Welcome to Brazil!
“Welcome to Brazil”, I think, turned to being the most used statement during the past Hackers to Hackers Conference in Sao Paulo. It was used as the main reaction to every speech taking moment, and there were a lot of those! To honor the moments and give you a quick insight into was what going on in Sao Paulo, here is a quick summary of the overall event and our own contribution.
To keep it in chronological order, the weekend started on Friday at the House of Learning, which was this year’s location for Sacicon. Sacicon is a sweet little invite only conference with just a few people. It actually is the only Brazilian IT-Security conference, which is completely held in English. This year’s speakers included Bryan Fite, PaX Team, Gabriel Barbossa and Hendrik and me.
Here Hendrik and I held a short talk on cellular networks, their vulnerabilities and a few things we learned from running our own GSM network at TROOPERS. The talk was admittedly tributed to one of our TROOPERS attendees, who was not amused, when he entered the venue and his phone (due to being foreign and in roaming state) jumped into the TROOPERS network. When he received the welcome text message, well, he prefers the airplane mode now! So greetings in his direction from here: Thanks for the inspiration for the talk.
Sacicon offers a very familiar atmosphere and so the talks included some interesting details and resulted in various discussions. In summary – just great!
Big thanks to the guys from the House of Learning!
Saturday
Then on Saturday, the first day of the conference, we were yet again surrounded by the many friends we made during last year’s H2HC and other conferences. The line of speakers, which included PaX Team, Ilfak Guilfanov and Vladimir Wolstencroft resulted in a great set of highly interesting talks. Most of the held talks were recorded and should be published beginning of 2016 (probably!). As always H2HC was accompanied by the H2HC University, which is a set of workshops for beginners and proficient people on various topics of IT security. Seems they also had a great line up!
Hendrik and I had also joined the line of H2HC speakers to present on some of our experience in the field of physical access and hardware hacking. The talk contained an overview of interfaces which are usually contained in all devices, but are often forgotten or not accounted for. For the talk we sorted these interfaces into three categories: “Maintenance”, “Service”, “Fallback” and “Internal Communication”. Here Maintenance summarizes the interfaces, which are used by service engineers, field technicians and sometimes even Admins for setting up or configuring the device. Service, although it’s probably a badly selected term, summarizes the interfaces, which will be used for debugging/fixing, when a device is sent back to the manufacturer. Fallback interfaces are, well, used when something has gone wrong and access needs to be kept available. And last, but not least, Internal Communication was a selection of interface which are necessary for a device to work (like the wires between a memory chip and a controller).
Using these groups and a few random examples like smart phones, thin clients and also the eNodeB from our telco lab, we showed that are large amount of hardware out there is vulnerable to very simple attacks. As the eNodeB is kind of an intersection between Hendrik’s (telco) and my (hardware) some focus went into this topic. Here we showed how helpful it is, when connectors on a devices PCB are actually marked as being serial or JTAG interfaces. Or when the device’s firmware is stored on a removable Compact Flash card directly on the center of the main PCB. Or when the device contains a maintenance interface with hardcoded credentials. Or when the device has a configuration tool, which you can’t run because it’s only compatible with JAVA 1.5 running on a Win XP / 2000. Or when…I guess you get the point. As such the eNodeB resulted in being a great case study, with vulnerabilities in all mentioned categories.
The talk ended with a very simple conclusion, very many devices out there can be easily attacked, by using $20 worth of tools and little experience. Some of this results from the reuse of old components, some from needing accessibility in case of errors and very very much from the fact that chips need to be able to talk to each other for a device to work. Sadly, a few of these flaws can only be patched up by obscurity Make sure that the attacker will break the device rather than extract data.
To keep it simple, do not put too much trust into your everyday electronic devices and give hardware hacking a try!
