Here is a short blog post that explains how you can make your own Man-in-the-Middle (MitM) setup for sniffing the traffic between a SIM card and the backend server. This is NOT a new research but I hope this will help anyone who doesn’t have a telco background to get started to play with mobile data sniffing and fake base stations. This is applicable to many scenarios today as we have so many IoT devices with SIM cards in it that connects to the backend.
In this particular case, I am explaining the simplest scenario where the SIM card is working with 2G and GPRS. You can probably expect me with more articles with 3G, 4G MitM in future. But lets stick to 2G and GPRS for now.
Motivation
In many IoT devices these days, we have a scenario that the device is connected to its backend with a SIM card. The IoT device could be anything starting from simple things like a coffee machine, a smart watch, smart glasses to bigger stuff like cars or critical medical equipment. If you want to sniff the traffic between your IoT device and the backend server, a setup like this will be very handy to you.
Objective
Perform Man-in-the-Middle for the mobile data traffic. In order to perform that, we make a simple fake base station using USRP hardware.
Requirements
I am mentioning the devices that I used for making this setup.
There are many other possibilities of doing the same. So I don’t have any claims that this is the best possible way to do it!
Hardware
- USRP B210 (with antennas and cables (USB 3) to connect to PC)
- A smart phone/or an old GSM phone. In case of an IoT pentest scenario, we have the IoT device here instead.
- A SIM card
- A laptop
Software
- OpenBTS
- SipauthServ
- Smqueue (Optional – if you want to play with some SMS messaging)
- Asterisk (Optional – if you want to play with making calls)
- OS – Ubuntu 16.04
Human ability
Googling, reading, writing and a lot of patience to start, stop, play kicker, restart, stop, pause, drink coffee, start, stop ….. in loop. 😉
What is OpenBTS
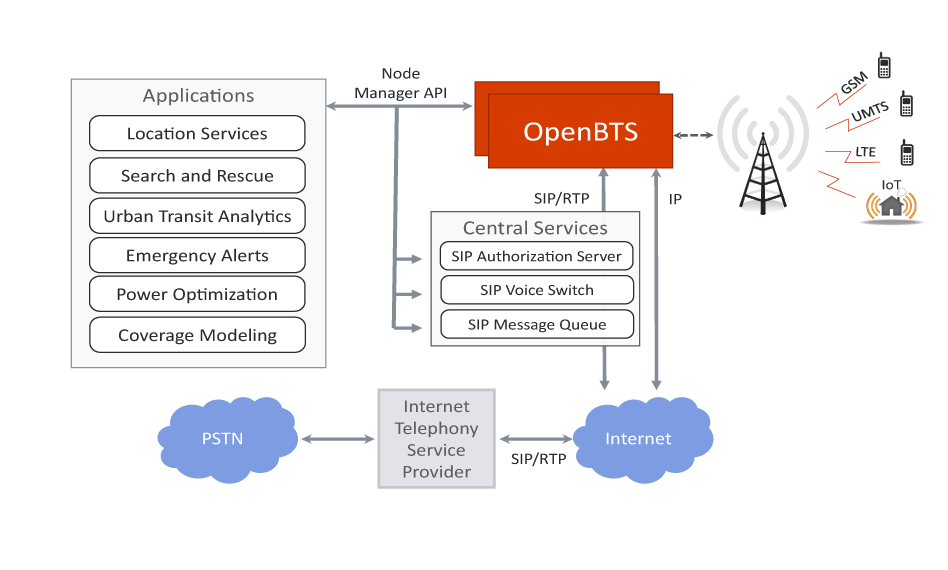
OpenBTS.org is an open source software project dedicated to making telco protocols and traditionally complex, proprietary hardware systems with Internet Protocol and a flexible software architecture. The OpenBTS software is a Linux application that uses a software-defined radio to present a standard 3GPP air interface to user devices, while simultaneously presenting those devices as SIP endpoints to the Internet. This forms the basis of a new type of wireless network which promises to expand coverage to unserved and underserved markets while unleashing a platform for innovation, including offering support for emerging network technologies, such as those targeted at the Internet of Things. [reference]
Building your fake base station

The first thing to do is having a working build of OpenBTS running.
