It is possible to spoof the URLs that Plume will open to arbitrary locations because of how Plume parses URLs. The preview of an URL in a tweet will show the complete (at least the host name and the first few chars of the URL) but shortened URL. However, if the URL contains a semicolon (;) the URL that will be opened is the part after the semicolon.
An attacker can make use of this behavior by specifying a URL like the following in a Tweet or direct message:
https://insinutaor.net/2018/05/security-of;https://www.ernw.de
Plume will display the first part of the URL and shorten the URL like this:
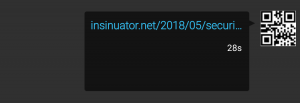
A user will think this is a valid link going to insinuator.net/2018/05/securi.... However, when clicking that link the URL https://www.ernw.de will be opened. This is a prime target for phishing attacks or tricking people into clicking on malicious links.
Affected Version
The affected version is at least Android Plume <= 6.30.2 (630190). There is only a partial fix implemented right now that prevents the spoofed link to be opened only for the first time a user clicks on it.
Disclosure Timeline
This bug has been disclosed to Ubermedia on May 19th. A disclosure date was set to 30 days.
I confirmed a partial fix on August 16th and noted that the issue still persists. Disclosure date was delayed to September 30th.
Final contact with a request for an updated status on November 16th was unanswered by the support since.