As you have probably already recognized, some of us here at ERNW are doing research in the area of smart home technologies e.g. KNX. Recently, we took a deeper look into a device which is used to control a smart home system produced by the vendor BAB TECHNOLOGIE GmbH called “eibPort”. This device can be used to control smart home systems based on different technologies e.g. EnoCean or KNX depending on the version of the device. The eibPort comes with a visualization running on a webserver to control the whole system e.g. open or close windows, changing the temperature in different rooms or turning the alarm system on or off by simply clicking on symbols. The following screenshots illustrate an example of such a visualization:

Source: http://dmz.bab-tec.de:8083/cubevision/CVMTablet.html
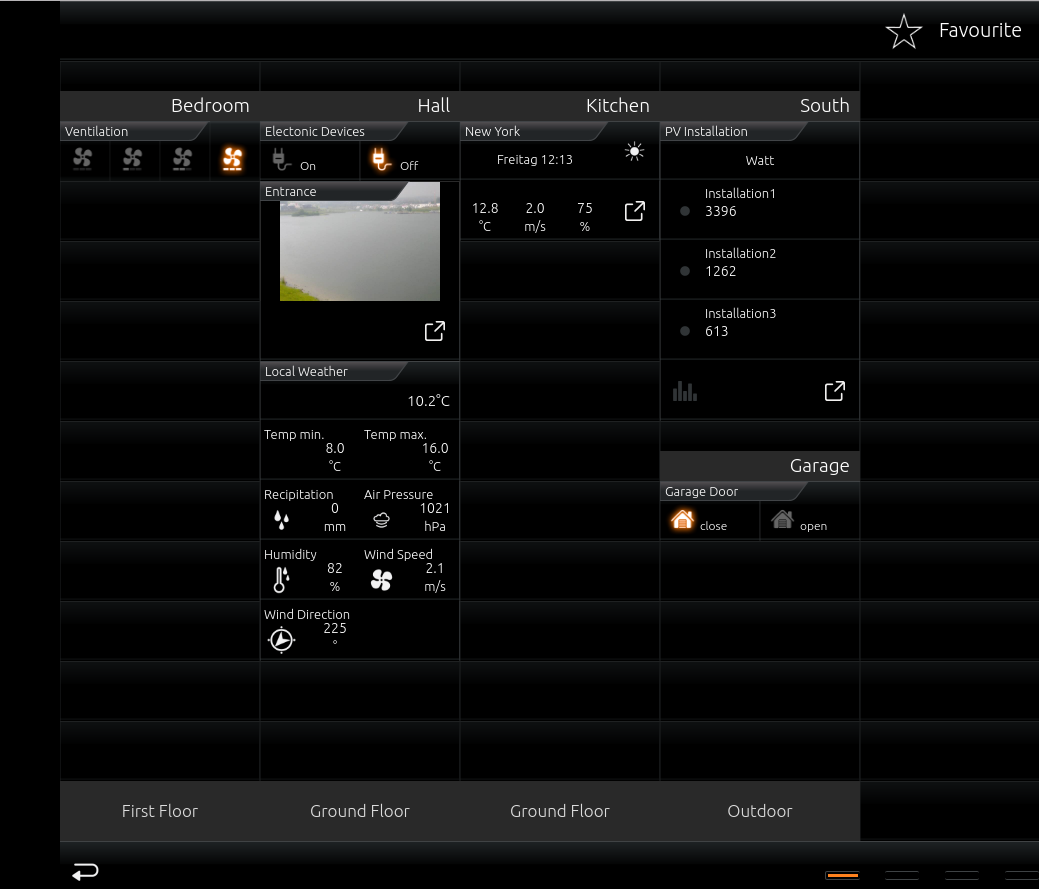
Source: http://dmz.bab-tec.de:8083/cubevision/CVMTablet.html
Therefore, the eibPort represents the central part of the system. With this fact security should play a major role regarding all software components which come with the eibPort. Nevertheless, there are a few vulnerabilities which will be covered in this blog post.
Analyzing the UpdateTool
Different from other embedded device solutions, BAB TECHNOLOGIE GmbH decided to update the devices by a separate update tool which is simply a Java Jar file. This method is pretty interesting as the update process itself differs from other solutions. Normally, updates are installed by entering the web application and provide a single file which stores all the relevant update data. This way the update file will be provided to the UpdateTool and in a further step the update tool transfers the data to the device. Taking a look on the UpdateTool could therefore be very interesting.
