I needed something new in my life, so I decided to take my favorite dog out for a walk in the ATT&CK jungle to check out the newly added sub-techniques…
ATT&CK stands for Adversarial Tactics, Techniques & Common Knowledge.
It’s a treasure trove of information about real-life offensive tradecraft.
I like to see it as an open-source encyclopedia of corporate post-exploitation.
There is a growing community around the project and more info keeps being added to it.
[Check out this post by @LikeTheCoins if you want to know more]
In this post, I just want to share my excitement about the new sub-techniques that are being added to the data to better structure it. [it’s a jungle out there…]
Still in beta, but I think it’s pretty cool, so I took some pictures for you. Check it out…
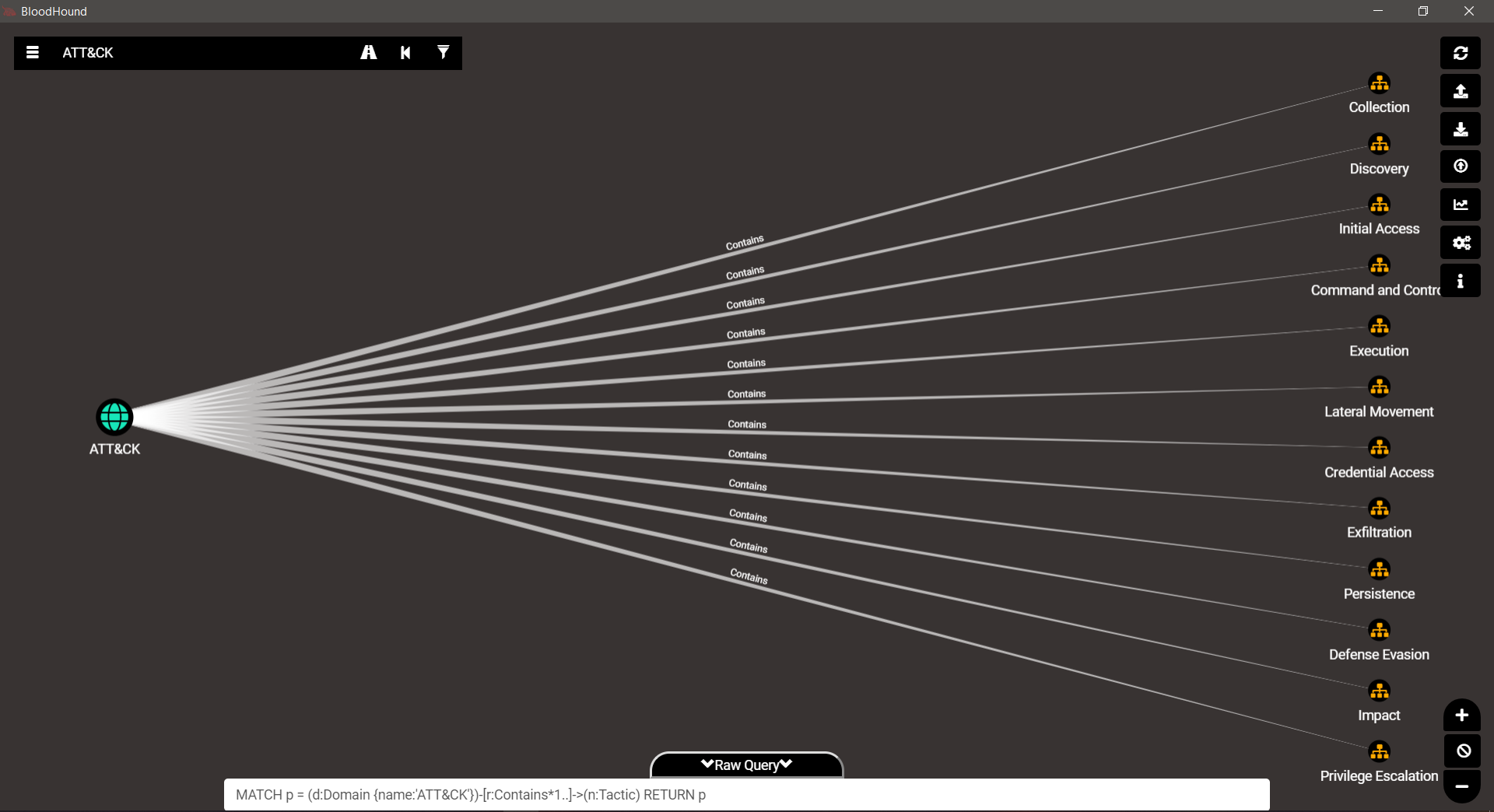
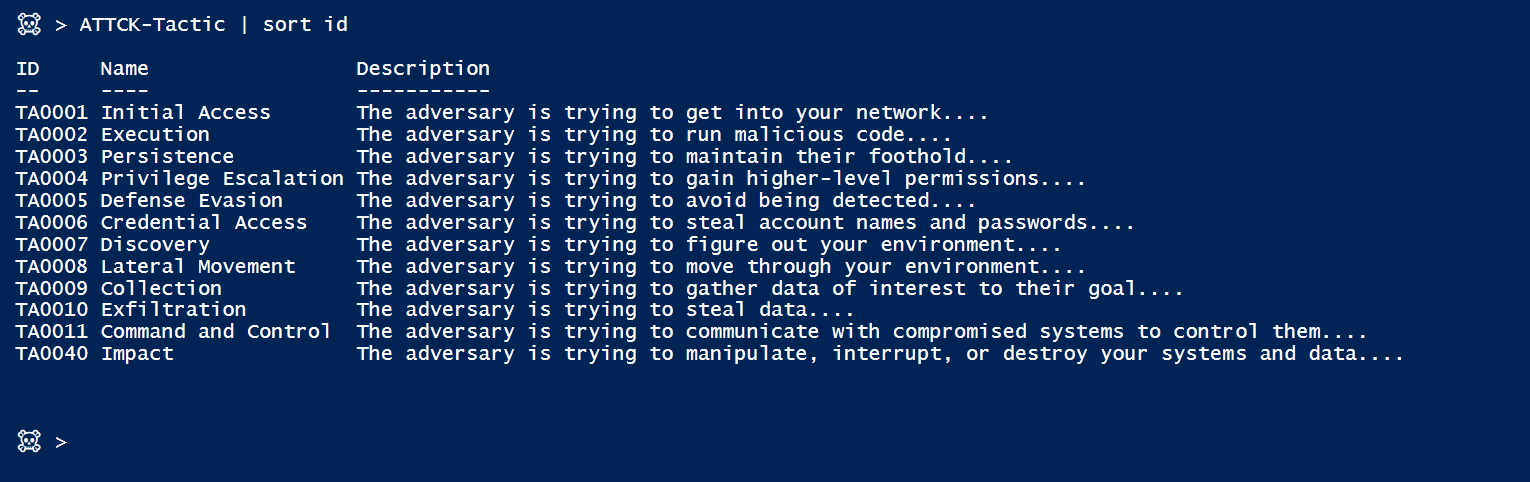
