This is part 1 of our report series on interesting talks of the 33rd Congress of the Chaos Computer Club. Every year the congress attracts hundreds (up to twelve thousand this year) of technical interested people with the opportunity to socialize and exchange knowledge with each other. The congress is organized by the European largest hacker association and speakers give talks about technical and societal issues like surveillance, privacy, freedom of information, data security and various more.
Talks in this part deal with CCC at schools, Wi-Fi security and the security of the N26 banking app.
‘Chaos macht Schule’
Talk by ‘benni’ and ‘Doriana’ | Video: German / English | Slides | 33c3-Talk-Schedule
“Chaos macht Schule” is a project from the Chaos Computer Club (CCC). Members from the CCC have been visiting education institutes for workshops for 10 years. The workshops deal with technical topics and data privacy and also with the aim to improve the pupils, parents and teacher’s media competence and technical understanding.
Motivation
Meanwhile new technologies are common for the society. People use it as a knowledge storage, an information source and as a communication platform too. The members of the CCC work with the Internet every day, therefore they consider it as their duty to inform interested parties about the options, risks and limits of the Internet.
Events with pupils
They try to establish basic technical knowledge together with the pupils. A lot of pupils use the digital media, but don’t understand the complex technical details. Therefore, they review more important social questions like:
- What is the privacy and where do they put an end to privacy?
- What is data privacy and why is it important?
- Who can I trust for example in social networks? Technology? Operators?
- Do I believe everything reported by the Internet?
Several basic schools request presentations about the architecture of the Internet. These questions will be clarified in those presentations. Another item on the agenda for example is a trip through the Internet. The pupils say which services they usually use. Thereby, they should try to explain for which reason they use those services. The next step is to identify their benefits and disadvantages. The members of the CCC do not want to restrict the usage of dubious services for the children, but they rather want to clarify the risks, so that the children may rethink their behavior. If they further insist on using their services, the members try to show alternatives and give advice on how to behave on the Internet and show how to easily remember a safe password.
Events with parents
A lot of parents realize that they only can protect their children, if they have knowledge about the digital world themselves. So schools request CCC members as competent experts to visit their parent evenings and to educate parents about the digital world. Contentual the parent evenings and the pupil events are the same but it should be noted that parents have additional parenting problems:
- When should children be allowed to use the computer or the Internet?
- Where should the computer be placed and which software should be allowed?
- Why are children interested in video games and which do they play?
- How can parents approach and speak with their child about this topic?
Usually the event contains a presentation about the daily digital life of their children. Also, the members of the CCC try to explain parents what their pupils are fascinated by.
Personal opinion
In my opinion, it’s a very good idea to educate pupils as well as parents about the Internet. Nowadays, the Internet is a controversal topic and we have to know how the Internet works and we should also know what we do when we use it.
Julie
Other Links
‘Shut Up and Take My Money’
Talk by Vincent Haupert | Video: German / English | Slides | 33c3-Talk-Schedule
The talk by Vincent Haupert, who is a security researcher and PhD student, dealt with the N26 mobile banking app.
The N26 app provides the functionality to manage a banking account without the need of anything else other than a smartphone. Security is enforced by pairing exactly one phone with the banking account. The speaker first described the architecture behind the system and after that he pointed out its vulnerabilities. The speaker focused on logic flaws and authentication as he never mentioned any different types of attacks. His vulnerability findings were commonly known flaws for these kinds of application. He showed “Spearphishing”, mentioned the missing certificate pinning, could brute force tokens and illustrated that there is no need to possess the paired phone for transactions. The researcher connected these flaws in an interesting way.
Connecting these flaws made it possible to completely compromise victims and take over their bank accounts instantly. Responses of the server often contained information, which was never displayed to the user. This information was used to exploit the unpairing step, support call, reset password and more.
Another interesting topic was the automation of money transactions, as N26 advertised to implement intelligent algorithms that are capable of detecting unusual behavior. The security researcher sent 2000 transactions within 30 minutes. Three weeks later N26 sent out an email concerning this high amount of transactions, not to the catalyst, but to the recipient, which is part of the problem.
The speaker contacted N26 with the CCC as intermediary. N26 support was glad, that he revealed these flaws and they all seem to be fixed by now.
I hope you enjoyed this short summary. This talk was not only informational as it comprised security research, the speaker also did a great job at entertaining the crowd, so it is definitely worth having a look at.
Tom
Other Links
‘Predicting and Abusing WPA2/802.11 Group Keys’
Talk by Mathy Vanhoef | Video: German / English | Slides | 33c3-Talk-Schedule
Dear readers,
There has been an interesting piece of research on the security of WPA2 Group Keys on this year’s Chaos Communication Congress. Mathy Vanhoef, the author of named 33C3 talk, states that research regarding Wi-Fi mainly focused on the security of pre-shared passphrases and session keys so far. This motivated some further research on other less common topics that might compromise WPA2 security as well.
As broadcast traffic is less frequent in contrast to unicast traffic, the mechanisms ensuring the integrity and confidentiality of former are a good place to start investigation.
