On the 8th of March SAP released the security note for a vulnerability we reported during an assessment of a SAP landscape. The issue affects the SAP NetWeaver Web Administration Interface. By knowing a special URL a malicious user can acquire version information about the services enabled in the SAP system as well as the operating system used. We wanted to share some details on the issue.
The vulnerability is a bypass of the HTTP Basic Authorization for the SAP Web Administration Interface. It discloses version information about the system respectively operating system, a brief SAP patch level overview and running services including their corresponding ports.
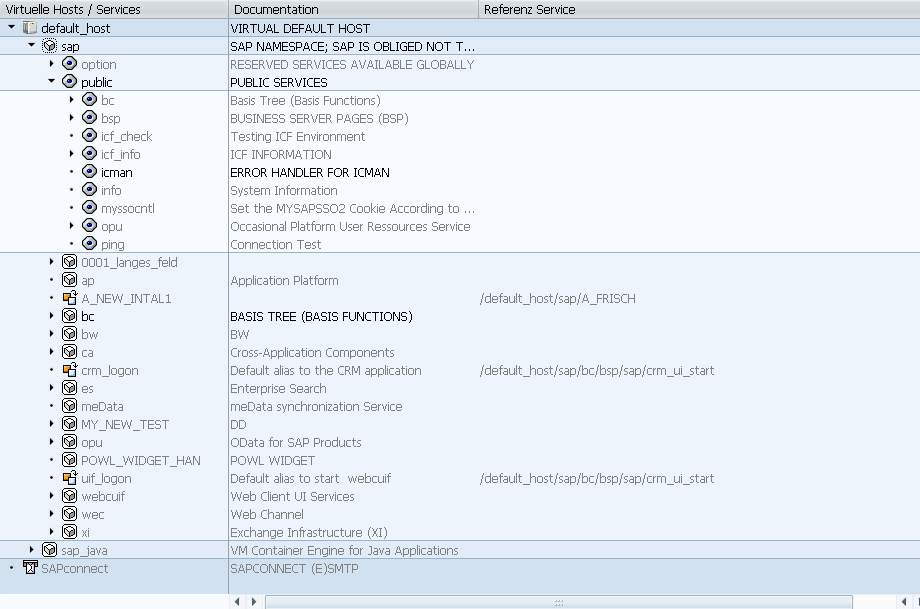
Netweaver SAP systems offer different services on URL paths which can be configured using transaction SICF as shown in the image below. The affected service endpoint is not present in this list. Correct me if I’m wrong, but my expectation is that the ICM administration interface should be listed here as well.
Proof-of-concept
The following (original) request prompts the user for HTTP basic authentication:
GET /sap/admin/public/default.html HTTP/1.1
Host: SAP-SYSTEM:8014
By changing the URL path to the following address, it will bypass the HTTP Basic authentication and the malicious user is signed in as “guest” in our example SAP-SYSTEM.