Directly after our talk, followed a small workshop on the H2HC 2015 electronic badge, of which I had the honor to design it. Having enjoyed H2HC in 2014 and being in regular contact with Rodrigo, we had worked out to give an electronic badge for the 2015 edition a try. And this is the result:
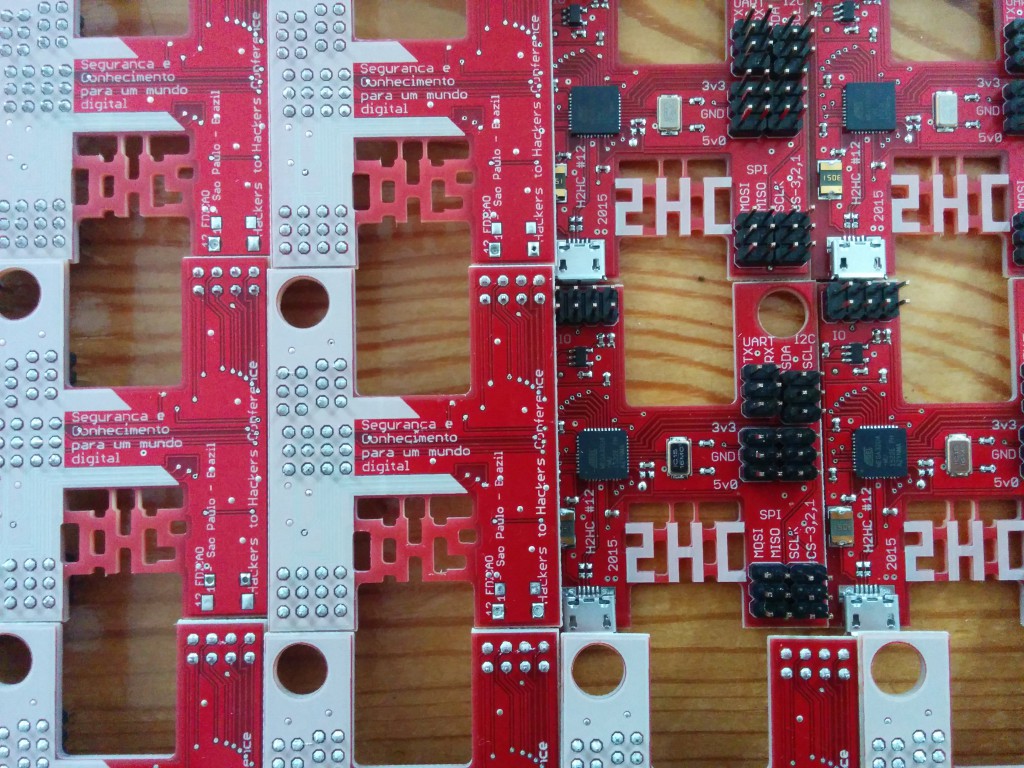
The badge is basically an Arduino Leonardo in a customized design. Using the same ATMega32U4 the badge offers 28kb of flash memory (the chip has 32kb, but 4 are used by the bootloader) and a straightforward way of programming it via USB. Using Arduino Studio as a source for libraries and for writing the code, the badge is great for small hardware projects and for the first (and sophisticated) attacks on any kind of hardware. To offer a quick start, the badge has multiple IO pins and duplicate headers for SPI, UART and I²C. Having duplicate headers offers the opportunity to not only connect the target device but also scopes or logic analyzers for debugging.
The workshop on the badge was something like a quick start guide, presenting options, functions and a few little ideas. For me, personally, the Arduino is a very helpful little gadget, which offers an easy start for beginners and can also be a mighty tool for practical penetration tests and demonstrations. At some point one will always have to start creating her own tools. So why not start directly from scratch and get a feeling for the overall approach?
Sunday
Sunday morning, the second and last day of H2HC, we had everything up and running for a round of Packet Wars in cooperation with Bryan Fite. A shiny Mac Mini connected to a little Cisco AP were both ready to play a game of “Hiding from Robots”. Although the setup had already shown a few weaknesses at DayCon IX, we decided to give it a shot. Hendrik and Bryan helped all combatants getting connected to the network, while I walked off to a group of university students who had been invited to join the hacking. As all seats for the actual contest were already taken, we decided to give a quick and simple hacking crash course.
As such I gave a quick introduction to the Metasploitable VM and got the guys going, while Hendrik supported the Packet Wars session. Luckily I had some support with the students, as the game would turn a little bit ugly.
While Packet Wars was aimed at being a challenge for the combatants, also we as organizers had a few battles of our own to fight. Directly during the first round various network and connection problems appeared. One of the teams, Team 3, had large problems staying on the network. These problems got so bad, that they kind of quit the game during the first round.
From what we’ve seen the problems resulted from three different anomalies:
- The access point seemingly crashed two or three times under the load.
- The SSID of Team 3 was completely missing at certain points and our RF-spectrum analyzer showed some strange peaks. It seems somebody was nicely jamming their frequency.
- Throughout the game, there were multiple de-authentication attacks against the WiFi clients. These seem to have been coming from more than one party.
As RF is a pig, it was sadly not possible to identify the exact source of the attacks and stop them. Still, even though the attacks did not stop, the teams seemed to just stay motivated to finish the game until about the middle of the third round. And while we felt sorry for everybody who could not properly use the infrastructure it seems the attendees still enjoyed themselves a lot.
Packet Wars ended with a ironic result, while Team 1 had a safe first place, the kicked out Team 3 had still made it to third place even though only playing for several minutes (effective playing time). So Maybe somebody was scared of them?
Eventually – Lessons learned:
- RF jamming is easily detected and can be traced while it’s running (the own body is great for creating a directional antenna effect)
- Brazilian’s hate WiFi and try to kill it where they can
- It’s simply impossible to identify the source of de-authentication packets in a small confined space.
- Next year: cables! 😉
- Seems the rivalry went slightly sour:
http://techviral.com/2015-11-10-brazilian-server-hacked-7000-leaked/
http://www.zdnet.com/article/brazilian-army-gets-hacked/ - We will be back!
All in all we had a real great time at H2HC. We learned a lot, got to know many great new people (greetings to all of you) and as much as we’d love to return last year, we’d also recommend it to you.
To finally end this post: Big thanks to Rodrigo, Balestra and all their staff and helpers for making us feel home and running a great conference! Hope to see some of you at TROOPERS 2016 or eventually at the next H2HC.
Hendrik & Brian
P.S.
A few random notes on questions we were asked:
- Sniffing GSM networks
- Sniffing with Nokia
- GSM Bastestation –
- Checking for jamming attacks: HackRF One + PortaPack
- Hacking VM