In the context of a customer project, we examined a new variant of the Locky ransomware. As in the meantime stated by a law enforcement agency, this has been part of a large wave of attacks hitting various enterprises in the night from Tuesday (2016-07-26) to Wednesday.
As an initial attack vector, the attackers use emails with an attachment that probably even uses a 0day exploit, that enables the payload to be executed already when displayed in the MS Outlook preview.
The ransomware encrypts accessible documents and threatens victims to pay a ransom in order to be able decrypt the files. Further, the malware uses accessible network shares/drives for further spreading.
Further information is following in the next section.
It might help to create filtering rules based on the mentioned file names, hash values, URLs, and IP addresses that are named in the rest of this report.
1.1 Analysis of the Dropper
A customer provided a sample of an email message that has in a similar form been delivered to multiple recipients within the company. The email contained an attached file named statement[ANONYMIZED].rtf
The cryptographic hash values of this file are:
md5=cfc78becb5354ecbc6b524c8f753f866
sha1=897fbef9e253d9ec980adc97096a8c27baa33aa4
sha256=ccb9b9fcb5d144bd3da74a24c35e7cfcd1cf895963cc815e42ebe60da5cc6360
Although the file name extension suggests an RTF document, the document is actually in MS docx format. Both file types are usually associated with MS Word as default application for opening.
When opening the document, it displays an embedded image file in the internal path word/media/image1.jpeg that is meant to trick the user to enable macros.
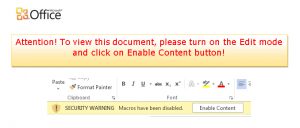
The document indeed contains the following VBA macro:
VBA-Makro: CreateObject(XI(“M16Byh”, “7C65111A1A2441420116063943592E573B2E435F320D2B225F42301604”, 6, 29))
According to an unverified statement of a law enforcement agency, the document also facilitates a zero-day exploit, which triggers the payload already when viewed in the MS Outlook preview.
The payload downloads a MS Windows PE binary file named c1.exe from the following URL:
http://indatronic.es/c1.exe
The domain indatronic.es during our analysis resolved to the IP address 91.121.236.165
The binary file is then saved under the following path:
c:\users\<username>\appdata\local\temp\36086.exe
1.2 Analysis of Malware Binary
We calculated the following cryptographic hash values of the downloaded binary file 36086.exe:
md5=e31df3282758158f2df7422ffd41412f
sha1=08cbc99a7ceac9a07d0c8b41238f88b9e5a67d23
sha256=af23f42a0a62e876a7a3776cd171a578da125ac68fdcc6d55f8382b0816c6499
After being executed, the malware binary 36086.exe showed the following behavior during our analysis:
- Terminates Windows Firewall
net stop MpsSvc, C:\Windows\system32\net1 stop MpsSvc - Disables automatic start of Windows Firewall Service
sc config MpsSvc start= disabled - Opens up MS Internet Explorer
“C:\Program Files (x86)\Internet Explorer\iexplore.exe” -nohome - Deletes all volume shadow copies (Local Windows System Backups, System Restore Points)
vssadmin.exe delete shadows /all /quiet - Initiates TCP communication with another Host with the IP address 138.204.170.84
- The encryption of user documents could not be observed in the controlled environment, but in the customer context, documents of multiple file types have been encrypted.
- The attackers want the victims to pay a ransom in order to decrypt those files.
1.3 Spreading of the malware
Our customer observed spreading behavior of the malware in order to infect other hosts by placing a binary file on network shares that are accessible on infected machines under the following file name in the root directory of the share. The actual IDs contained in the file name have been anonymized.
$RECYCLE.BIN.{12345678-1234-1234-1234-123456789ABC}\{12345678-1234-1234-1234-123456789ABC}.exe
Further, all folders on the share are renamed to a random name and a LNK-file with the original name of each folder is created, that first executes the binary file and then opens the corresponding renamed folder.
1.4 Indicators and Countermeasures
The malware identifies in various AV signatures as:
W2KM_DL.FBEE686D
W2KM_DLOADR.YYSQM
W2KM_LOCKY.DLXFW
TSPY_FA.C5529BD9
TSPY_FAREIT.YYSVM
W2KM_DRIDEX.SMX3
Ransom_CRYPWALL.GHN
The Outlook Preview function can be disabled under
Outlook Options -> Trust Center -> Trust Center Options -> Attachment Handling
There, check “Do not Preview Attachments”.
The same can be achieved via GPO by setting the following registry key:
HKCU\Software\Microsoft\Office\15.0\Outlook\Preferences\DisableAttachmentPreviewing
In general, you may want to reconsider whether the preview feature is required at all — it would certainly remove significant attack surface from your mail clients.
Please reach out to us if you have further questions, or you are interested in our Incident Response/Forensic Computing training at Troopers17.
Cheers,
Andreas
Well, i use Microsoft Outlook cloud-based, how does it afect it? My enterprise as buyed the Outlook for the company (NetShares).
Hi Skylle,
it shouldn’t affect you in the first place, because even if the exploit also works against the cloud hosted Outlook version, from that environment there should not be any direct access to your documents. Attackers might of course try to add other exploits on top, to attack your users’ browsers for example when using the cloud app, but this would require lots of further effort on their side, which I don’t see for the moment.
Best,
Andreas