Now, a look at the various techniques and the new branching for each phase…
TA0001 – Initial Access
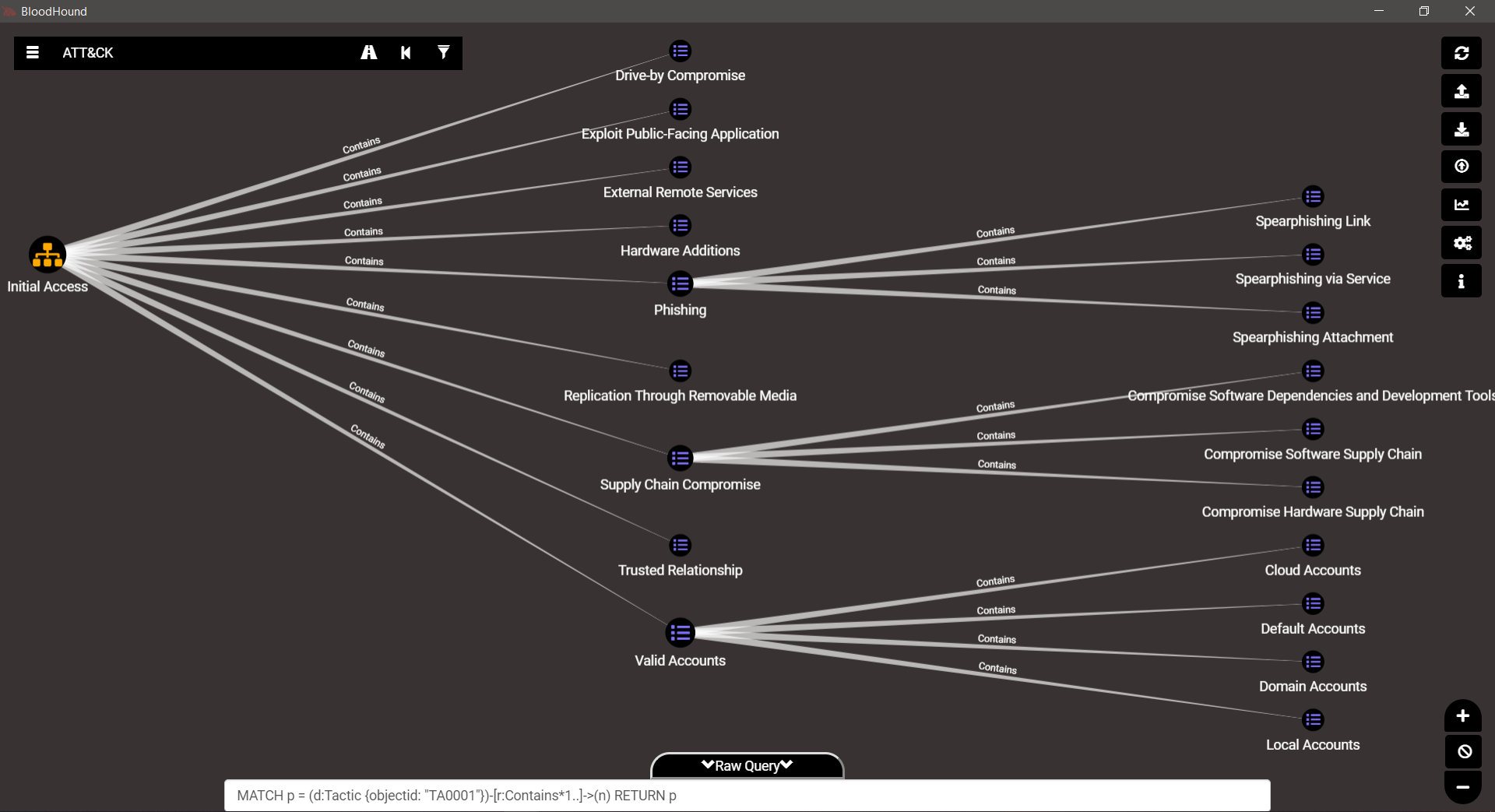
TA0002 – Execution
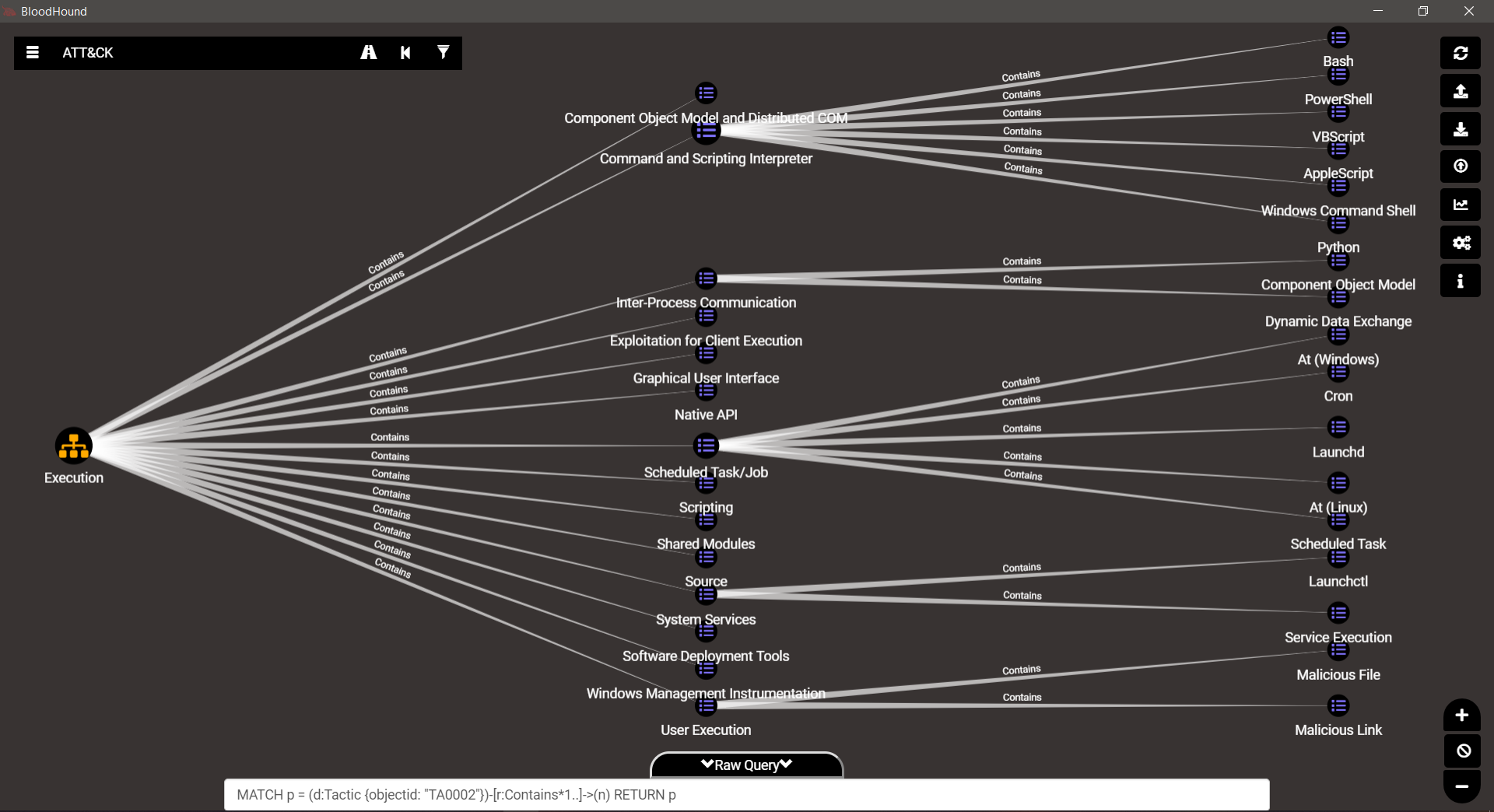
TA0003 – Persistence
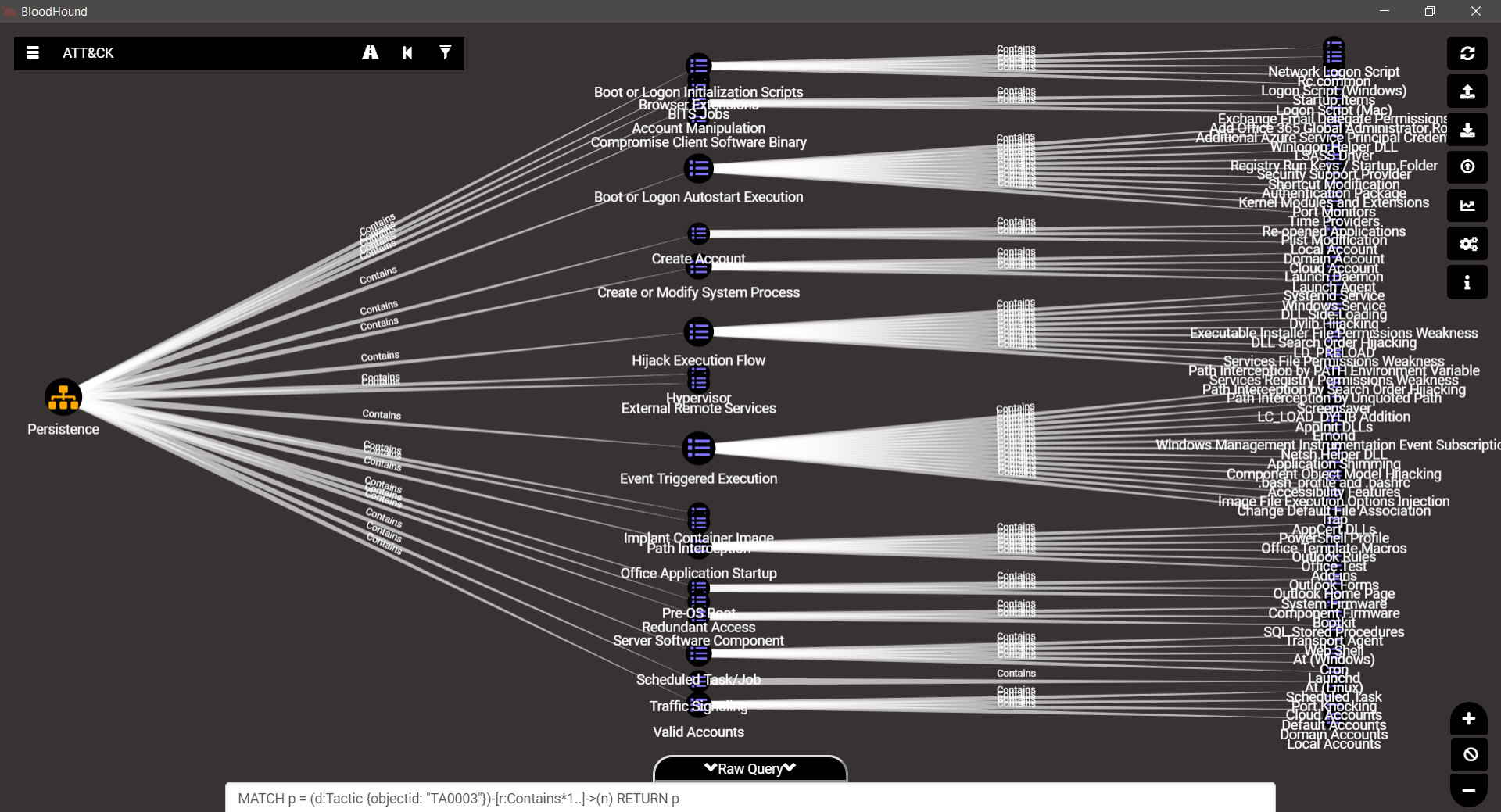
TA0004 – Privilege Escalation
