When I recently joined the Windows Security team at ERNW, Enno asked me if I wanted to write a ‘welcome’ blogpost on a topic of my choosing… Up for the challenge, and since I had been playing with BloodHound & Cypher for the last couple of months, I first thought I would do something on that topic.
However, after gathering my thoughts and some Cypher I had collected here and there, I realized that the topic of Bloodhound Cypher might actually require several blog posts… And so I changed my mind. I will keep the joys of Cypher for later, and in this post, I will talk about a tiny tool I wrote to query the Mitre ATT&CK™ knowledge base from the comfort of a PowerShell prompt.
Small, Simple and hopefully useful: should be suited for this first post…
TLDR: ATT&CK is great. Tool is here. Enjoy.
What is Mitre ATT&CK™ ?
The MITRE Corporation is a “not-for-profit [US] company that operates multiple federally funded research and development centers” and is “dedicated to solving problems for a safer world”
“MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target. ATT&CK is useful for understanding security risk against known adversary behavior, for planning security improvements, and verifying defenses work as expected.”

In simple words, a great source of knowledge for anyone wanting to know more about real life threat groups, publicly known techniques, and tools used ‘in the wild’. All this info is available online via the ATT&CK wiki, and each page links to further online references in order to dig deeper into each topic.
Some might argue that this data is not complete (and it most probably isn’t), but I’d rather see this glass half full than half empty. It is in my opinion a fantastic attempt at classifying and sharing what there is, and for sure a valuable resource for the community.
Each described Technique has associated Detection and Mitigation, and is classified according to the attacker kill chain with a unique ID. Several open source projects/tools use this ATT&CK ID as a common reference, making it easier to identify/document/reference what is being searched/tested/automated and so on…
For more info on the Mitre ATT&CK project, you can also check this x33fcon video from Christopher Korban & Cody Thomas.
For examples of projects/tools referencing ATT&CK, check CALDERA / Atomic Red Team / HELK .
What is this PowerShell Tool ?
Now that I told you how much I like ATT&CK, I also have to tell you how much I love PowerShell… I Love it so much, that I try to glue everything with it. And of course, ATT&CK was on my list…
PoSh_ATTCK is a set of Cmdlets to manipulate the ATT&CK data from the command line. Nothing new… However last January, ATT&CK announced that the old MediaWiki REST API would be deprecated in favor of a new and shiny STIX one, so I decided it was time to rewrite my old cmdlets.
To keep it short, let’s just say that the easiest way to query this STIX data is to use a TAXII python library (which doesn’t really make much sense for a PowerShell tool), so I decided to take another road, and get the data from a JSON object that ATT&CK publishes on their Cyber-Threat-Intelligence (cti) repository (instead of going thru all this TAXII documentation).
A simple Invoke-RestMethod to GitHub and all that knowledge is returned as a single JSON string and is immediately available as objects… Cool!
Now let’s check out some Cmdlet build on top of that…
Install & Import
First things first, you need some code. For now, you can find it in a single flat file on my GitHub. I do plan to turn it into a module for the PowerShell Gallery and move the code to the ERNW GitHub (as soon as I get a moment to add the PRE and MOBILE cmdlets).
Good practice would recommend you read the code before playing with it, and I trust you for doing so… Now that this is done, you can paste it into ISE|VSCode, load it in your session (F5) and you are good to go…
Now, we need to make a call to the Mitre CTI repository to memorize all that knowledge. This is done with the following command at the beginning of your session (or if for any reason you were to need to reload it).
PS> Invoke-ATTCKnowledge -Sync
Data is now stored in memory and can be manipulated with 3 simple commands:
Get-ATTCKTechnique
This Cmdlet returns Technique objects, and is probably the one you will be using the most (and therefor has the shortest Alias :).
