This is a guest post from Fernando Gont.
On March 16th, 2015, at the Troopers IPv6 Security Summit, we finally released the SI6 Networks’ IPv6 Toolkit v2.0 (Guille). The aforementioned release is now available at the SI6 IPv6 Toolkit homepage. It is the result of over a year of work, and includes improvements in the following areas:
- Increased portability
- Bug fixes
- Additional features in existing tools
- Brand-new tools
Increased Portability
One of the goals that the SI6 Toolkit had since its inception is that of portability. The SI6 Toolkit has supported all major BSD-derived OSes, Linux, and Mac OS for a number of years now. And this new release supports yet another new platform: OpenSolaris. We believe that besides supporting a greater user base, increased portability ultimately results in improved code quality.
Bug Fixes
No matter the effort, computer programs has bugs. This new version of the toolkit fixes a number of bugs that were present in previous versions, thus leading to improved reliability.
Additional Features in Existing Tools
This new release of the toolkit includes some new features in existing tools. For example, our scan6 tool now supports heuristic address scans: that is, given an IPv6 address or domain name, scan6 can now automatically infer the address pattern employed at the target site, and target only addressings following such patterns. Triggering the use of heuristic address scans is very simple, just specify a target IPv6 address or target domain with a prefix notation, as follows:
scan6 -v -d www.example.com/64
or
scan6 -v -d 2001:db8::1/64
Additionally, scan6 now includes TCP and UDP port scanning support. For example, the following command:
# scan6 -d 2001:db8::1 –port-scan tcp:1-1024 –tcp-scan-type syn -v
will cause scan6 to perform a SYN scan of the TCP port range 1-1024.
Another tool that has incorporated new features is our tcp6 tool: it now supports the “–open-mode” and “–close-mode” options. These two option control the connection-establishment and the connection-termination phases. The “–open-mode” option mode option supports the following arguments:
- active: Perform an active open (i.e., initiate the three-way handshake)
- passive: Perform a passive open (listen to incoming SYN segments)
- simultaneous: Force a “simultaneous open” scenario
- abort: Reject incoming connections with a RST segment
This means that one can control the specific state(s) that a TCP connection will transition during the connection-establishment phase. However, from a security standpoint, it is typically more interesting t control the connection-termination phase. The “–close-mode” option, which controls such phase, supports the following arguments:
- simultaneous: Force a s”simultaneous close” scenario (crossing FINs)
- passive: Perform a passive close (wait for the other end to initiate connection-termination phase)
- active: Perform an active close (start the connection-termination phase)
- abort: Reset the connection
- FIN-WAIT-1: Cause the remote TCP to enter the FIN-WAIT-1 state
- FIN-WAIT-2: Cause the remote TCP to enter the FIN-WAIT-2 state
- LAST-ACK: Cause the remote TCP to enter the LAST-ACK state
The aforementioned arguments can cause a TCP connection to transition to/through specific states of the connection-termination phase. What makes this particularly interesting for an attacker is that some TCP states typically have no controlling process, and therefore in the face of a connection-flooding attack, the only place (if any) where these attacks can be mitigated is at TCP level (typically the kernel). For example, if a node is flooded with connections in the ESTABLISHED state, the corresponding application might enforce limits on the number of TCP connections per IPv6 address or per /64 prefix. On the other hand, if the same node is flooded with connections in the FIN-WAIT-2 state, it is typically only the kernel that can mitigate such an attack.
As an example, a target can be flooded with connections in the ESTABLISHED state as follows:
# tcp6 -i IFACE -s SRCPREF -d TARGET -a DSTPORT -L -l –flood-sources N -z 1 –tcp-flags auto -v
where
- IFACE: Network Interface Card to be employed for the attack
- SRCPREF: Prefix from which IPv6 addresses will be forged (e.g., 2001:db8::/64)
- TARGET: IPv6 address or domain name of the target system
- DSTPORT: Target port
- N: number of TCP connections per second that tcp6 will establish
tcp6 can be instructed to flood a target with connections in the FIN-WAIT-2 state by employing the same command, wth the addition of a “–close-mode” option, as follows:
# tcp6 -i IFACE -s SRCPREF -d TARGET -a DSTPORT -L -l –flood-sources N -z 1 –tcp-flags auto -v –close-mode last-ack
Finally, tcp6 now supports the “–data” command, which can be employed to easily specify a TCP payload. For example, tcp6 can now be employed to perform a Netkill (please see <>) attack as follows:
# tcp6 -i IFACE -d TARGET -a 80 -L -s SRCPREF -l -z 1 –flood-sources N –window-mode close –tcp-flags auto -v –data “GET / HTTP/1.0\r\n\r\n”
This command will essentially flood the target with TCP connections, send an HTTP GET request to the target, and immediately close the TCP window, with the goal of exhausting not only file descriptors and/or available slots (TCBs) for TCP connections, but also the kernel memory employed for the TCP send buffer.