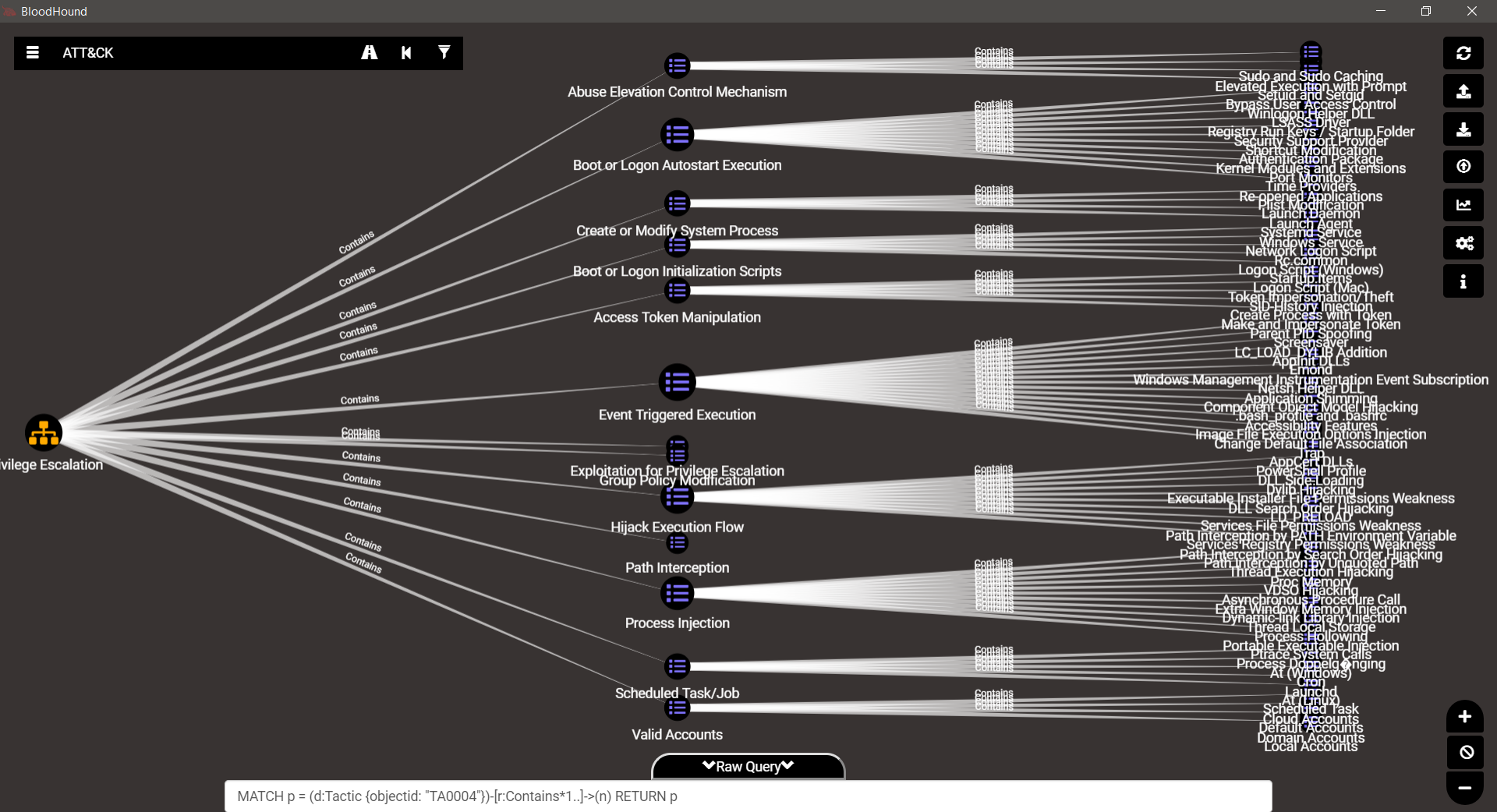
TA0005 – Defense Evasion
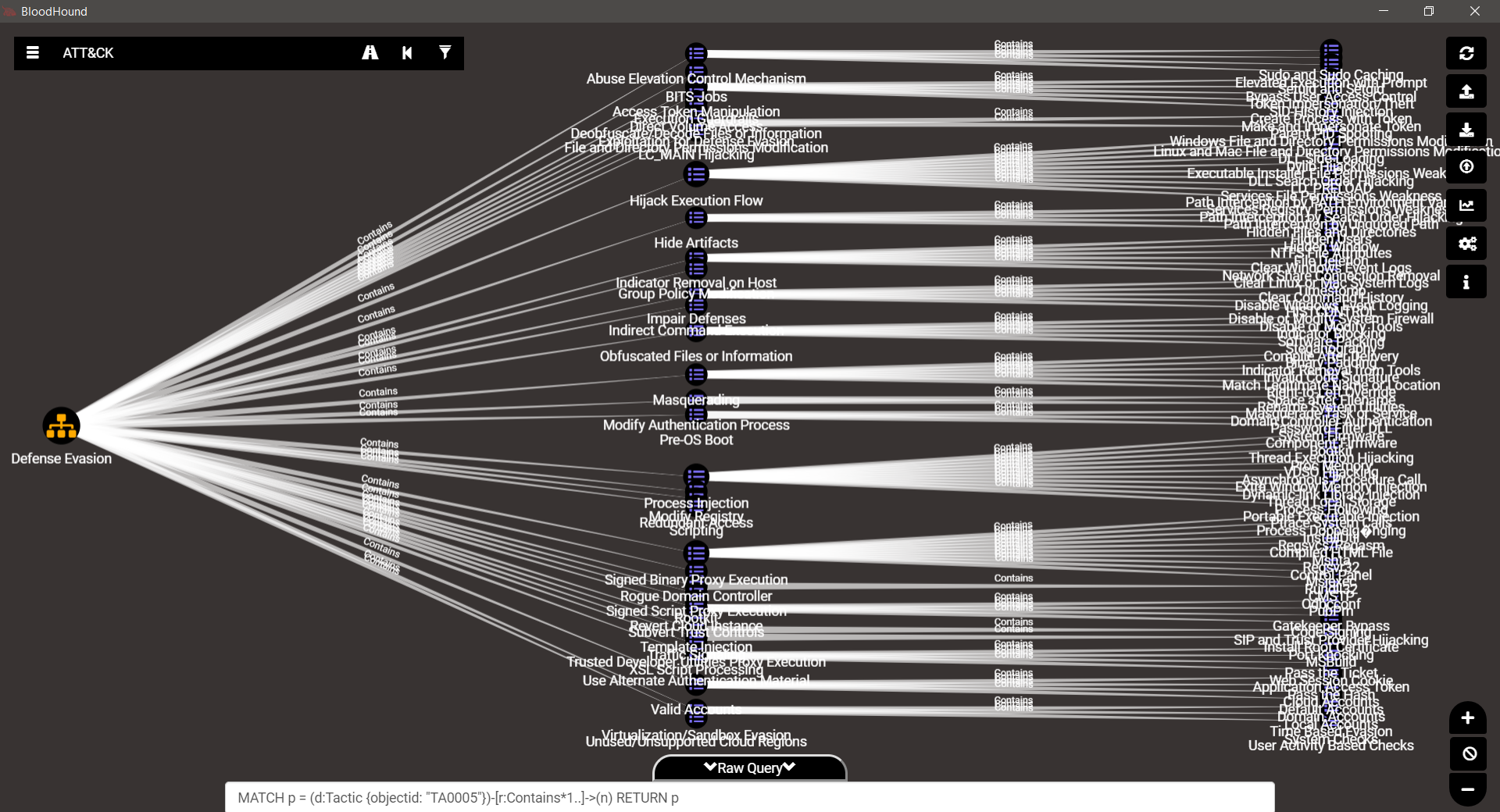
TA0006 – Credential Access
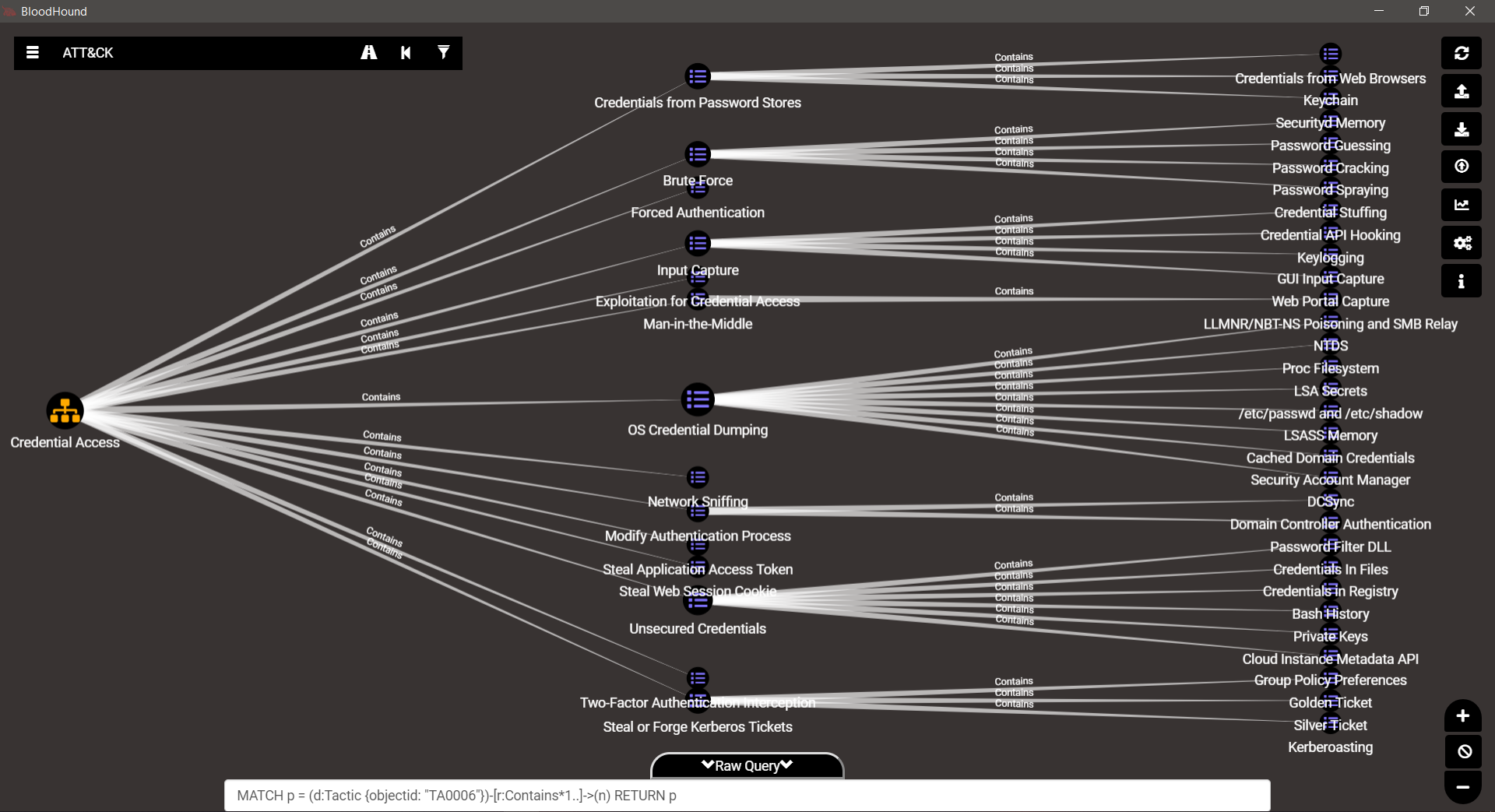
TA0007 – Discovery
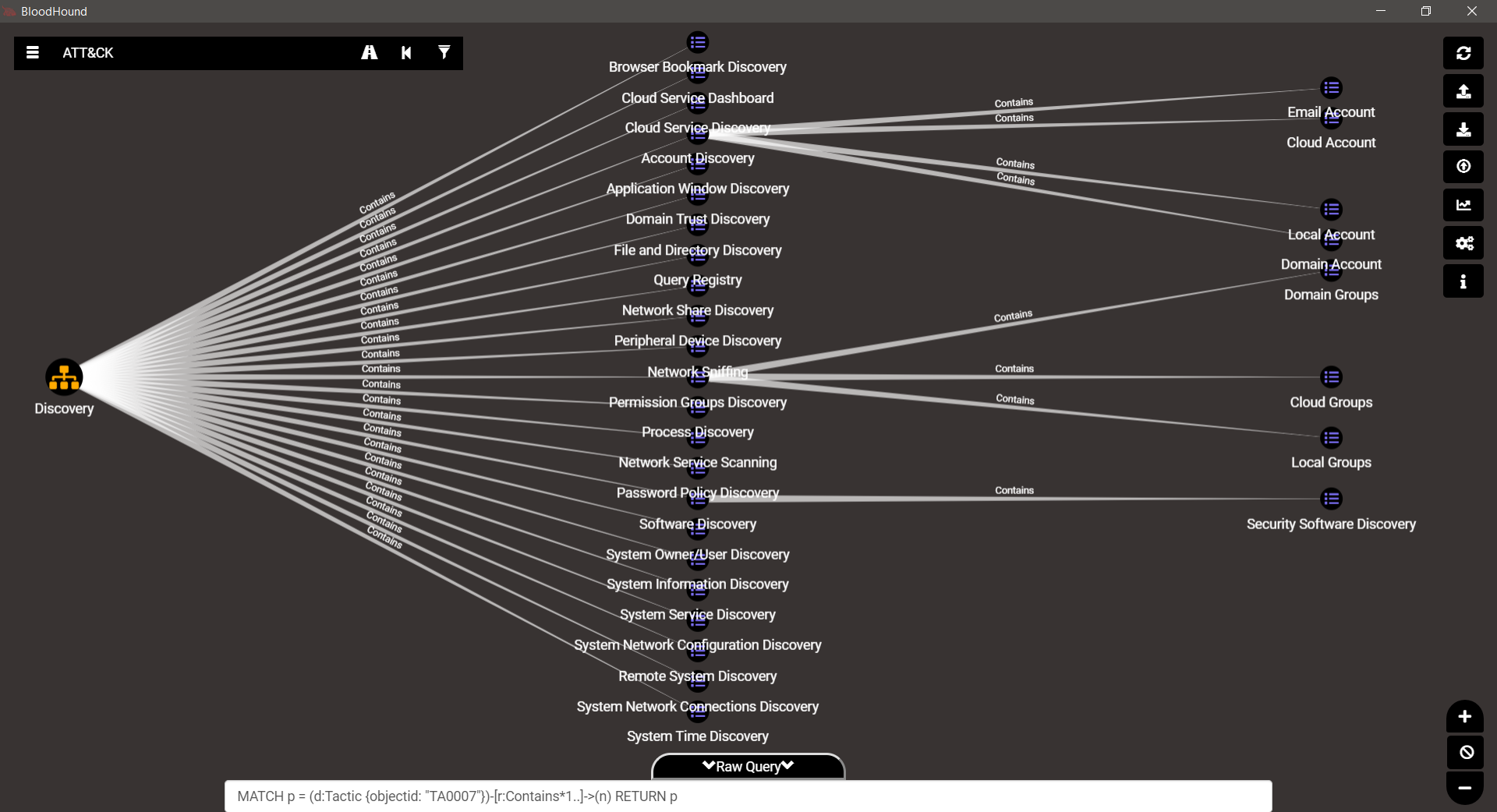
TA0008 – Lateral Movement
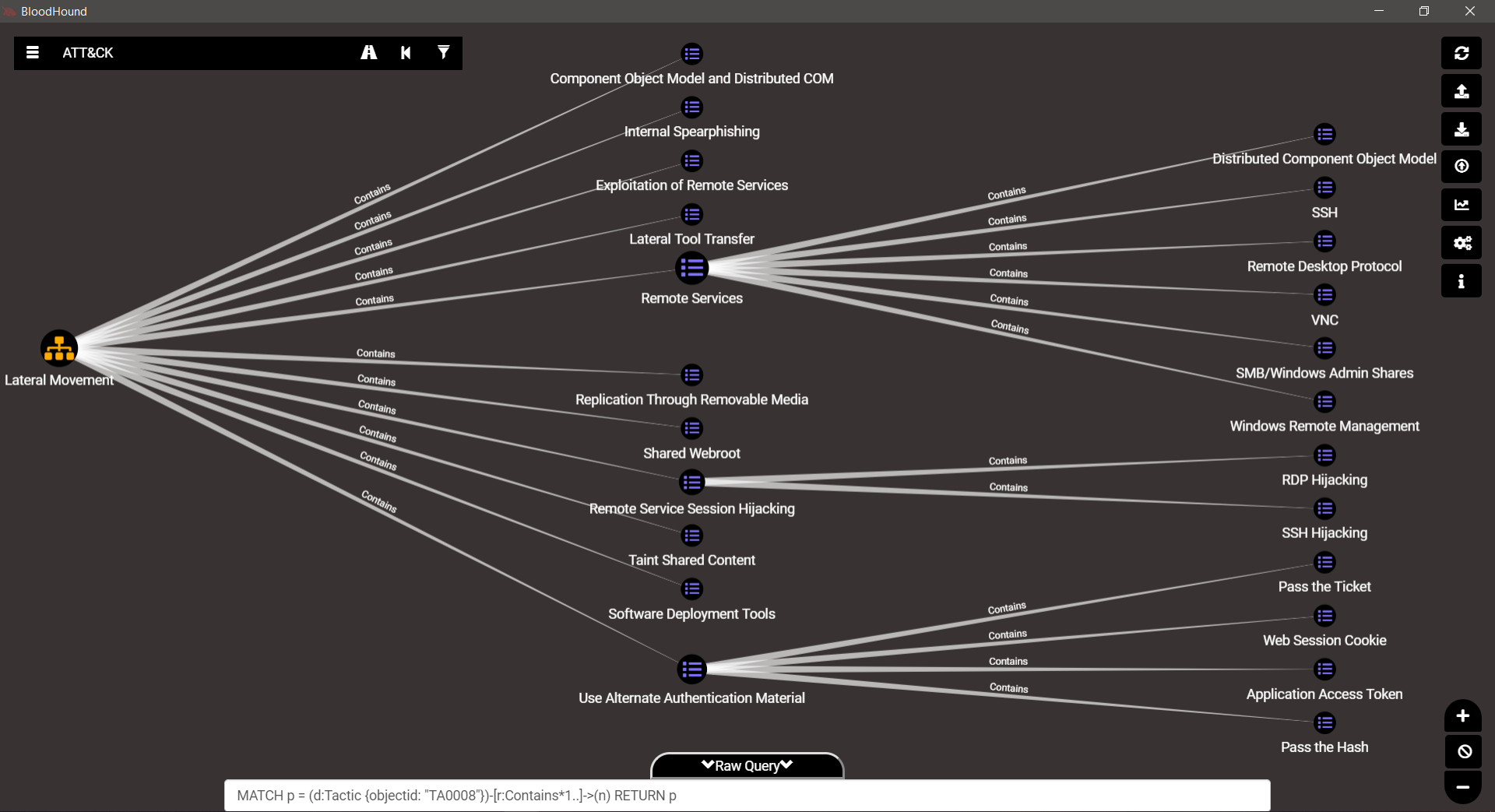