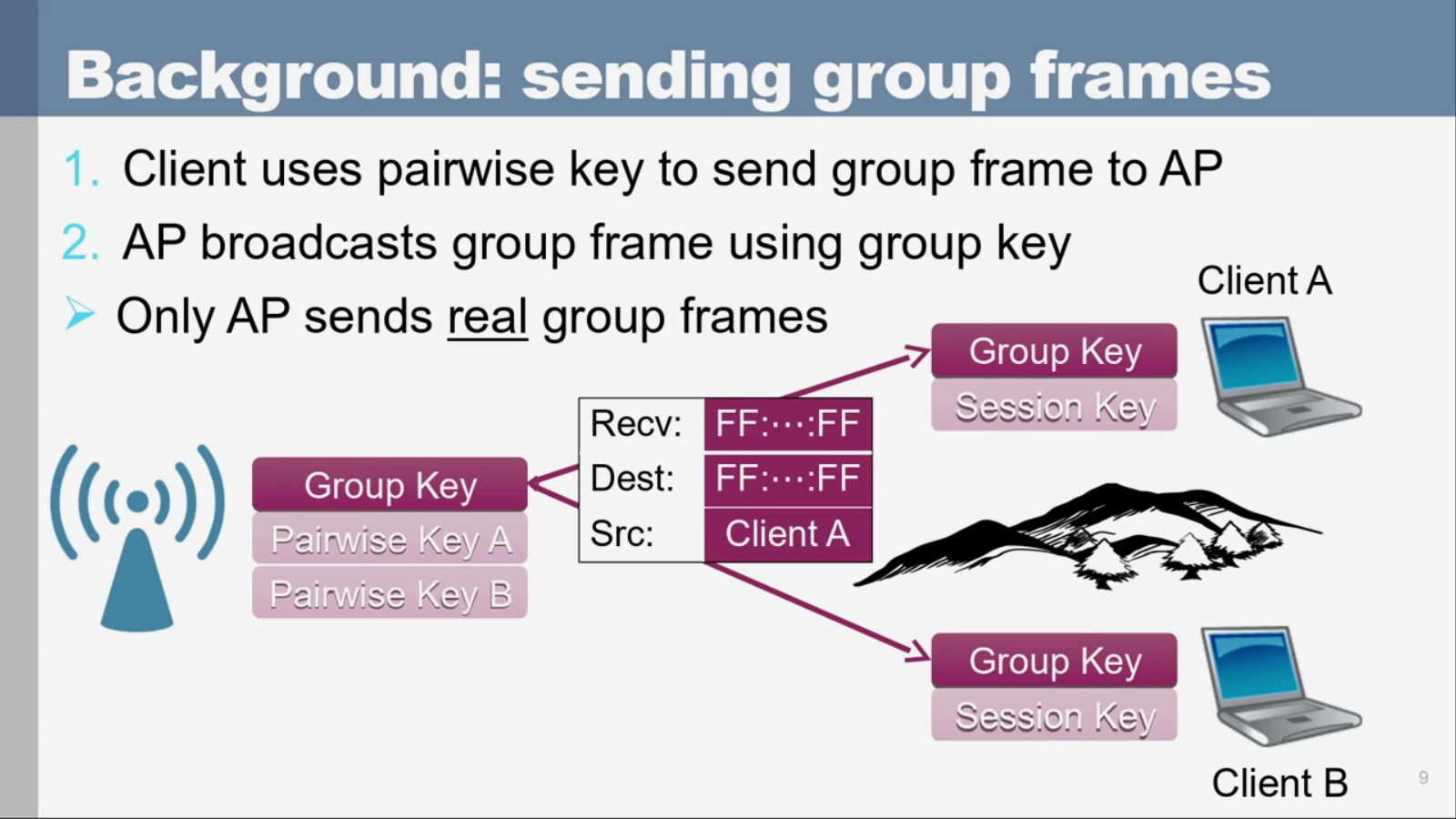 (Picture stolen from Mathy’s presentation)
(Picture stolen from Mathy’s presentation)
So if client A wants to broadcast, it will send the frame to the access point encrypted with its individual session key pair. Then the access point sends the real broadcast using the group key instead, which is shared among all clients.
The weak point Mathy Vanhoef examines in his talk is the group key. It is generated by feeding a public counter value and a private random key into a hash function. The problem here is the source of entropy as the reference implementation for the random number generator is quite vague at some point and it is inconsistent about how secure the implementation actually is. Sources of entropy are traffic on the network as well as clock jitter. As the private random key is generated during boot time some implementations lack enough entropy and the random key varies only little.
In fact, Mathy Vanhoef states that in his particular case (RT-AC51U, a Mediatek device) the “random number” which secures the group key resided within a few hundred possibilities. Once the attacker correctly guesses the group key, broadcast traffic can be decrypted and unicast frames can be forged. Although many clients implement simple countermeasures and reject unicast packages on broadcast frames, Mathy Vanhoef found a trick to let the access point forward the traffic for an attacker.
TL;DR
Alongside the known classical vulnerabilities such as the use of WEP or the use of pre-shared passphrases printed on the device that derive from its MAC address, people using WPA2 cannot necessarily feel safe:
Some Vendors implement flawed random number generators because of a badly chosen example for the reference implementation. Therefore, Wi-Fi group keys generated by that randomness can be estimated. The following vulnerabilities arise: the access point can be used to inject unicast IP packages and all traffic to the access point can be decrypted by ARP-poisoning the network to let all traffic be sent to the broadcast.
Mathy Vanhoef suggests to simply use the background noise generated by other Wi-Fi networks nearby to collect more entropy if kernel methods like /dev/random on Linux are not available.
So again, IT failed at security because we try to generate randomness with mostly deterministic machines 😉
Happy to share this great talk with you,
Luis
Other Links
- Research Paper by Mathy Vanhoef