This is a guest blog post by Salvador Mendoza.
During years, many different researches and attacks against digital and physical payment methods have been discussed. New security techniques and methodologies such as tokenization process attempts to reduce or prevent fraudulent transactions.
Extracting or capturing data from a transaction have been studied in different ways, and some of the most common techniques are skimming, wireless skimming, relay attacks, traffic sniffing or modifying a PoS(Point of Sale) system. In our talk, “NFC Payments: The Art of Relay & Replay Attacks” at TROOPERS18, we will discuss a new technique and methodology that malicious individuals could implement to extract data.

Centinelas: More details in Troopers
Obtaining data from a physical EMV(Europay, MasterCard, and Visa) card seems inadequate and irrational these days because NFC has introduced more attractive and simpler attack vectors . With the EMV specifications, an attacker might not be able to use intercepted data to make a fraudulent transaction because of cryptogram security measures.
Many of the documented relay attacks are determined by the protocols, for example, a relay attack against EMV Chip-And-Pin cards is divided by technology from Chip to Chip protocol. In the same way as the contactless world, we always see relay attacks from NFC to NFC protocol. But analyzing the protocols abstractly, an attacker could communicate with both of them sending the same commands. The reason is because the APDU(Application Protocol Data Unit) layer of the ISO models is shared between them:
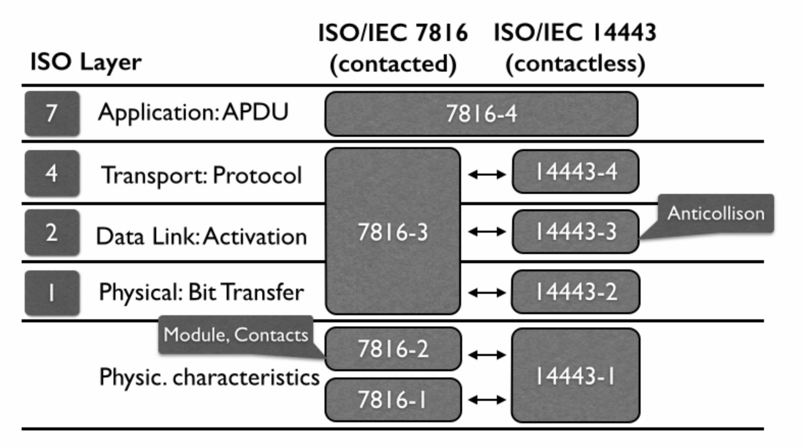
The PoS could determine which protocol will be implemented for the communication when the card answers with its ATR(Answer To Reset). The card could implement T1(block-oriented) or T0(byte-oriented, common) protocol. A malicious user could make some changes in the protocols and have a different relay attack to extract data: sending APDU commands to an EMV card but using NFC technology; abusing the shared APDU layer:
In this PoC video, we can see how a malicious user could implement a relay attack implementing commands from a NFC(Near Field Communication) protocol. In the right side, we have an EMV card inserted into a chip reader in the Centinela 2. In the left side, we have a Android phone behaving as a PoS in the Centinela 1.
The process is simple: Centinela 1 reads the PoS initialization APDU command and transmits it by SDR(Software-Defined Radio). The SDR in the Centinela 2 receives the APDU command and sends it to the EMV card. The card processes the APDU and responds; the Centinela 2 sends that answer back. Repeating this process back and forth until the communication is completed.
With a relay attack, a malicious user can interchange the communication protocols: T0 or T1 in real-time to fool the EMV card. We will discuss more of these techniques and scenarios in our talk at TROOPERS.
Salvador Mendoza(@Netxing)