Basic syntax is as follows:
PS> Get-ATTCKTechnique # List all Techniques
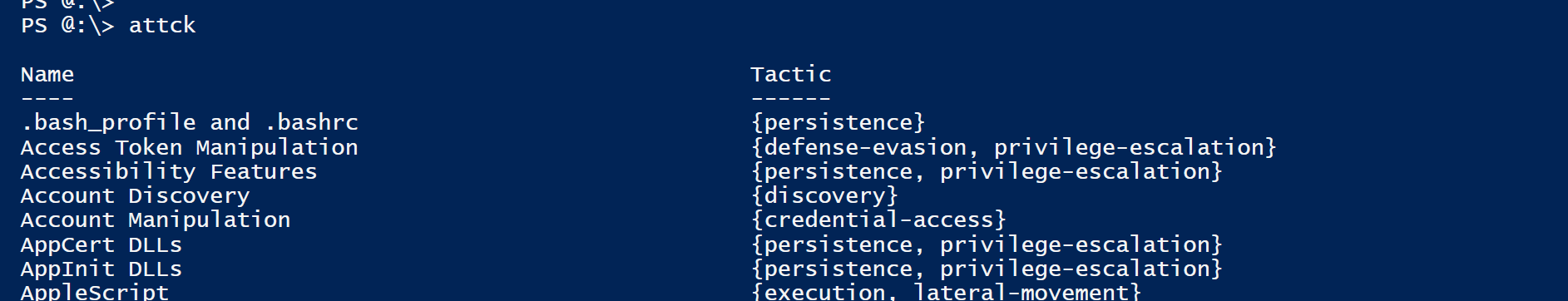
Note: Cmdlet has aliases of ATTCK-Technique or ATTCK (ATT<tab>)
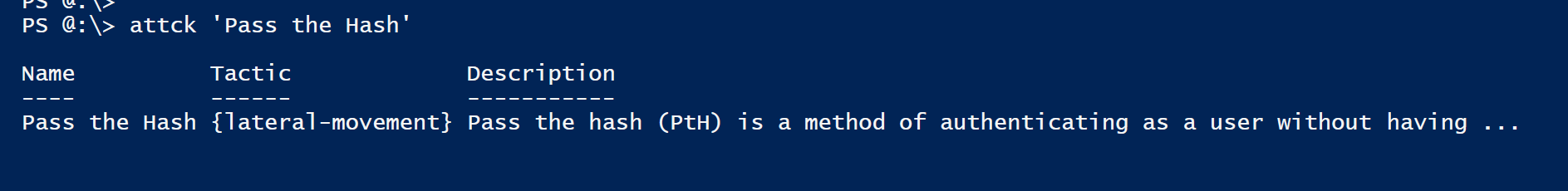
PS> ATTCK <name> # View Technique by Name
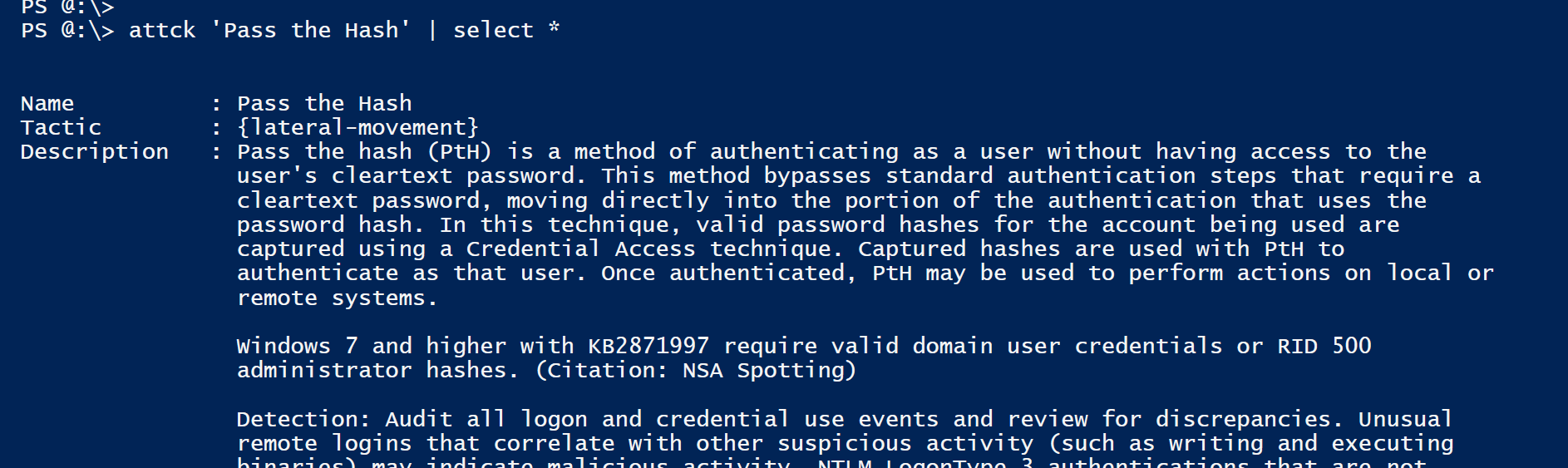
PS> ATTCK <name> | Select * # View full object
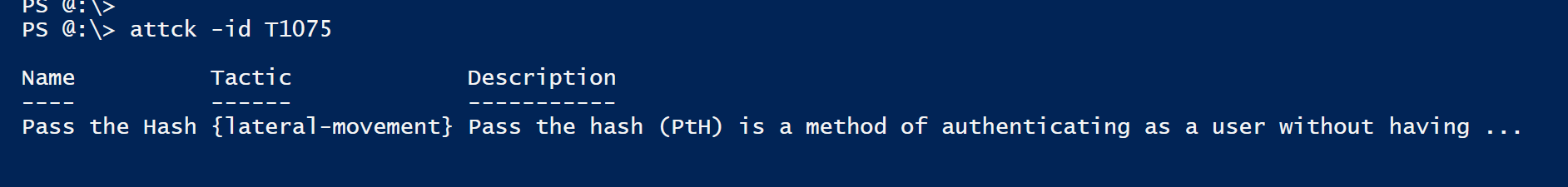
PS> ATTCK -ID <id> # View Technique by ID