As soon as the Update Tool is started, it searches for eibPort devices which are in the same network. If an eibPort was found, information about the device will be displayed e.g. the IP address, serial number, installed firmware version as well as different ports.
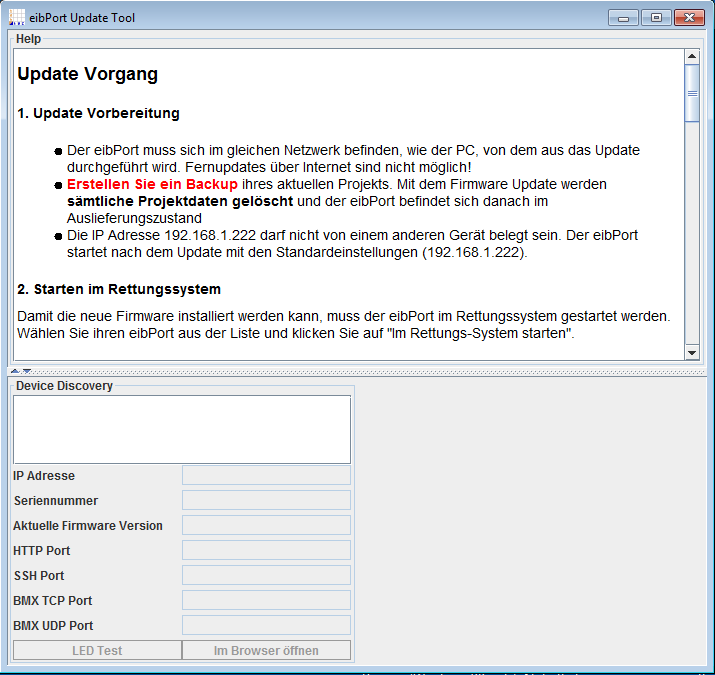
Because of this reason we took a look at the source code of the Update Tool which isn’t very complicated. If you compile Java code it will be transferred in an intermediate form, JVM bytecode, that retains a large amount of the information contained in the original Java code. This fact makes it very easy to decompile the Java code in this case the .class files which are included in the Jar file.
Source Code of Update Tool
Right after opening the file “UpdateTool-20141219.jar” with a Java decompiler, we can see the code structure e.g. the included packages within the Update Tool.
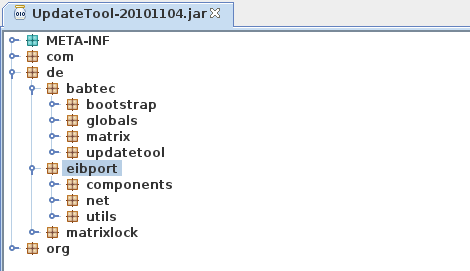
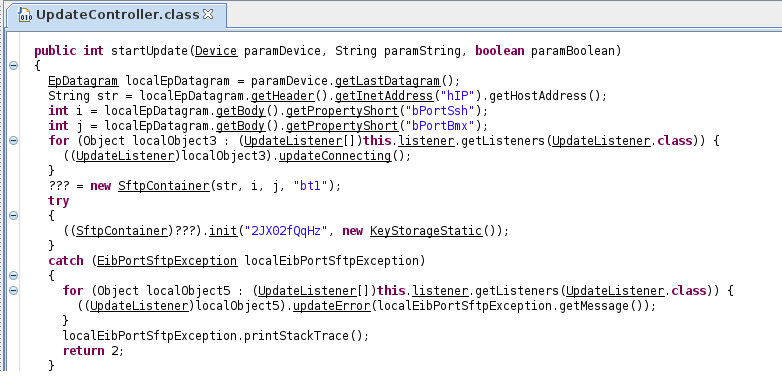
There are two packages which look interesting called “babtec” and “eibport”. After some time of analyzing the source code and the relations between different classes and methods we found an encrypted DSA Private Key in the class “KeyStorageStatic”.