The flexibility of our tcp6 tool allows for the implementation of virtually all known TCP-based attacks (please see this document for further information regarding TCP-based attacks).
New tools
A key tool had been missing in the toolbox of the IPv6 practitioner: an IPv6-based traceroute tool with full support of IPv6 Extension Headers. The new tool path6 implements traceroute-like functionally with full IPv6 support, in addition to support of a variety of probe types (ICMP6 Echo Requests, UDP datagrams, TCP segments, etc.). For example, path6 can be instructed to trace the route to www.si6networks.com with IPv6 packets employing a Destination Options header of 8 bytes as follows:
# path6 -u 8 -d www.si6networks.com
Part of the work that has been performed over the last few years in the area of IPv6 extension headers has lead to the publication of statistics regarding the extent to which packets with IPv6 Extension Headers are dropped when communicating with public servers (please see this IETF Internet-Draft). The script6 tool implements all the functionality required to produce the results published in the aforementioned IETF Internet-Draft.
Namely, it implements the following commands:
- get-alexa-domains: Extracts the domain names from Alexa’s Top-1M web sites
- get-mx, get-ns, get-aaaa: Obtain MX records, NS records, and AAAA records for a domain name, respectively
- get-trace: measures packet drops when communicating with a specific target employing IPv6 Extension Headers
- get-trace-results: Produces statistics based on the results of “script6 get-trace”
Appendix A of the IETF Internet Draft “Observations on IPv6 EH Filtering in the Real World” contains a detailed explanation about how to employ these tools to reproduce the experiments that produced the results published in there.
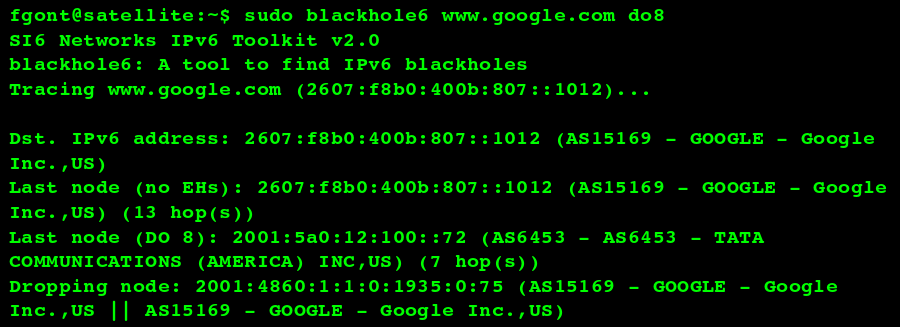
Another tool, blackhole6, has been incorporated into the SI6 Networks’ IPv6 Toolkit to troubleshoot packet drops resulting from the use of IPv6. blackhole6 can measure where in the network packets employing specific IPv6 Extension Headers are dropped, and report useful information such as the IPv6 address of the dropping node and the Autonomous System Number (and related information) of the dropping node. The following is a sample output of blackhole6:
Finally, a new tool has been incorporated to send arbitrary IPv6-based UDP datagrams: udp6 can flood an IPv6 address/UDP port with packets with forged IPv6 addresses and specific payloads (thanks to the “–data” option of the tool), etc. This tools complements the existing tcp6 tool, which can be employed for TCP-based attacks and experiments.
As with previous releases of the SI6 Networks’ IPv6 Toolkit, this latest release ships with comprehensive documentation via the on-line manual pages. Just “man ipvt6toolkit” for an overview of the available tools, or consult the tool-specific manual pages for details.
Have fun
Fernando