The use of Internet of Things devices is continuously increasing: People buy devices, such as smart assistants, to make their lives more comfortable or fitness trackers to assess sports activities. According to the Pew Research Center [1], every fifth American wears a device to track their fitness. In Germany, the number increases likewise. The increasing number of fitness trackers in use can also be seen in criminal proceedings, as there exist more and more cases where these devices provide evidence.
Which useful evidential information fitness trackers collect and how to analyze them forensically was part of a paper that we presented at WACCO 2020 this year [2]. The goal was to develop an open source program to support investigators analyzing data that fitness trackers provide and to give a general approach on how to analyze fitness trackers.
Fitness trackers are wrist bands without a broadly developed operating system and only small memory capacity. To configure the device and to view fitness information, a smartphone with the corresponding fitness app installed and connected via Bluetooth Low Energy (BLE) is required. Furthermore, most apps send the fitness data to a cloud server in addition. The fitness trackers collect information such as the heart rate, GPS, movement, or sleeping data. For investigators, the heart rate information is interesting as it helps to determine the time of death if a murder victim used a fitness tracker. To illustrate another example, assume a suspect who claims that she is innocent and that she watched a movie relaxing on her couch at the time of the crime. If investigators have access to her movement profile and discover that she instead moved a lot and fast during the time of the crime, her statement is less trustworthy.
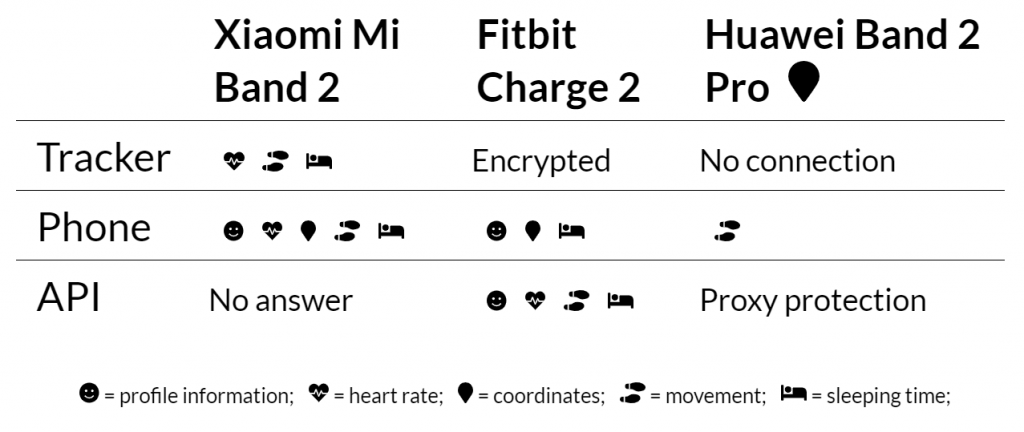
In order to develop the analysis program, we inspected three trackers: Xiaomi Mi Band 2; Fitbit Charge 2; Huawei Band 2 Pro. We installed the corresponding apps on a Samsung Galaxy S4 and hold with this setup three potential evidence sources. We analyzed the tracker device via the phone’s Bluetooth logs and bluepy, the smartphone’s internal data via the Android Debug Bridge, and API calls via the Burp Suite proxy.
In the table below, we summarized results of the analysis, more detailed information can be found in the paper. The first thing to notice is that most information can be found on the phone. Only in the case of Huawei, many databases were encrypted and few data were available. However, this does not mean that investigators should skip the analysis of the tracker device in general, it could still hold unsynchronized and valuable information. The last source is the API that the apps use to synchronize information with the cloud. Xiaomi and Fitbit have both public APIs, yet Xiaomi never responded to our registration request. In the case of Fitbit, user credentials are required to download data.
Based on the previous results, we developed an open source Python 3 tool [3] to investigate fitness trackers. It first extracts all data from the given source and afterward presents the results on interactive HTML reports. As it is built for forensic use cases, special attention was paid to the integrity of all data and to an informative log functionality that should be used for the chain of custody. Furthermore, the tool consists of single modules so that new fitness tracker models can easily be added in future work.
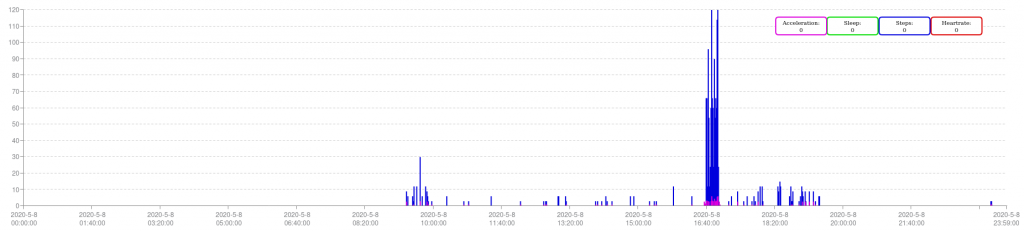
Investigators can view various reports. The first report, the user report, shows profile information. Thus, the investigator can easily check whether it is the suspected person who owns and uses the tracker device. The data report provides graphs with heart rate, movement, and sleeping hours. This is the main part of the report as it shows the most valuable information. One example graph can be seen in the picture below. The map report presents the collected GPS routes on a Google Maps view. In the compare report, selected analysis can be compared. And finally, the custom attribute report gives the option to add custom attributes for new devices.
We propose an approach for fitness tracker forensics that analysts should use when they find fitness trackers during the investigation.
- Preparation: When a fitness tracker is involved as a potential witness, we recommend putting the phone and the tracker into separate Faraday Bags to block further communication. Otherwise, a tracker could send mistakenly collected data to the phone and show activity, even after the seizure. This could lead to inconsistent data during the analysis.
- Extraction: In this step, investigators should use our tool to extract the information from the given sources. They should begin with the most volatile medium, the tracker itself. Next, we recommend extracting data from the phone and last, if possible, data from the cloud. Furthermore, investigators should request data from the fitness tracker company. Fitbit, for instance, provides information to law enforcement agencies.
- Analysis: During the analysis, investigators try to answer initial questions of the investigation by interpreting the collected data. They can use the different views and graphs in our tool for this purpose. The analysts should crosscheck and synchronize all the findings in the different sources, for instance, the phone and the tracker. The findings can show differences in the data which should be considered. This can, for example, happen when the tracker was not connected to the phone the time it was confiscated.
- Reporting: To report the findings, investigators should extract the graphs from our tool and use them in the report. In the end, the report must also hold all interactions with the devices to justify the decisions and results.
With the developed tool and the proposed approach, we believe that this work gives a good idea on how beneficial the analysis of fitness trackers for law enforcement can be and that we will see fitness trackers more often in legal cases in the future.
Best,
Florian Hantke & Andreas Dewald