between the layers and which information a layer sees of a specific packet.
He mentioned ICMP, its use in networks and then talks about the UDP- and TCP-Header and its components. In addition, the speaker provided for both protocols a practical simplified code example to implement a client or server in C. At this point, he showed the differences between both, according to its function and parameters. Based on this process described in C code, he showed a typical visualization of the TCP state machine and the process of how a TCP connection is established. Then he mentioned the control mechanisms flow control and congestion control, which are necessary for smooth TCP communications. At last, he introduced netsem [1], which is developed in the interactive theorem prover HOL4 by him and his colleagues at Cambridge University. At this moment there is a draft paper about ‘Engineering with Logic: Rigorous Test-Oracle Specification and Validation of TCP/IP and the Sockets API’ [2] published by them.
This talk gives you short overview about general network communications and the used protocols.
[1] https://github.com/rems-project/netsem
[2] https://www.cl.cam.ac.uk/~pes20/Netsem/paper3.pdf
https://www.youtube.com/watch?v=Fck8rIDvA5o
Kernel Tracing With eBPF
Ever wrote a Linux Kernel Module to trace a system call? In the talk “Kernel Tracing with eBPF” Jeff Dileo and Andy Olsen show you the easy way. In just a few lines of code you are able to trace any open call in /root. The talk includes something for both sides, defensive as offensive. Jeff firstly explains what eBPF is, what it generally can be used for and why one should even use it. Afterwards he follows up with a small summary of history about Linux tracing. From then on practical examples follow.
For example the following code:
from bcc import BPF
prog = """
#include <uapi/linux/ptrace.h>
int kprobe__do_sys_open(struct pt_regs *ctx, int dfd, const char __user *filename) {
char root[] = "/root";
#pragma unroll
for (int i=0; i<5; i++){
if (root[i] != filename[i])
return 0;
}
bpf_trace_printk("attempted access: %s\\n", filename);
return 0;
}
"""
b = BPF(text=prog)
b.trace_print()
The code above does trace the open syscall and if the filename starts with /root it prints out which program executed the syscall and the full path of the file. So for example run the script in one terminal:
user@ernw:~$ sudo python trace_open.py
And in another terminal run:
user@ernw:~$ sudo touch /root/hithere
You should see (nearly) the same output:
user@ernw:~$ sudo python trace_open.py
touch-31784 [000] .... 6442.007509: 0x00000001: attempted access: /root/hithere
There you go, it can be this easy. A thing I should mention is that this could be bypassed with ../../../root/hithere ;D.
There is also another vulnerability in the code above (TOCTOU), but for that one you have to watch the talk [2] ;P. Instead of spending this much time explaining the “eBPF Validator Hell” and how to avoid it, more time should have been spend on actual methods. Thanks for the talk as we already started playing around with bcc and eBPF and had quite some fun.
https://www.youtube.com/watch?v=2lbtr85Yrs4
The Rocky Road to TLS 1.3 and better Internet Encryption
Hanno Böcks talk about TLS1.3 started with a great and well understandable summary of the attacks against past SSL and TLS versions. Hanno explained how Padding Oracle (against CBC cipher mode), Bleichenbacher attack (against RSA encryption), POODLE and ROBOT work and what are the major problems of these kinds of attacks. He also explained that some of the attacks exist due to implementation flaws (such as Padding Oracle in most cases) and some others exist due to design flaws within the protocol standard. Next, to these flaws, Hanno talked about downgrade attacks and how they basically work. He asked rhetorically, who would use SSL Version 3 even though this protocol version is deprecated since 16 years? No one, he immediately responded, but by denying the establishment of TLS1.2, TLS1.1 and TLS1.0 a man-in-the-middle attacker can force the client and server to downgrade to SSLv3 if it is still supported by the corresponding endpoints, which is why some of the attacks still exist.
Next, to the attack scenarios, Hanno went into the major changes of TLS 1.3, such as speed improvements, which are mainly the outcome of the decreased complexity of the establishment process. He stated that “in many ways, TLS 1.3 is the biggest step ever done in the history of TLS and its predecessor SSL. While previous TLS versions always tried to retain compatibility and not change too many things, the new version radically removes problematic and insecure constructions like static RSA key exchanges, fragile CBC/HMAC constructions and broken hash functions like MD5 and SHA1.”
He also talked about changes, that raised some concerns in the IT-Sec community. Such as the so-called 0-Round-Trip-Time (0-RTT) mode in which a connection is established on a set of parameters, that were exchanged the last time this very client connected to the server. This enables an extremely fast and – as of the specification makers – secure connection establishment, but also needs to be correctly implemented and extensively tested.
