In our talks in the past we showed what might be possible if an attacker gets access to backhaul and/or core network of a telecommunication provider. In a security analysts perspective this is really disgusting, but provider always will argument that those attack scenarios are not realistic.
Because of legal restrictions we are not able to demonstrate this in practice (e.g. by breaking in into a BTS environment somewhere in the woods) but what we can do is this: building a lab.
Sometimes it is really shocking what you can buy on Ebay, right? Here we got one very interesting component: a Huawei BBU3900 BaseStation which is used by a couple of providers. Okay, it is for GSM-Rail, but the technology behind is very equal. And for 100 dollars (plus shipping) you don’t ask further questions…
Some weeks later the BaseStation arrived from the US. The first obstacle was finding out a working power supply because it needs an industrial power power supply of minus 48 Volts. After some more hours spent on Ebay, we even got this working. It took some while but now we have our Lab running, even if it is looking a bit improvisational.
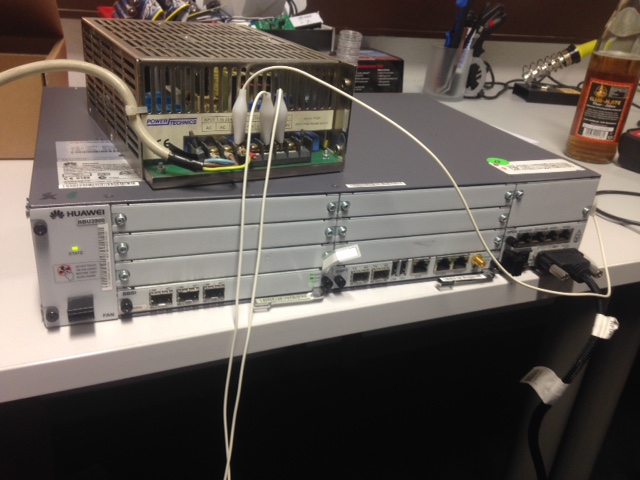
Once having the lab working it was very easy to get access to the BTS, even if we did not know the configuration and/or password from the previous configuration. There are a couple of services running on the machine like:
- WebGUI (it should be mentioned that there is no HTTPS supported
- TFTP
- local maintenance
- remote maintenance
- MML CLI
Interesting is that as OS VXWorks is used and Huawei is providing an own Web interface as well as CLI, using so called MML commands. But the most obvious one to get access is, of course, Telnet:
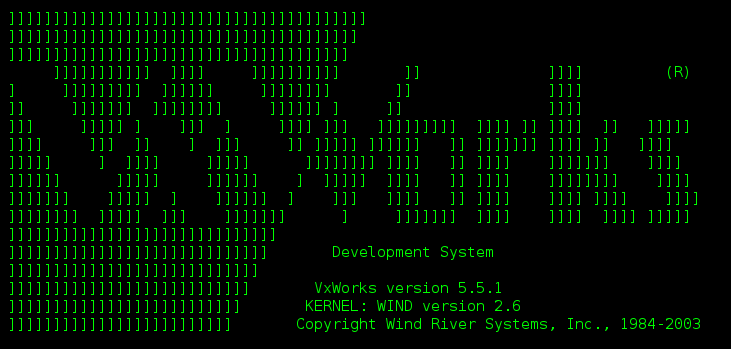
However, we now have a new and very interesting lab and we will keep you posted with new demos and maybe some new talks.
-Hendrik-
will be ordering one shortly and following along 🙂
thanx