Source code:
I followed this link for building the OpenBTS from source. There is usually some missing dependencies to fix. Apart from that, there is no specific setup needed for building OpenBTS. To get started, we mainly need two services which is OpenBTS itself and SipauthServe. After building OpenBTS and SipauthServe from source, start both the services in a terminal. In the above link, there is also other components such as Smqueue and Asterisk which is needed for making calling and SMS features working. But as our focus here is mainly on mobile data, (here GPRS), we don’t care about setting those components here. But it is still fun to try and get it working.
Running OpenBTS
- Connect the USRP device to your computer with the USB 3 cable that comes with it.
- In my case, I made a VM where I built all the required software to make it easy to port. When you have a VM, make sure you have USB 3 forwarding possibility. In virtualbox, you should be able to enable USB > Devices > Ettus Research USRP B210 (or some similar name. If you don’t know the right name, do dmesg to figure out.)
- uhd_usrp_probe : Use this command – USRP Hardware Driver Peripheral Report Utility for linux – this will download the firmware for B210 once it detects the device.
- Run SipauthServe
home/dev/subscriberRegistry/apps$ sudo ./sipauthserve
- Run OpenBTS
home/dev/openbts/apps$ sudo ./OpenBTS
- Run OpenBTSCLI
home/dev/openbts/apps$ sudo ./OpenBTSCLI
Configuring the Base Station
In the above step, you would have noticed running OpenBTSCLI. This is mainly for configuring our OpenBTS.
Below are the main configurations to be done in OpenBTSCLI for us to get a functioning model:
- Allow any phone to connect to the base station without any authentication. This allows registrations from any phone regardless of their provider.
OpenBTS> config Control.LUR.OpenRegistration .*
- Enable GPRS
OpenBTS> config GPRS.Enable 1
- Enable IP forwarding
echo 1 > /proc/sys/net/ipv4/ip_forward
- Setup iptables : The whole GPRS and IPtables setup is found in detail here.
Getting the phone connect to the Base Station
If you have a smart phone, you have to change some settings to actually make the phone connect to the base station. This gets even more challenging when there is an IoT device in place as there is hardly any option to configure the “Mobile Network” in an IoT device. But we will get to that later.
Setting up an Android phone:
(Basically similar on iPhones.)
- Enable 2G. This is downgrading to 2G from 4G: Settings > Cellular Networks > Preferred network type > 2G
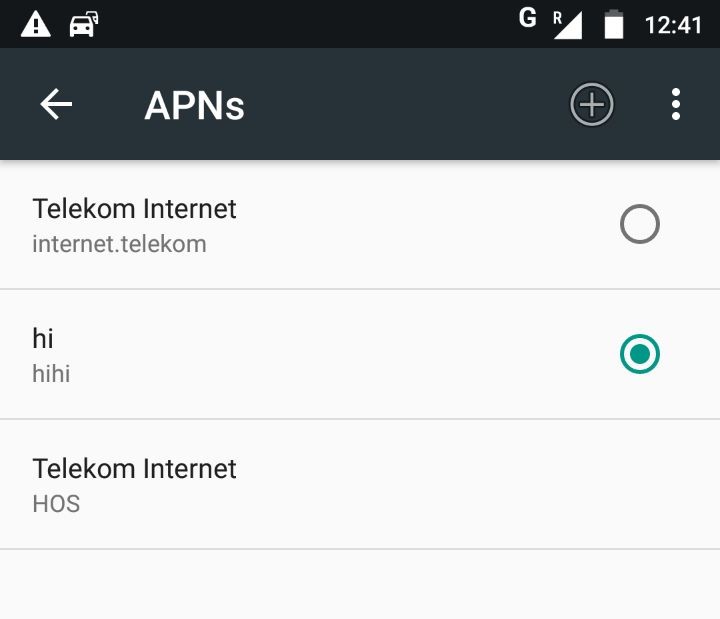
- Add an APN : Settings > Cellular Networks > Access Point Names. When you add, make sure that the MCC and MNC are set as the same value as for the SIM card. In Germany, the MCC is 262. The MNC will change based on the provider. This is a link where you can find that out. Apart from that, the APN and Name value could be anything. Also, keep the authentication as none.
- Search for our base station and manually connect to it: Settings > Cellular Networks > Search Networks. Usually it appears as numbers including MCC and MNC values.
