Dear Readers,
just recently i bought a wireless plug on Amazon with the main use of controlling my coffee machine with an app. The installation of the wireless plug was quite easy and only requires me to set my Wifi SSID and my passphrase – that’s it. But what happened behind the scenes? I visited the control interface of my router and saw that along with the other devices there was a new one with the network name HF-LPB100 and a local IP address in my case 192.168.0.235. First of all i wondered about the name itself, but ignored that and kept on looking for open ports.
So what i did next was running nmap to see if any ports are accessible
Starting Nmap 7.31 ( https://nmap.org ) at 2016-11-15 18:16 CET Nmap scan report for 192.168.0.235 Host is up (0.060s latency). Not shown: 999 closed ports PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 6.71 seconds
As it turned out there was only one port accessible… So i fired up my browser and looked whats there:
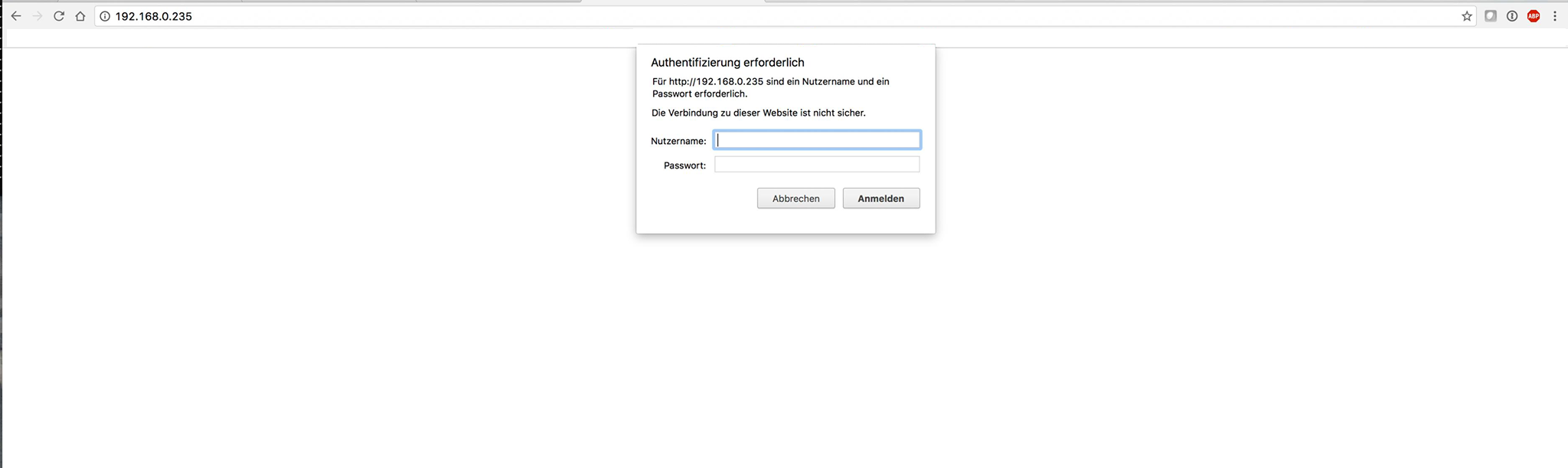
It seems that the web server is secured using .htaccess, as i am not a friend of bruteforcing credentials (and i guess the web server of that device is not that powerful) i went back and looked at other possible solutions to get in. The network name came into my mind HF-LPB100 and after a quick search on Google i found out that it is a “Low power Wifi module” most likely the one that is built into the wifi plug. After a bit of additional research if found the manual for the device. Chapter 3.1 “Configuration via Web Accessing” sounded promising to me.