HTTP-Request (Modified):
GET /sap/admin/public/index.html HTTP/1.1
Host: SAP-SYSTEM:8014
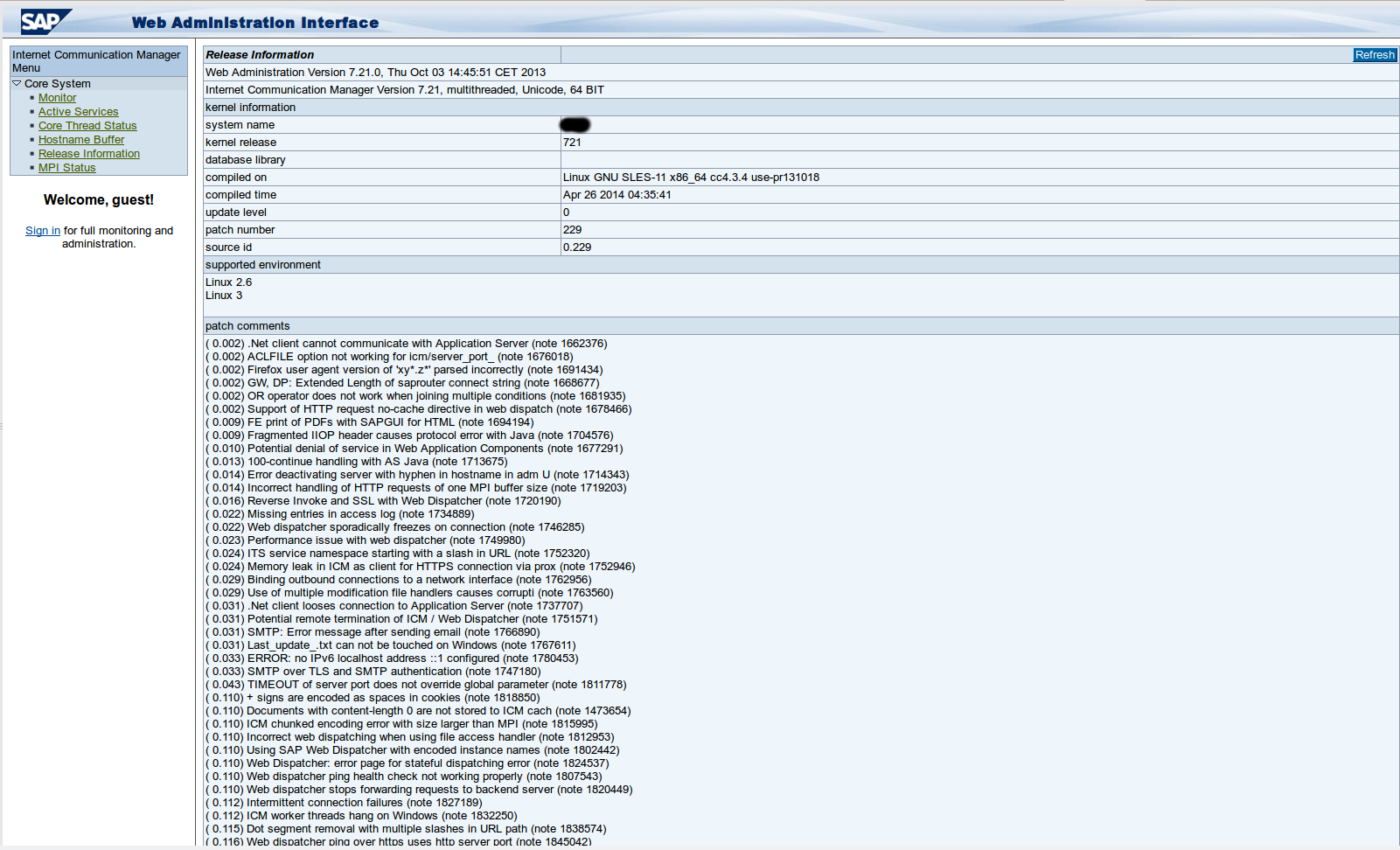
The attached screenshot illustrates the view an attacker has when visiting the edited URL (/sap/admin/public/index.html)
To fix this issue you should install the security note 2258786 or see THIS note if you can´t install the security note for some reason. The article describes how to filter URL requests using the configuration file DEFAULT.PFL using parameter. There are exact examples for this vulnerability/bug in the linked article. Although it’s only an information disclosure, this could help an attacker to prepare further attacks based on the patch level of the system or by identifying if there is network filtering in place. He could scan the system and compare the results to running services in the web interface identifying the attack surface of the system. As this is easy to reproduce and discloses valuable information you should take action and mitigate this issue, especially if your system is exposed to the internet.
Timeline of the disclosure process:
14.12.2015 – Initial report of the vulnerability
15.12.2015 – Confirmation of the vulnerability
08.03.2016 – Release of security note
20.06.2016 – Blogpost
Have a safe day
Wojtek
Nice one. Keep looking 🙂