TA0009 – Collection
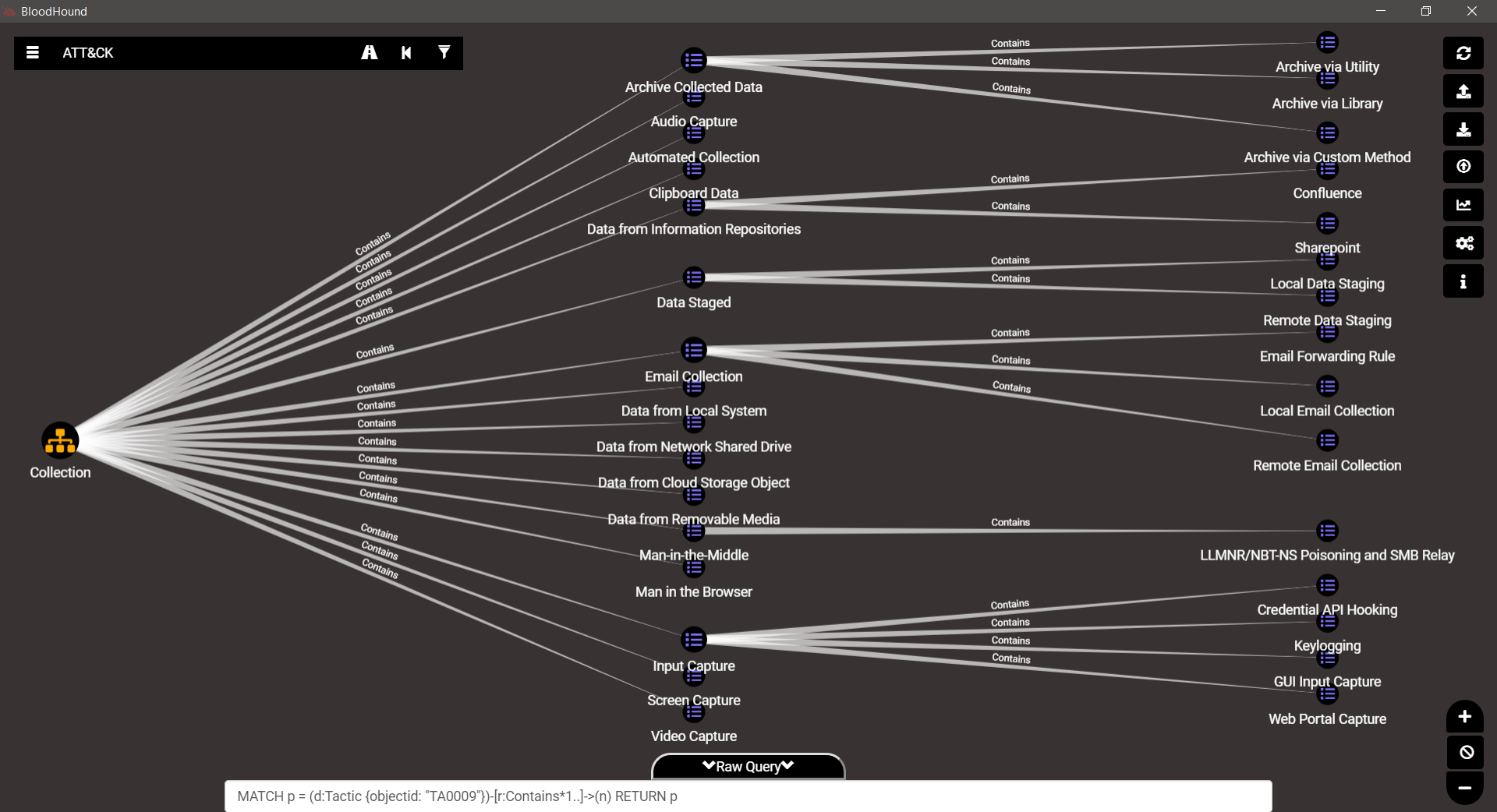
TA0010 – Exfiltration
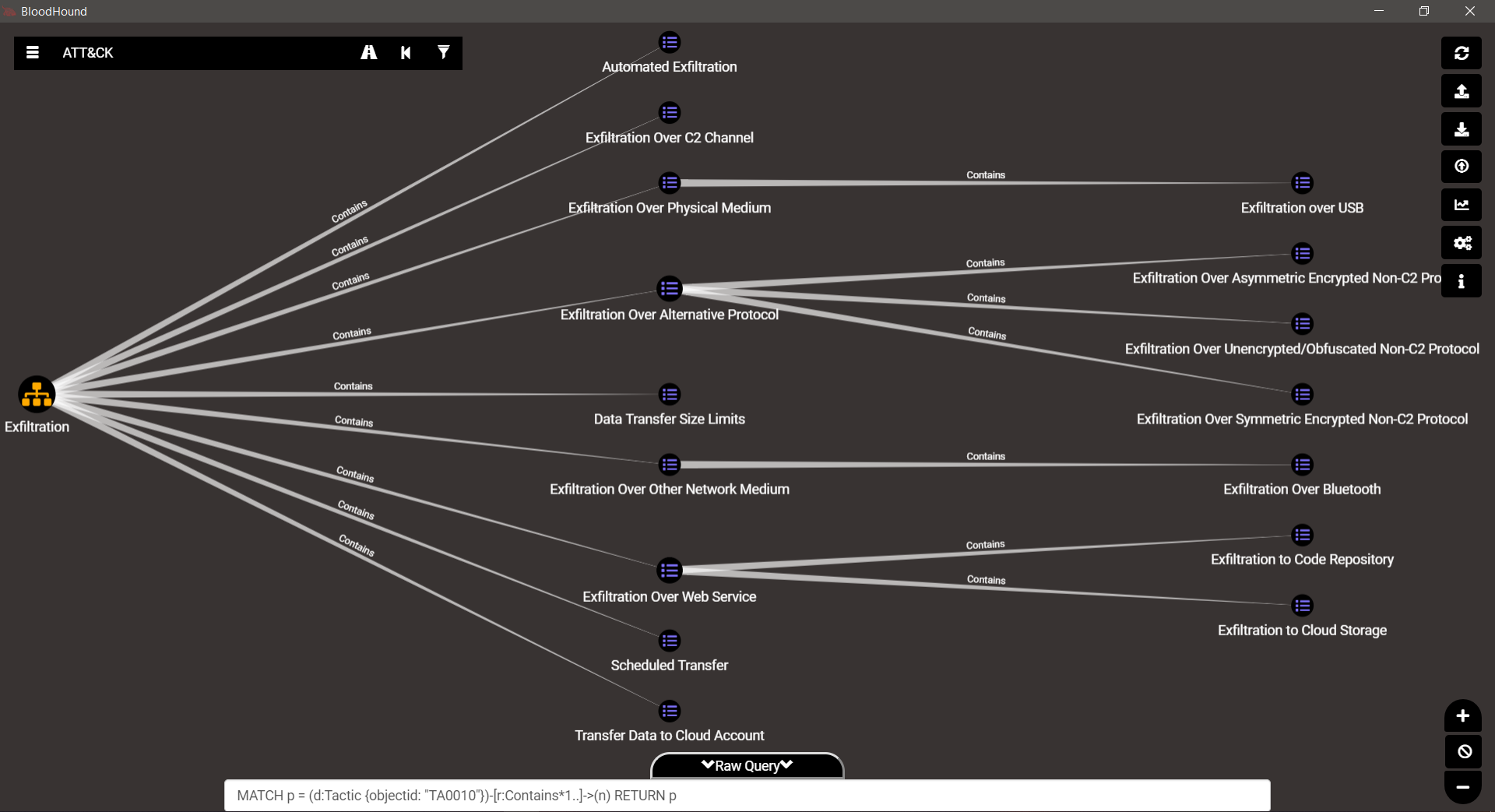
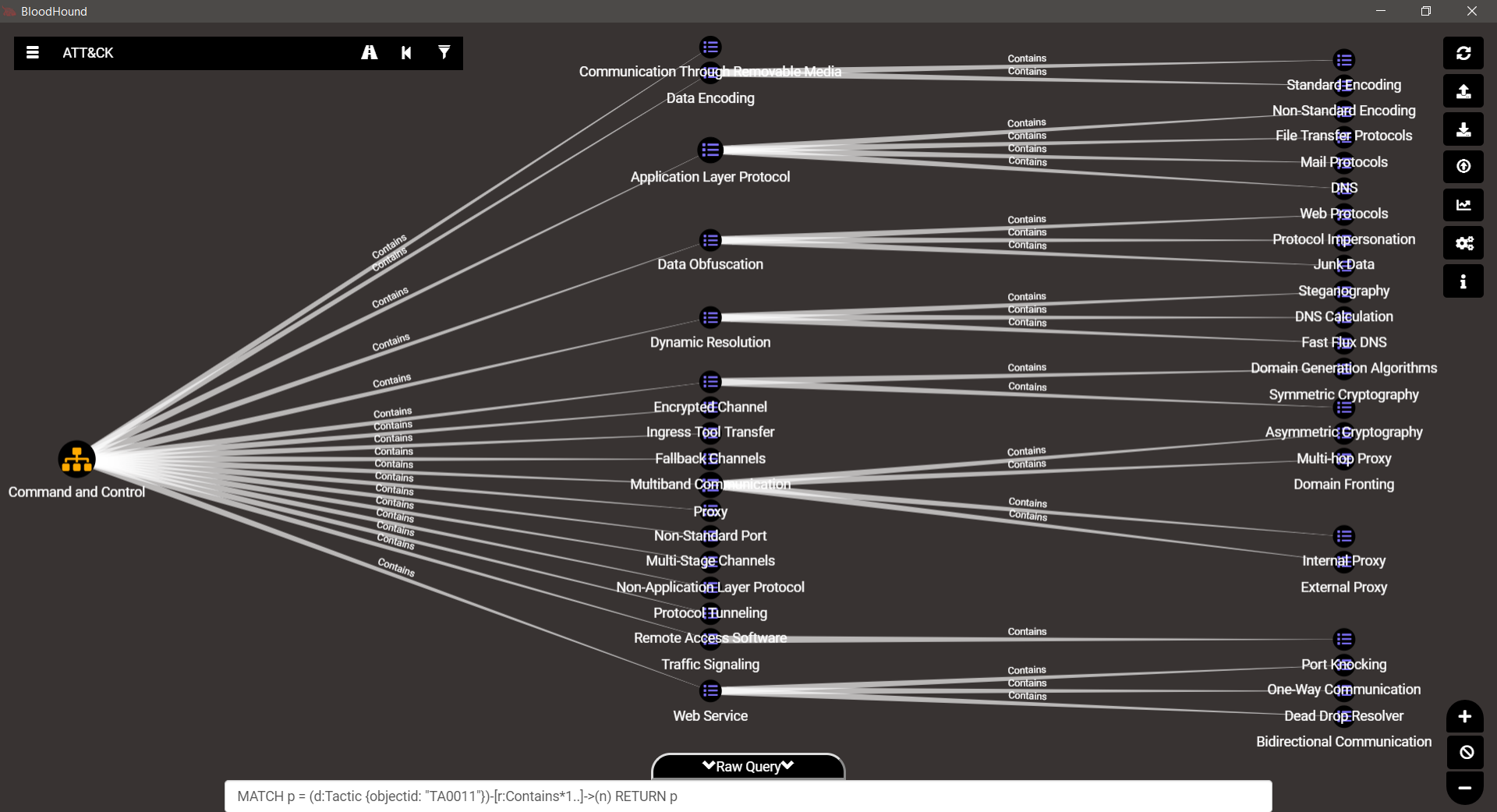
TA0011 – Command & Control
TA0040 – Impact
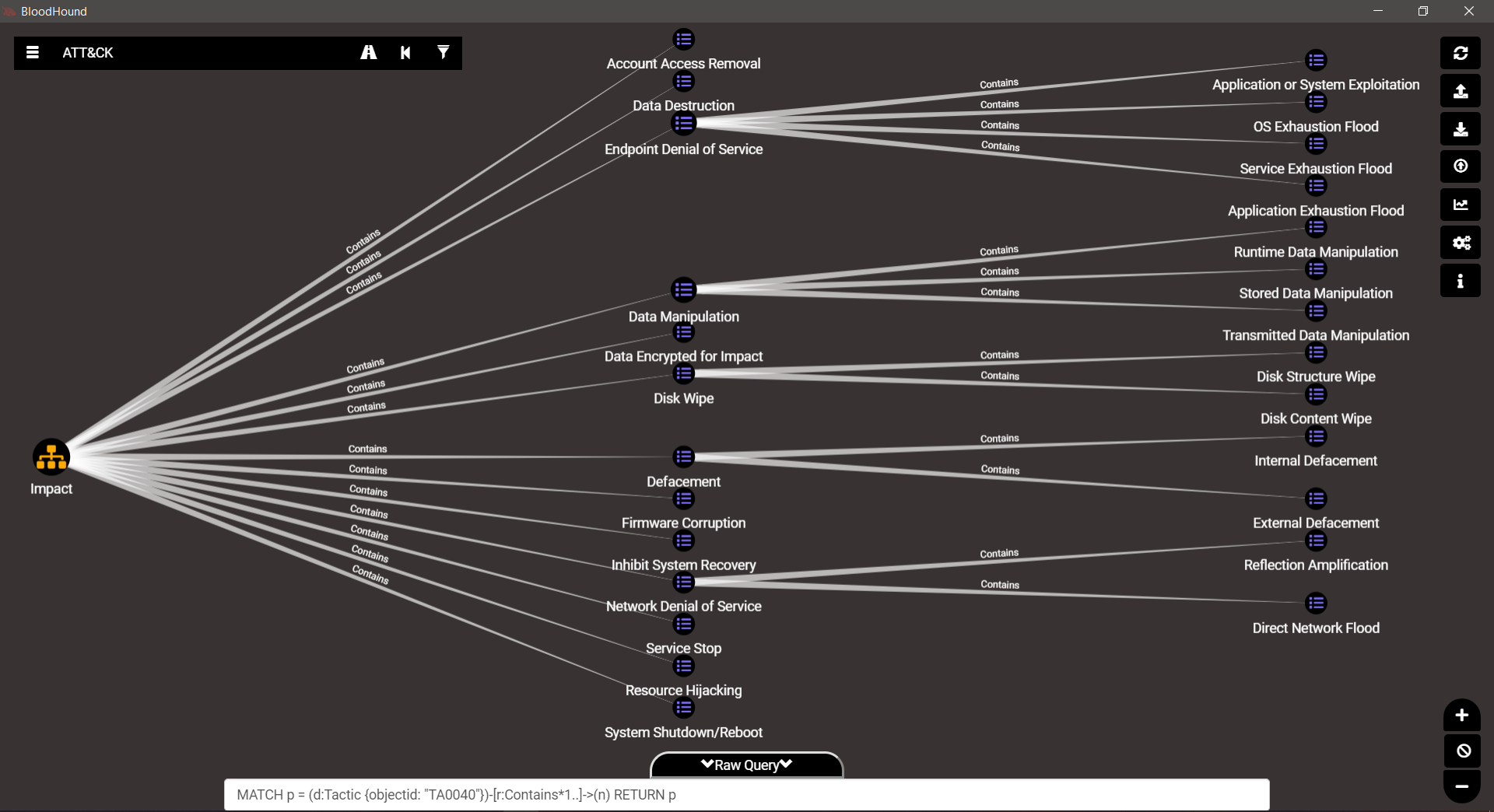
Gorgeous isn’t it…