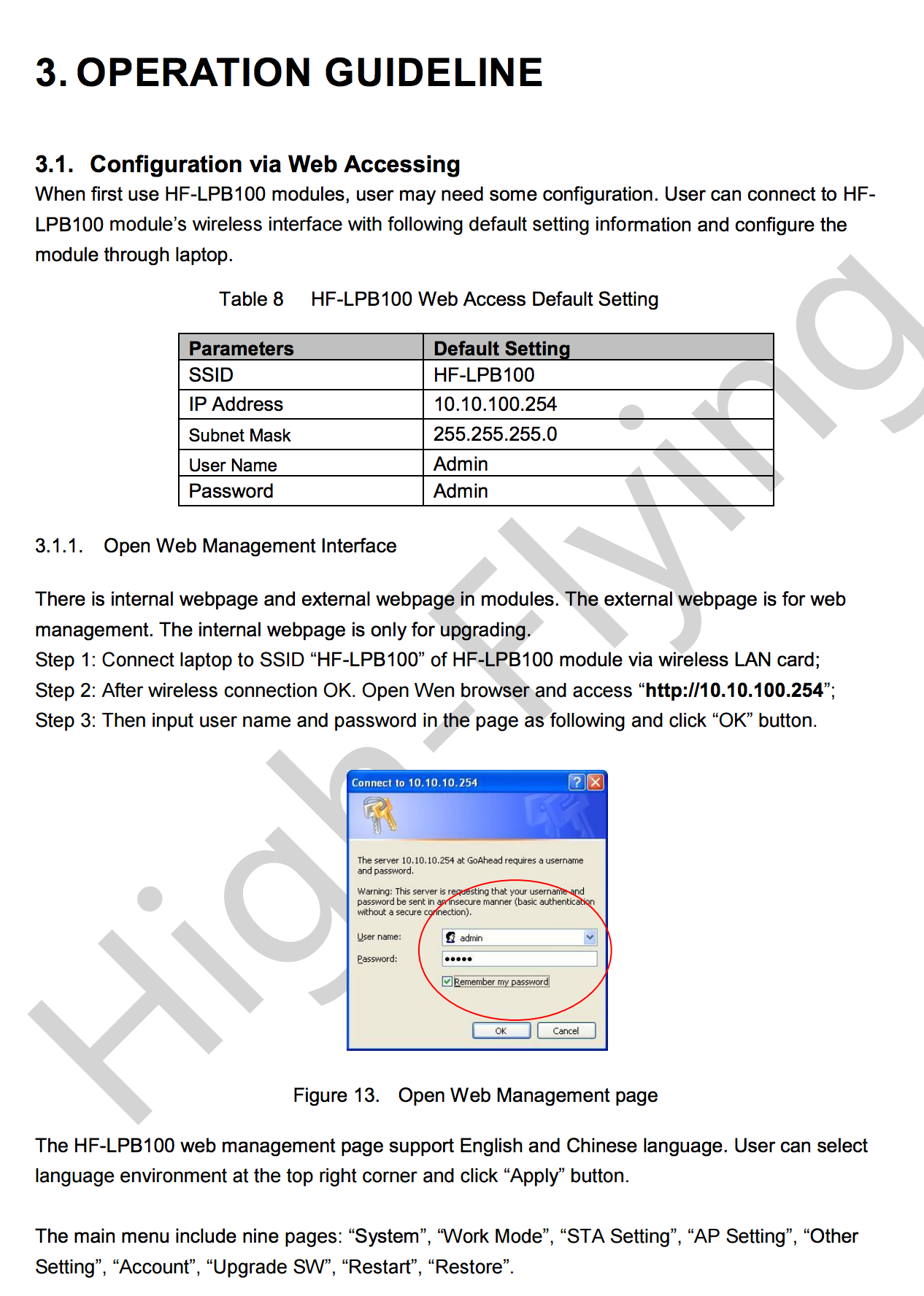
Web Access Default Settings Username and Password is admin / admin ?
No way the vendor has left them unchanged or did they? So i went back to the web interface and tried out the combination admin/admin aaaannnd?