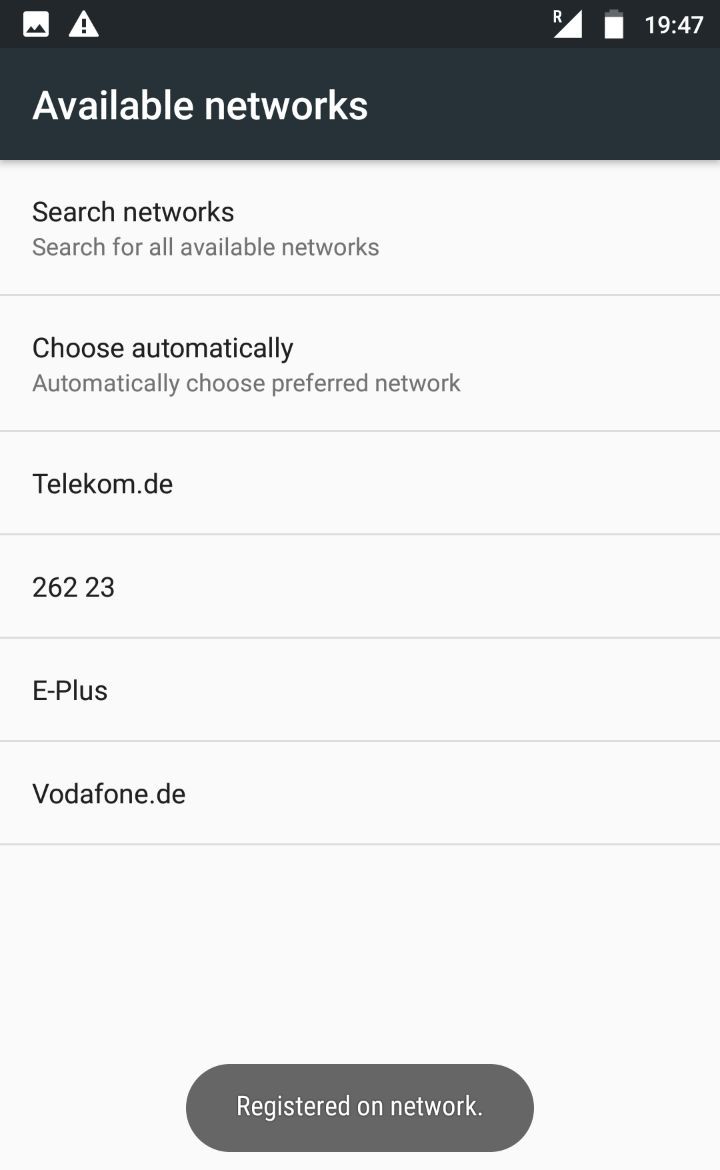
If you see the message, that your phone is registered on the network, then you can confirm that by checking in OpenBTSCLI.
OpenBTS> tmsis
This will show the IMSI of the SIM card that registered to your base station. If you manage to do till here, you already have your first finding which is the IMSI of the SIM card. IMSI is the private identifier of your SIM card. An attacker with an IMSI can identify and track the subscriber’s network and can even try to perform impersonation.
Mobile data sniffing
Once GPRS is working, you should be able to see the symbol ‘G’ in the place where you actually see ‘LTE’ or mobile data symbol in your phone.
Try to google for something in the browser in your smart phone. It is going to be super slow. Remember the old GPRS days. 😀
Open Wireshark in your OpenBTS VM.
You will be able to see the packets..