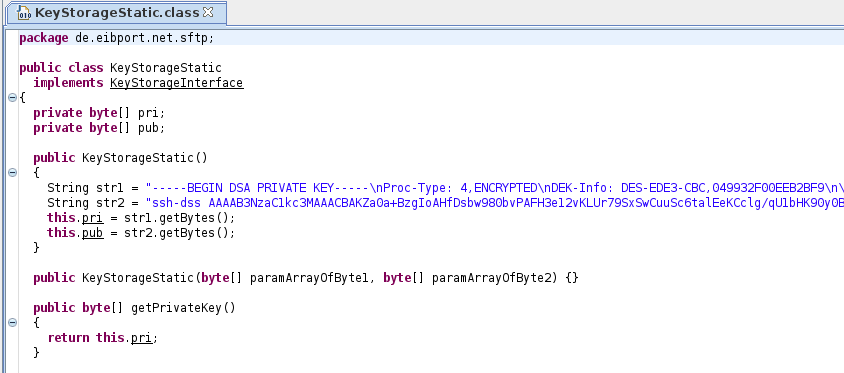
This key will be used in the method “startUpdate” as well as “getRescueVersion” to connect to the eibPort with the user “bt1”. The fact that this DSA private key is encrypted but will be used in another class to connect to the device indicates that there must also be the encryption key to decrypt it. Another option would be that a passphrase must be entered to unlock the key if the Update Tools wants to connect to the eibPort, but this isn’t the case. After some further research we found a String which fit into the context of the DSA private key and looks like a passphrase. This string is located in the class “UpdateController” which is shown in the following figure:
Connect to EibPort
With the gathered information we can try to connect via SFTP to the device. At this point we have the username, the encrypted DSA Private Key as well as the passphrase for unlocking the key.
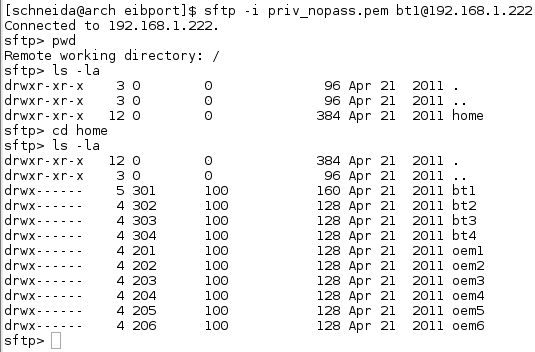
As you can see in the screenshot above, it works but we are in a chroot environment which is under “/config/chroot/”.
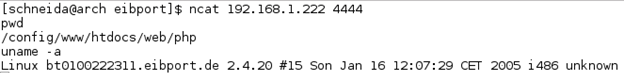
Nevertheless, for getting a shell with more capabilities we can now upload a PHP shell as the system is running PHP in version “4.3.1” which is stated in the HTTP response header X-Powered-By. If a PHP file is uploaded to the home directory of the bt1 user, the file will be accessible via the web browser.
As soon as the webshell is uploaded you have gained root privileges on the device. The reason for that is, that the webserver is running with root privileges and therefore also the uploaded PHP script. At this point you have full control over the device and can control the smart home system as well. Lights and power sockets can be controlled, windows or doors can be opened or even alarm systems can be turned off.
In a further step we took a look at the web application itself and which functionalities are provided. We detected a PHP script which looks pretty interesting as it is extracting data. The script receives two values via the GET parameters “src” and “dst”. These two parameters are processed as follows:
“exec(“unzip ../..”.$src.” -d ../..”.$dst);”
Both parameters aren’t checked for malicious input and straight handled over to the method exec and used for the unzip command. This way of handling untrusted user input implements a further remote code execution. It is possible to easily break out of the context of the actual unzip command and execute other OS commands, again with root privileges.
Conclusion
Smart home devices like the eibPort are an essential part of smart home installations. People want to be able to control their home from everywhere but at the same time they are not aware of the potential consequences which are implied with their requirement.
These devices can be found very easily via a Google search or by writing a short Python script which crawls for specific paths. If you know the structure of the web application which comes on the eibPort you can find hundreds of them available on the Internet for everybody, some of them even without any authentication mechanism activated.
BAB TECHNOLOGIE GmbH provides an update for the affected eibPort version (2.1). Users of the eibPort 2.1 should update their device as fast as possible and follow the recommendations provided by BAB TECHNOLOGIE. The update can be found here.
Timeline:
- 17.06.2016 First call to get contact e-mail address
- 21.06.2016 Information about the vulnerabilities was provided to the vendor
- 07.07.2016 Asking if everything is clear or if additional information is required
- 01.08.2016 Received a preview of customer information regarding the security issues and planned update
- 02.08.2016 Sent additional information to the vendor to support our opinion that not all vulnerabilities will be fixed with their planned update
- 04.08.2016 Vendor decided to delay the planned update for the eibPort
- 07.09.2016 Asking if everything is clear or if additional information is required
- 08.09.2016 Release of Firmware Update for eibPort V2.1 by Bab-Tec (v0.11.8)
Cheers
Dominik