Back from Holidays, you started the year well motivated to make the world a safer place.
However, sitting at your desk today you realize nothing really changed since last year, and you are surfing the web, feeling a bit blue, trying to avoid that pile of emails waiting for you and wondering how you could gain some visibility on your domain in order to better defend it.
No worries, emails can wait a bit longer. All you need is some fresh air and something cool to keep your defensive mind motivated for the year, and I might have just what you need; so put on your shoes and let me take you on a 15 minute Cypher walk with a cool blue dog…
Using BloodHound for defensive purposes is not new. Wald0 and folks have been tinkering with it for a while and introduced the concept last year with the Active Directory Resiliency Methodology. But when talking with colleagues and customers, I see a growing interest for BloodHound usage outside of the “Red Teaming” context, and something tells me (or at least I hope) 2019 will be year of the blue dog…
In this post, and continuing where I left it in 2018, I would like to share some Cypher experiment with you.
I really love wald0’s idea of using the graph data to simulate hardening options and try to reduce the number of attack paths to known sensitive groups. However the workflow of creating a copy of the database for each hardening hypothesis and keeping track of these successive changes and associated branching can quickly get quite tricky (and a bit too complicated for ADD people like me), so I was wondering if there was a Cypher way to exclude specific nodes from queries without having to really remove them from the database…