Voilá
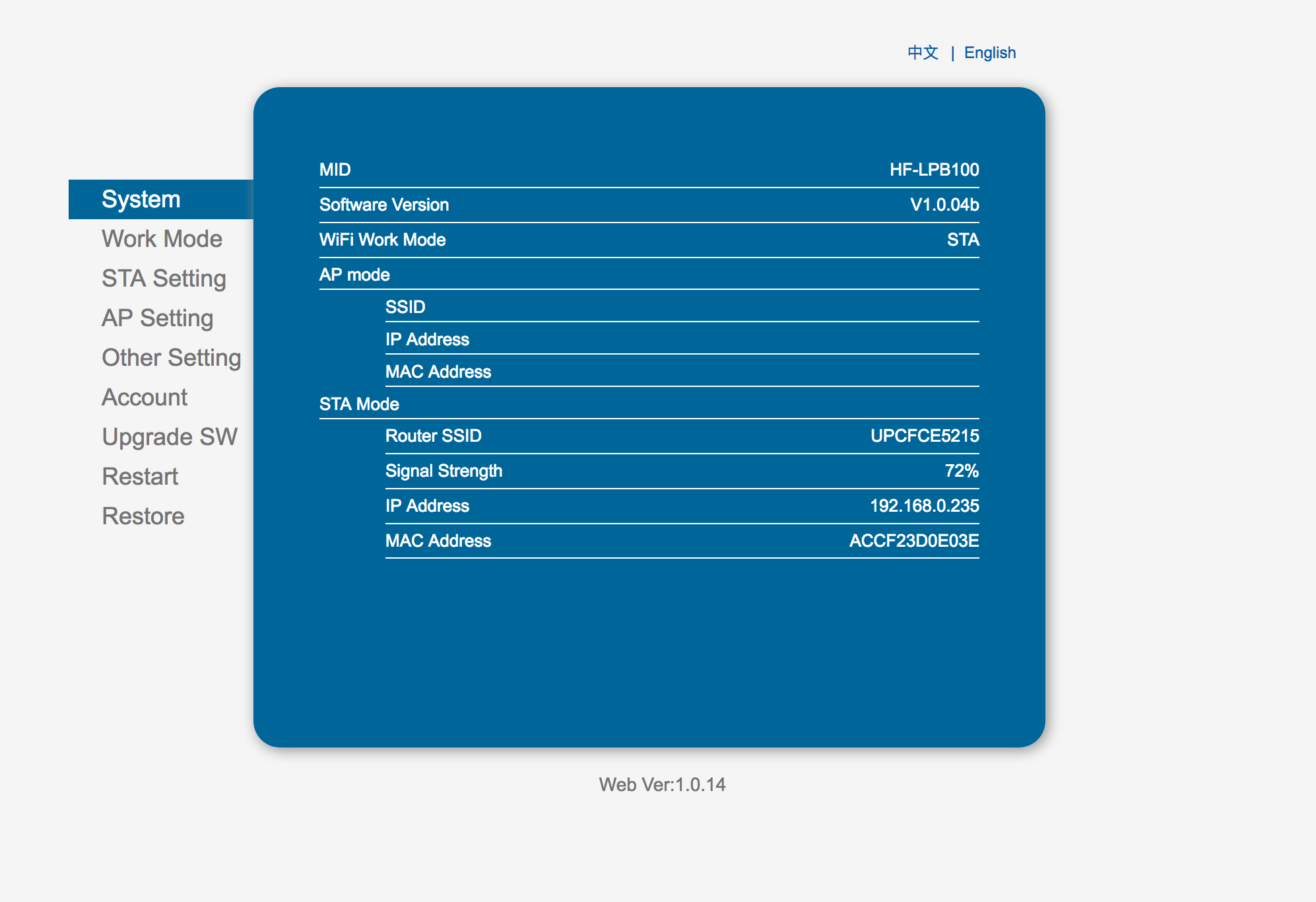
The entire configuration of the wireless plug is now available for everyone in your network 🙂 (If you are one of the brave with IPv6 to the entire world).
So an attacker could now:
- Restart my coffee machine (I DARE YOU!)
- Upgrade the firmware and brick the device
- Change the password of this interface
- Change the network parameter settings (settings for the communication wireless plug > server)
This is yet another example of an administration interface which was never intended to be seen by the end customer of the plug. From a particular point of view this is an advantage as the interface can be used for firmware updates, but in general most of the customers will never update any firmware as it is just a plug and by updating the firmware of the wifi module is renewed and not the one of the plug itself. Therefore, there is no need for such an interface – especially if it is not documented in the plugs manual.
So long,
Patrik
Hi Patrik,
Try 192.168.0.235/iweb.html
Here you can upgrade the frimeware “after” the plug has connect to your network
Alexander