PS> ATTCK -Description <keyword> # Search for Keyword in Technique description
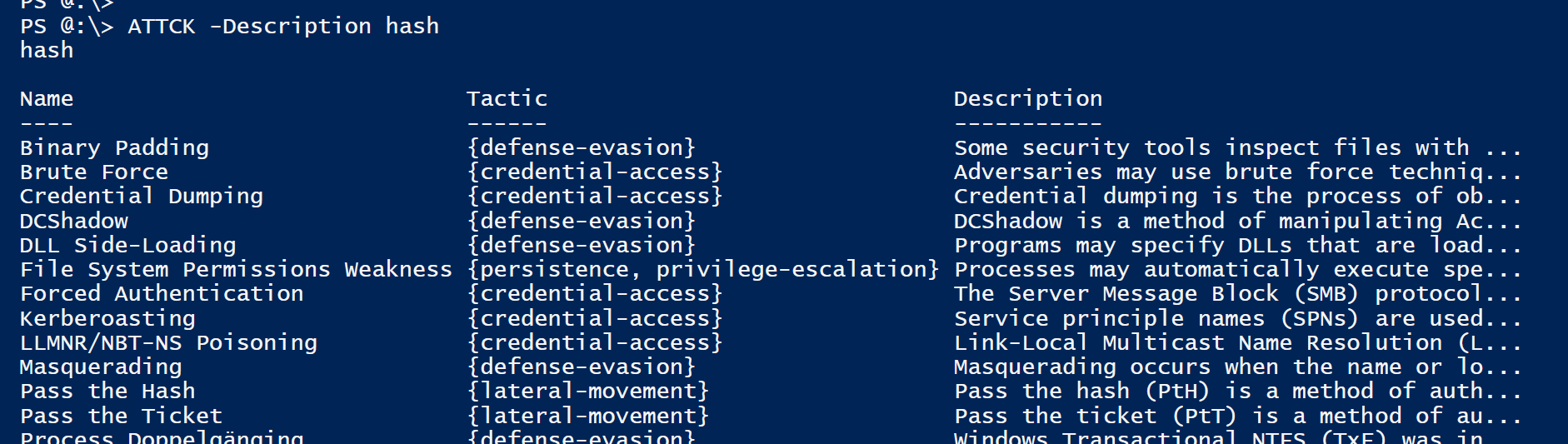
PS> ATTCK -Filter <Tactic> <Platform> <Permission> # Return filtered Technique list
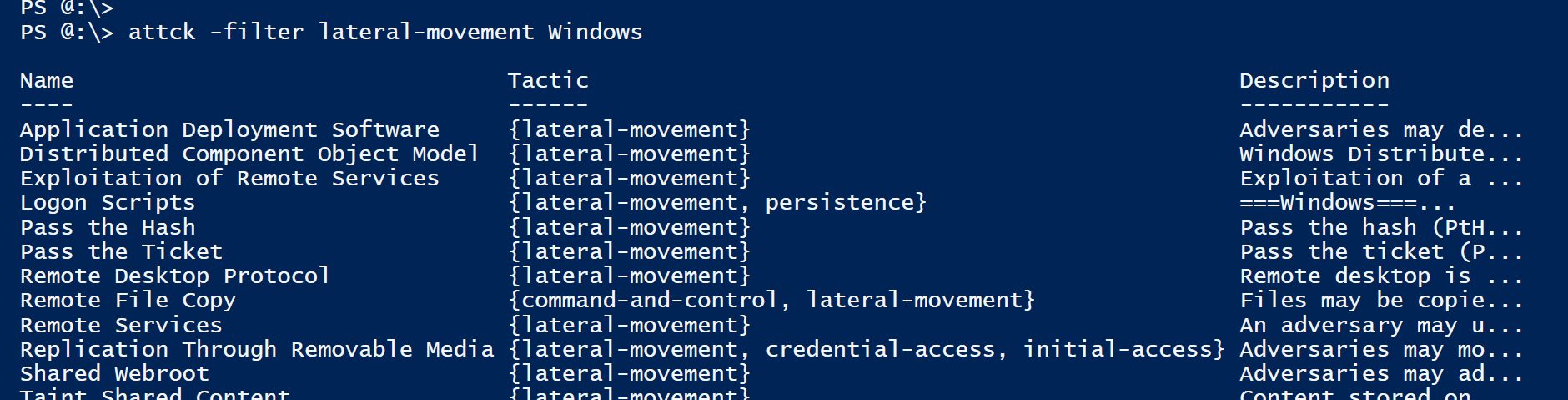
For more info and examples, check Get-Help ATTCK -Full
Note: When viewing by Name/ID, use -Reference to retrieve object refs, use -Online to open wiki page or references in your browser.