>From my perspective this talk was a very nice summary and should be watched by everyone who is interested in the TLS progression.
https://www.youtube.com/watch?v=i6mGfZrypP4
A Christmas Carol – The Spectres of the Past, Present, and Future
On day 2 of the Congress, Moritz Lipp, Michael Schwarz, Daniel Gruss, and Claudio Canella from the Core Security Group of TU Graz gave a great introduction into the world of all the Spectre/Meltdown vulnerabilities which came up last year. By telling this story as their very own version of the novella “A Christmas Carol” by Charles Dickens, they even manage to do this in a fairly entertaining way. The underlying CPU features and their vulnerabilities to side-channel attacks are explained drawing comparisons to real-world issues and using very simple code examples.
This should make it easy to understand the attacks, even for people with minimal knowledge about microarchitectures. Finally, a classification of the vulnerabilities and their defenses is presented, also demonstrating a proof-of-concept of exploiting the L1 Terminal Fault (L1TF) variant to read host memory from within a VirtualBox VM on a fully patched Ubuntu system.
https://www.youtube.com/watch?v=r5wtQBpRFsM
SiliVaccine: North Korea’s Weapon of Mass Detection
The Talk SiliVaccine by Mark Lechtik from Checkpoint focused on North Korea’s national Anti-Virus solution. He presented on his approach of the analysis of the Anti-Virus solution. It showed that there are SPOILER: “some” similarities between SilliVaccine and a very outdated version of TrendMicro’s scanning engine 😉 as well as some entertaining vulnerabilities bound to this fact. Moreover, Mark showed how SilliVaccine choose their encryption key as shown below:
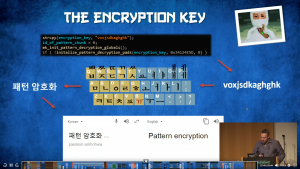
SilliVaccine encyption keyGoing from the technical details to the actual creators of the software, Mark discovered some connections between Japanese companies and North Korean companies while digging deeper. Pretty exciting facts he was able to identify…go and watch the recording, it is worth it!
See the Talk below or download it HERE:
https://www.youtube.com/watch?v=7xcLAiWQm9Y
I think this talk is a nice addition to the already conducted research about Democratic Republic of North Korea devices and own software by @0x79 and @_takeshix and shows DPRK’s approach to deal with Software, devices, and surveillance. There are also some similarities between the RedStar OS research and SilliVaccine which may be covered in a follow-up blog post, so stay tuned. You can find the previous research results focusing on RedStar OS and North Korea’s surveillance technologies in general below:
Also see:
https://www.ernw.de/download/exploring_north_koreas_survelliance_technology_troopers17.pdf
https://www.dprktech.info/post/exploring-north-koreas-surveillance-technology/
https://media.ccc.de/v/32c3-7174-lifting_the_fog_on_red_star_os
All Your Gesundheitsakten Are Belongs To Us
In this talk, Mr. Tschirsich showed examples of vulnerable patient health records and interesting attacks that often lead to tremendous exposure of sensitive health data. He explained the negligent decisions that render online platforms and apps of private providers in the field of health and telemedicine vulnerable. The applications recently have gone live for a large customer base and are supported by large health insurers which serve millions of patients. He motivated for a debate about future developments of the electronic health record and telematics facing recent efforts for the digitization of health care in Germany by the Secretary of Health Jens Spahn.
Though, he expressed misleading statements on telematics and the electronic health record (ePA) I want to make a few remarks regarding this. He mixes the offered health records by private companies with the unrelated “official” ePA by the gematik. The health records he examined are covered by §68 SGB V, which basically says that health insurers are allowed to provide financial assistance for these solutions if patients want to use them. As security researchers, we need to be careful not to ignite public debates about future developments in healthcare. The field of application is too intimate and the problems too complex to drive the public discussion with hysteria. We should work on the solutions and give constructive advice to expert panels. Otherwise, we will quickly lose our credibility.
https://www.youtube.com/watch?v=82Hfh1AItiQ
The Ghost in the Machine
Anyone who knows Joscha Bach from previous talks already knows where this is going; the rest probably needs some context first:
This talk was part of a series of talks about, as described in the latest talk “How to get from computation to consciousness”:
[How to Build a Mind @ 30c3]
[From Computation to Consciousness @ 31c3]
[Computational Meta-Psychology @ 32c3]
[Machine Dreams @ 33c3]
[The Ghost in the Machine @ 35c3]
All of these talks deal with various topics surrounding philosophy of mind, artificial intelligence (or rather artificial consciousness to distinguish it from the AI and Machine learning hype of the recent years), computer science and mathematics. If you are interested in that kind of philosophical topics and have a background in mathematics or computer science, these talks are a great entry point to this field. I will focus on some key ideas that kept me thinking after the talk that can be illustrated with limited context and without in-depth explanations of other topics.