Looking at all this is like reading the menu in front of the restaurant, and now that your mouth is watering, you probably want to explore all of this by yourself…
If you like, I’ll share the little PowerShell tool I use to manipulate ATT&CK from the command line.
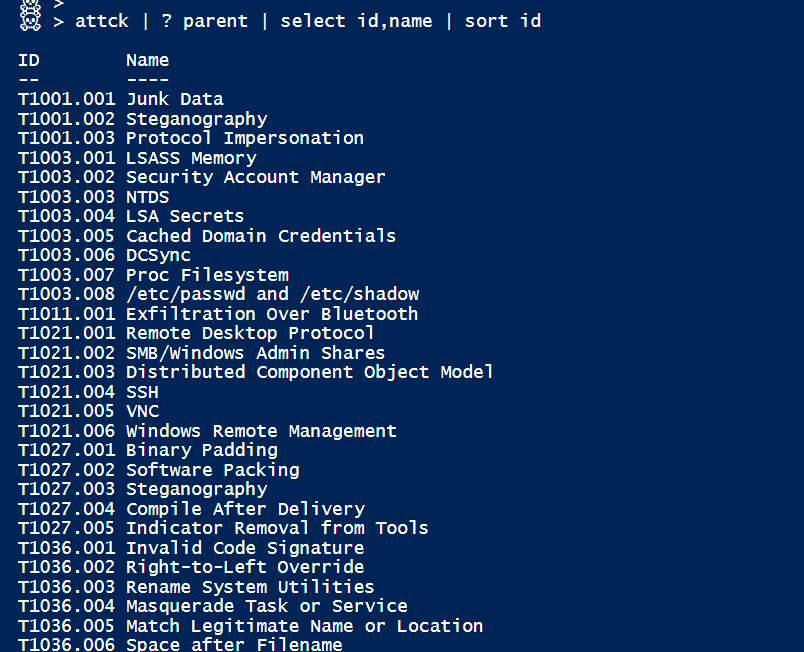