Everything tab-completes except <keyword>
Get-ATTCKSoftware
This Cmdlets return ATT&CK software objects. Default output is as follows:
PS> ATTCK-Software <name> # Return Software objects
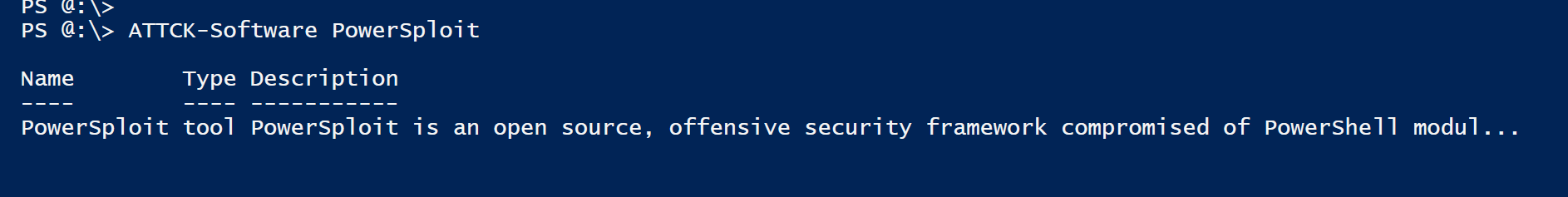
Parameters are slightly different, but this cmdlet works in the same way than the previous one. I’ll let you play with it and am sure you will figure it out…
For more info and examples, check Get-Help ATTCK-Software -Full
Get-ATTCKGroup
This last command returns ATT&CK Group objects and also works the same way:
PS> ATTCK-Group <name> # Return Group object
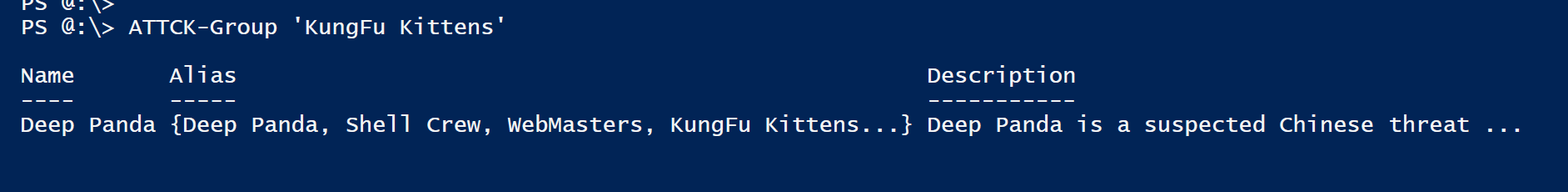
Note: Aliases can be used instead of group name in dynamic params for quick and easy search
For more info and examples, check Get-Help ATTCK-Software -Full
PoSh Features
By default, only part of properties are displayed to screen. Pipe Cmdlet output to | Select * to display all properties of objects. Properties names tab complete after the pipeline (where/select/sort)
All 3 Cmdlets have an -Online switch parameter (that can be combined with the -Reference) when searching by name or ID. Awesome for quick internet browsing…
And because it’s PowerShell, now you can do whatever you want with that data… Imagination is the limit.
Aaand… because it’s PowerShell, for the same price you get:
- Objects
- Easy syntax and Aliases
- Tab-completion / Intellisense
- Dynamic Params
- Multi OS support
What more could one ask for?
I really think you should check it out… And so I wrote a blogpost.
Tool is here. Hope you like it.
Outro
Common knowledge is to me the only solution in a field (IT) that evolves quicker than the people that create it.
ATT&CK serves as an open encyclopedia of observed threat groups and publicly known techniques, and is a great source of info for N00bs and Pr0s alike, whether you want to perfect your knowledge or document your moves (Pipe to Set-Clipboard to paste in report…).
Manipulating this data from the command line (with PowerShell or whatever you like) allows for powerful search and quick access to the info needed, and I hope this post makes you want to give it a go…
With this being said, that’s it folks. I hope you found it useful – and that some of you are already downloading the code to test it out.
Hit me on Twitter if you have any questions or feedback, and enjoy exploring all that ATT&CK knowledge.
Until next time, and thanks for reading.