To achieve this goal, we are going mark nodes as “Blacklisted” using labels, to then query paths excluding nodes labeled as such.
Adding a label to an existing node can be done by using the following Cypher:
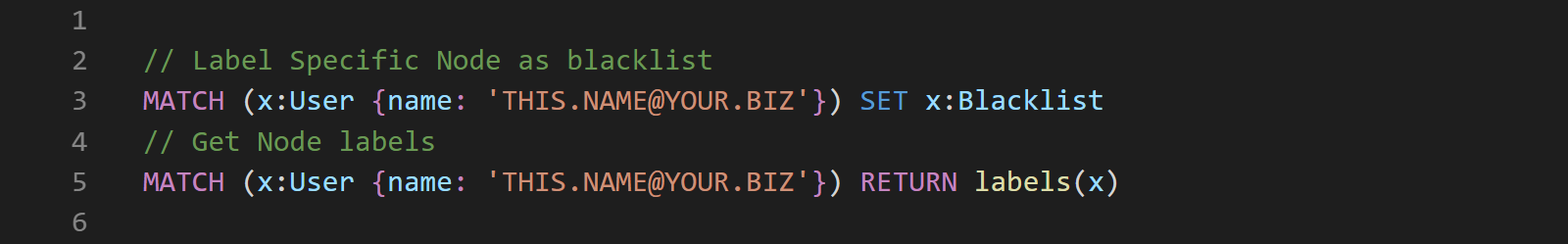
We can then check what nodes are excluded by running the following queries:
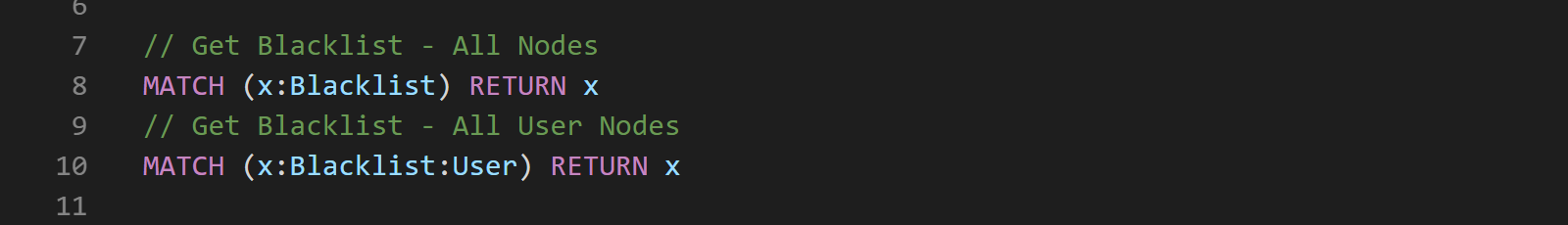
Removing label from nodes can be done with the following Cypher:
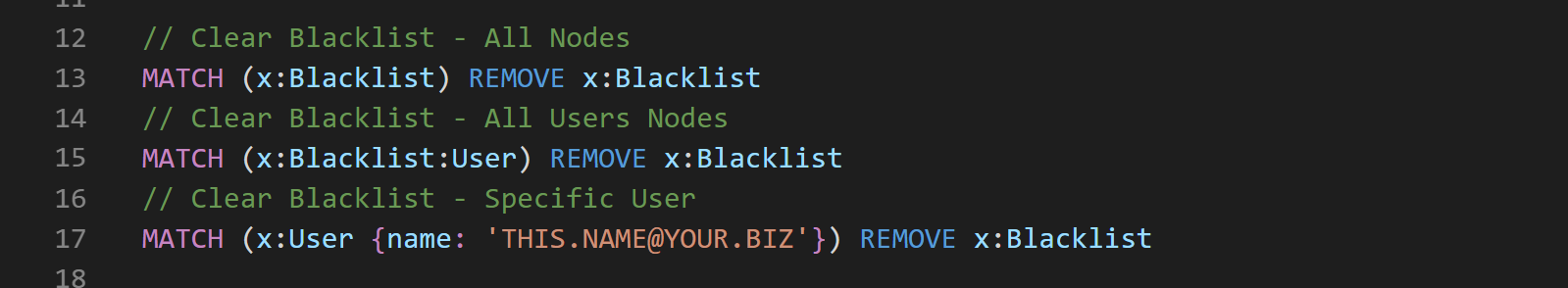
Ok, so we have all the basic commands we needed to manipulate our Blacklist…
Now all we need a path query that excludes blacklisted Nodes.
To mark our start nodes and end nodes, we are going to hijack the owned/highvalue features of the UI. This will give us a quick and easy way to mark start/end nodes and query our paths.
So let’s start with a regular path query from Owned Nodes to HighValue Nodes:
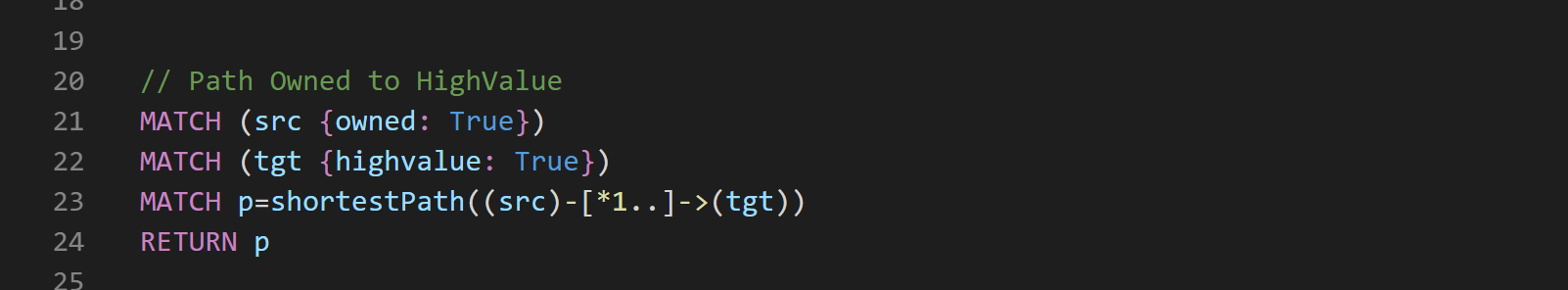
To exclude our Blacklist Nodes from this query, we can use the following syntax:
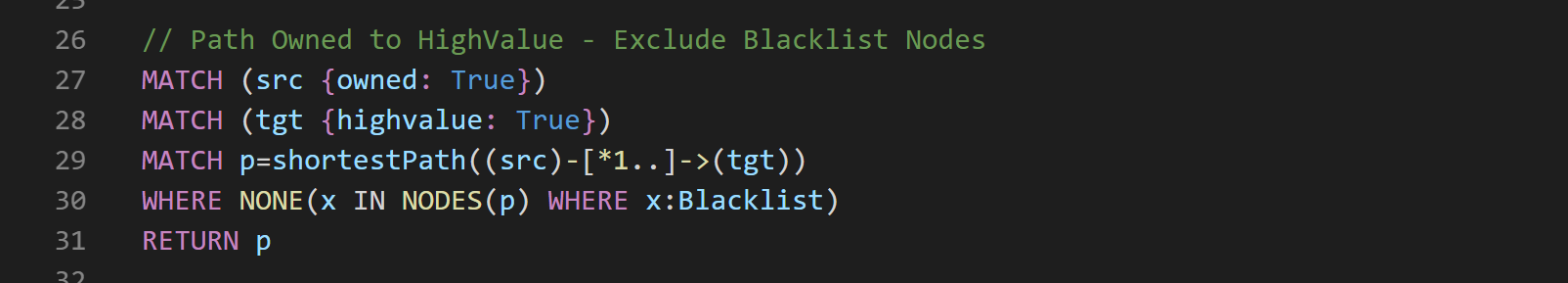
The added Cypher on line 30 allows us to look at each node on each path, and return only paths where none of these nodes are labeled as Blacklist.
First, using the NODES() function, we take all Nodes where label “Blacklist” is set and store them in a variable x.
Then, we filter paths where x is equal to nothing using the NONE() function after a WHERE clause.
Cypher syntax is really quite cool…
Now that we have all these Cypher queries, the last thing we could do to make our life easier, is tweak them a bit, format them in some obscure JSON, and add them to the BloodHound UI.