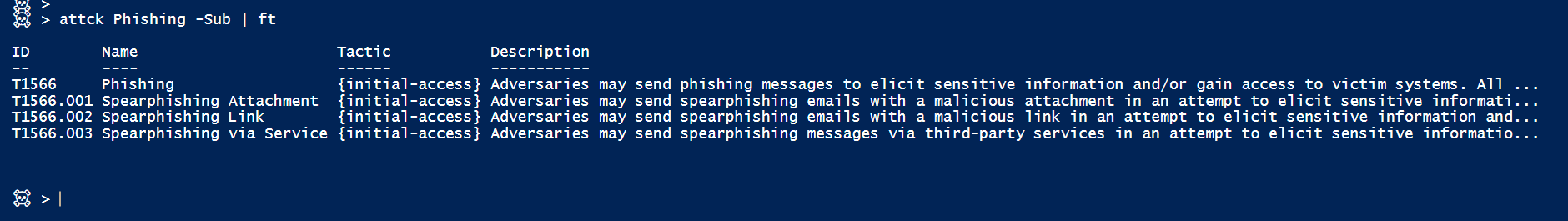
[Updated for sub-techniques. Beta too. Code can be found here]
you can check out this video of my [Sunday morning] talk at DerbyCon last year…
That’s about it for today. Hope you enjoyed it.
Ping me on the BloodHound Slack if you have any questions or remarks…