Some Terms
For the start some terms that are used and defined, according to Joscha’s models, early in the talk:
Intelligence: ability to make models
Which he distinguishes from:
smart: ability to reach your goals
wise: ability to pick the right goals
Mind: thing that observes a universe
self: identification with properties and purposes
consciousness: experience of what it’s like
mind body problem: How are mind and consciousness realized in the universe?
Human Intellect and Civilizational Intellect
This is only briefly brought up, but the idea is that concepts from an individual human intellect can be generalized, so they apply to civilizational intellect, resulting in the thesis that:
`culture` in a civilization is what the `self` is in an individual, i.e., the identification with what the entity(human or civilization) thinks it is and its goals.
`media` is the pendant to `consciousness`, i.e. the contents of attention that make knowledge available throughout the entity.
Local Compression of the Universe ( or its Global Modeling Function)
In case you don’t know about the Mandelbrot fractal yet, now is a really good time to watch this video which was also used in the talk to illustrate the topic. If you don’t know the underlying mathematics yet, this illustrates the point even better. Try finding some kind of description of the landscape you see in the video that approximates it, for example what shapes you can see (spirals, circles, etc) and how they interact (spirals meet annihilate sometimes). The rule set will capture some of the structure, but no matter how many rules are added, it will never fully account for the infinite complexity and depth of the fractal. This is what is meant with “local compression” in this case. This rule set is good enough to describe higher level concepts of this universe, but is not actually an accurate description of the universe.
The actual mathematical function to generate the Mandelbrot fractal is incredibly simple in comparison, either watch this Numberphile video for a friendly introduction or just read the Wikipedia article if the question “For which points on the complex plane does this iterative function diverge?” is something you understand already.
This Mandelbrot function is the global modeling function in this illustration.
A concept related to this is Kolmogorov Complexity.
The point is that we (as humanity) do not know what the global modeling function of our universe is and what we base our reality on is some local compression that works good enough. Even if we knew the global modeling function it would not necessarily help with anything humans typically do despite being potentially incredibly simple.
This and related ideas are then dealt with in great detail over the following part of the talk (e.g. neural networks as function approximators)
The Lebowski Theorem
This “theorem” is the idea that:
“no super-intelligent system is going to do anything that is harder than hacking its reward function”
e.g. how would one prevent a true AI that tries to maximize its reward function from blackmailing some human to just set the reward value in memory to MAX_INT, change the code that modifies it and kill anyone who tries to change it back.
This is already a problem in certain humans, i.e. monks who just meditate until they reach states that maximize (or possibly bypass) their reward function, while doing nothing that organisms are typically driven to do by their reward functions and ultimately being culled by natural selection.
Conclusion
Overall this was another great talk by Joscha Bach which I would highly recommend, though it will probably be easier to start with one of his earlier talks.
https://www.youtube.com/watch?v=e3K5UxWRRuY
Open Source Firmware – Eine Liebesgeschichte
Another talk at 35C3 was “Open Source Firmware – Eine Liebesgeschichte” translated “a love story” by zaolin. It wrapped up the state of open source firmware in 2018 very good and explained various questions like how things work, why things should be more open or that there is more than only one firmware on our mainboards and ow/where it is stored.
The talk shows some details how the x86 environment before the OS works and what we can do using coreboot and its components to gain more freedom.
It also shows that various vendors already ship open source firmware, like google with its chromeOS devices or Microsoft with its surface.
A good point of the talk was that it was not rather security or research focused, but rather a very explaining talk that gave a lot of overview over the state of open source firmware
on various platforms like risc-v, arm/arm64, ppc/OpenPower and x86. I recommend this talk to everyone who’d like to understand how things work before the OS or who’d like to get started doing own research.
Link to talk and info: https://media.ccc.de/v/35c3-9778-open_source_firmware
https://www.youtube.com/watch?v=HRmr7aeufTo
Last but not least we want to give you a curated list of talks that are worth having a look into:
Foundation talks:
https://media.ccc.de/v/35c3-9873-all_creatures_welcome
https://media.ccc.de/v/35c3-10011-hackerethik_-_eine_einfuhrung
Technical talks:
https://media.ccc.de/v/35c3-9498-dissecting_broadcom_bluetooth
https://media.ccc.de/v/35c3-9462-what_the_fax
https://media.ccc.de/v/35c3-9364-viva_la_vita_vida
https://media.ccc.de/v/35c3-9979-the_layman_s_guide_to_zero-day_engineering
https://media.ccc.de/v/35c3-9647-taming_the_chaos_can_we_build_systems_that_actually_work
Have a SAFE ‘n SECURE day,
your Troopers Team!