And since it is still holiday season, I have a little something for you…
You can paste this content into your Custom Queries and you should have something like this to tinker with… Hope you like.
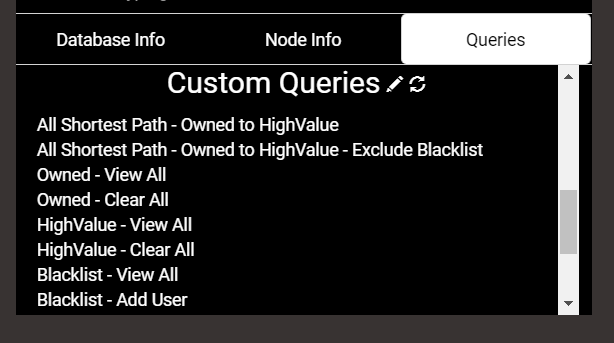
We can now mark start nodes [Owned] and end nodes [HighValue] via the graph, and manipulate the blacklist on the fly via the Query tab… Achievement Unlocked.
Bonus: the Edge filter functionality of the UI works with the two supplied allShortestPaths() queries. Awesome…
So that’s it for this post, I hope you found some useful bits in there, and that you now want to dig deeper into BloodHound and custom Cypher queries.
If that is the case (or if you are into Active directory Security in general), make sure to check out this year’s Trooper Conference. Loads of great people, awesome talks (if you like AD, check this out!!) and cool trainings, including an extended 2-day version of the BloodHound/Cypher training I gave last year for the ERNW AD Summit. (Make sure to book quickly if you are interested as there is a limited amount of seats available.)
I will be adding those features to the upcoming version of CypherDog that I will be presenting at Troopers (and at the PoSh Summit in Seattle) later this spring.
Cherry on the cake, @_Wald0 and @CptJesus will be at Troopers to present their latest defensive BloodHound work and @_Dirkjan (creator of ACLPwn) will also join the party. 2019, year of the blue dog… Don’t miss it…
In the meanwhile, hit me on Twitter or BloodHound slack if you have any questions or remarks.
Arrroooooooo & Best Wishes for the coming year.