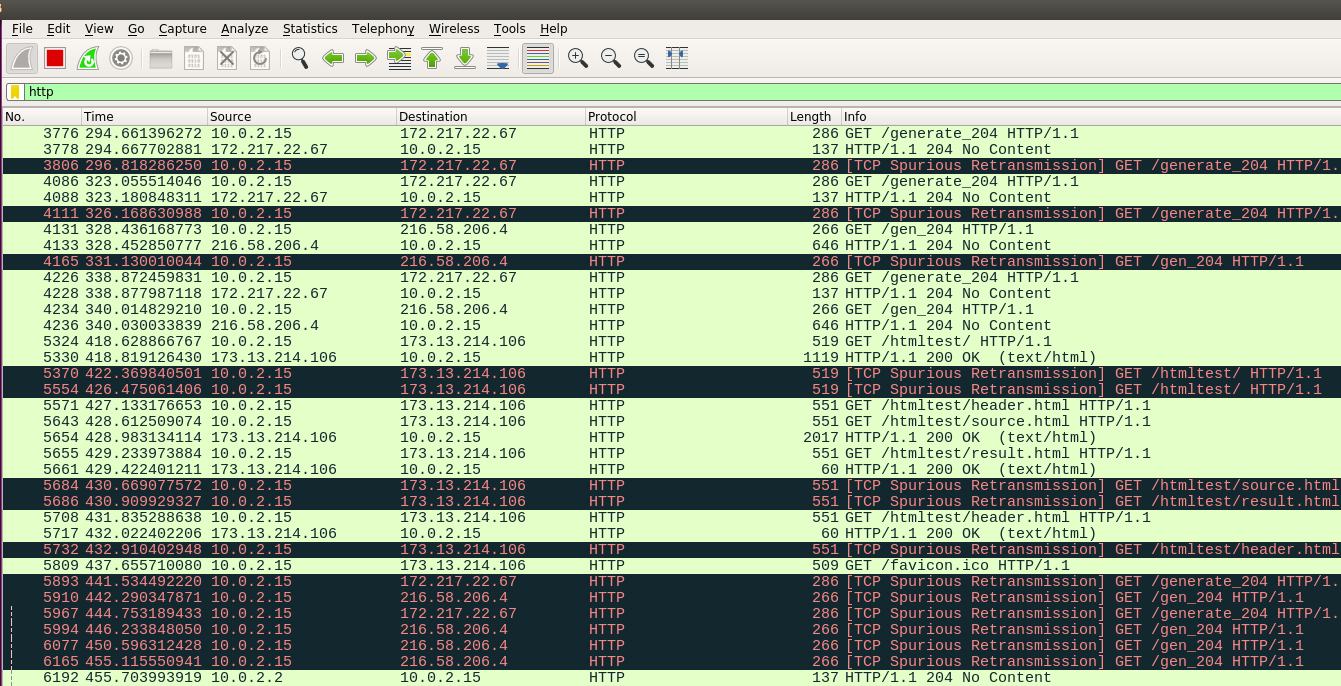
I guess I don’t have to explain further on how to place a Burp proxy for that interface.
We have a full MitM ready for hacking.. yey….
Thoughts on IoT
As we know, none of the devices today are going to use GPRS for connecting to its backend. It is either LTE or at least 3G. If the IoT device is small enough, the best idea to get it connect to our base station is by placing it in a faraday cage. In that case, there are no other signals available and the SIM card gradually connects to our base station. But this is not possible when the device is big like a car. (unless you have a garage with a faraday cage). One possible technique here is to use a jammer so that the SIM card actually disconnects from its original provider. Meanwhile we have our OpenBTS ready next to the device as soon as we turn off the jammer. Then pray and wait for the SIM to actually connect to us. This takes lots of trial and errors. But if we are lucky, we might get a working setup. Also, having a jammer that allows to selectively break only LTE and 3G might lead to downgrade attacks making the SIM connect to our 2G base station. Anyhow, I must say that these are not so easy in practice.
Note: Using a jammer is prohibited in many places. Make sure you can control the range and frequencies disrupted with the jammer. It has to be limited to your device that you are testing.
For those who are really interested in trying 4G sniffing, srsLTE must be interesting.
Hope you enjoyed reading this article.
By the way, if you are into IoT or Telco security, Troopers18 is having some super cool tracks that might be interesting to you. Check out our “Next Generation Internet” and TelcoSecDay for more details.
Ciao,
Priya
Very informative for newbie like me. Thanks
Hi,
Nice article.Any replacement for USRP
Hey thanks. Sysmobts (https://www.sysmocom.de/products/sysmobts/index.html), or nanobts (https://osmocom.org/projects/openbsc/wiki/NanoBTS) are possible alternatives. Check out https://www.sysmocom.de/ in general for more ideas.
good article…
nice article
I will like to know if it is possible to have access over a radio frequency and how
does this have to be done on Ubuntu 12.04?