Microsoft released EMET v4.0 with a new (security) feature that enables protection against fraudulent websites or compromised root certification authorities (do you remember Comodo, DigiNotar, DigiCert, Turktrust et al. ;-)?)
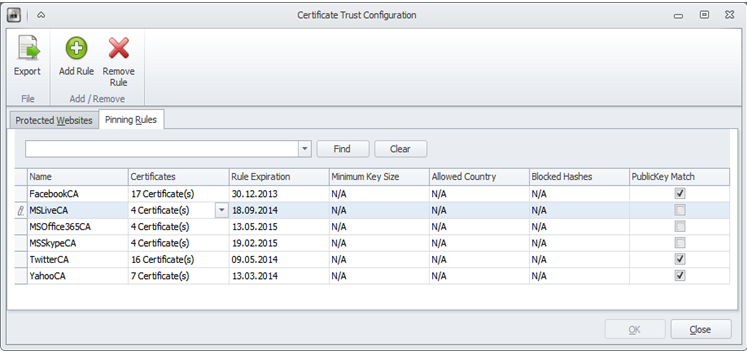
EMET defines via “certificate trust“ a trust chain between the domain name of a website (and its associated website certificate) and a root CA certificate. This is done through so called “pinning rules”. Here is one of the default pinning rules of EMET 4.0 for the domain name login.live.com:
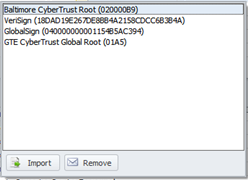
Thus, the login.live.com domain name is “pinned” to four root certification authorities. (Intermediate CAs are currently not supported).
If a user visits the website with Internet Explorer (only IE as desktop application is supported, Windows 8 (Metro-) App-IE not), Internet Explorer verifies the trust chain for the certificate of the website up to the root CA certificate according to the shell validation model.
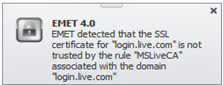
If the root CA certificate differs from the via EMET configured root CA, a warning message is displayed (and an event is logged to the application event protocol). The warning might look like this:
For a customer, I did a short presentation in terms of a quick walk through the capabilities, configuration and practice of EMET v. 4.0, which is, in my opinion a completely underestimated product with a rich security benefit. You may benefit from this presentation as well 😉 Please take a look here. The presentation is digitally signed with a qualified electronic signature. In order to be able to validate the signature, you will need a free signature validation software like SecCommerce´s SecSigner.
Have a nice day,
Friedwart Kuhn.