Dear readers of Insinuator,
Today I want to give a little review about the latest app released by SektionEins called “System and Security Info” due to its recent media appearance. So first of all the app can be obtained via the Apple App store for 0,99€ at the time this article was written. This article will try to answer two basic questions: for whom (or “which groups of people”) is this app helpful, and which security features does this app actually has. The design of the app is straight forward and pretty minimalistic with a clean and modern design. The first page of the Application called “Overview” provides nothing more than the current CPU usage of the device, with detailed subdivision in User, Idle, Total and Load. The next section provides an overview about the used RAM divided into Wire, Active RAM usage, Inactive RAM usage, “other”, free and the total amount of the device’s ram. The next option shows the used and unused part of the devices available storage, with “used”, “free” and total amount of space. While these features can be handled with several other (free and open source) applications I won’t write a comment wether it these components make sense.
What I think is nice about this app is the feature which shows the current running processes, once pressed it shows all processes running on the device with information about the identity of the app (the developer) the team identifier of the developer and the CD Hash, and hash type. Also, the signer of the App (on non-jailbroken iDevices this is, in any case, the App store for installed Applications or “adhoc” of default system binaries). Another helpful option is to display the CS Blob Flags and the CS progress flags which can be really helpful while tracking down a malicious application. I have to confess these features are helpful for iOS Developers or people involved in mobile application security, but I don’t see the use case for the average iDevice user yet (Users without any modification to the device like a Jailbreak e.G.). As there is a feature that does show the current cpu load, I’d have expected the app to show which application does consume a lot of CPU and therefore may be causing the battery to run out faster.
Now comes the really interesting part called “Security”. Basically, in this section there are two available options, one called “Jailbreak” and the other one is called “Anomalies”. Let’s review the first option, the Jailbreak detection part. What’s impressive here is that the app is able to recognize about forty commonly changed files, permissions, and additional system files provided during the jailbreak process. The application is capable of recognizing several jailbreaks. These so called Jailbreaks are developed by different groups such as Pangu and evasi0n7 and taig. The first question that came into my mind was, to whom is this helpful? The short story, for the average iDevice user without a jailbreak… well this is… unnecessary The long story: As it turns out, each jailbreak leaves a fingerprint of modified files and added binaries on the device, recognizing one that does not fit into the fingerprints could be an indicator for a previously unknown jailbreak that is in the wild. The potential reason this could happen is state driven malware, or espionage on a specific person. A nice to have in terms of user security would be to show which files are modified in a “clean” jailbreak and which appeared there additionally. The additional files could indicate that the device was jailbreaked using a malware infected jailbreak from un-trusted sources. Due to the popularity of jailbreaks a lot of fake services are offered around the internet to infect naive users with annoying Malware.
The next option of the “Security” part is the anomalies section, this section provides six checks of anomalies that should not occur on an iDevice, if not set on purpose. The application checks for multiple anomalies such as non-apple daemons found on the system, attached debuggers, code signing integrity, manipulated CS flags, or injected libraries. If you are the regular iDevice user, and you bought the device from a store, use the latest iOS version you should only have green dots next to the description. If you have bought a second hand device without entirely wiping and re-installing the device this might be interesting for you, as criminals sell specially prepared iDevices to spy on the user and steal passwords or banking / credit card details. If you are a citizen from an oppressed country and you are targeted by your government this might also be interesting for you since this could be an indicator that something is wrong with your device and you should get rid of it ;-).
We are almost finished with the app, the last part left (apart from the info section) is the so called “Details” section. I am not sure what exactly the intention behind this part is, but I find it a bit useless since it’s only providing basic information about the system. Although this may sound a bit rough the main intention of this blogpost is not to bash anyone (especially not Stefan Esser) who constantly contributes to mobile security, but rather clarify the scope of function this app provides.
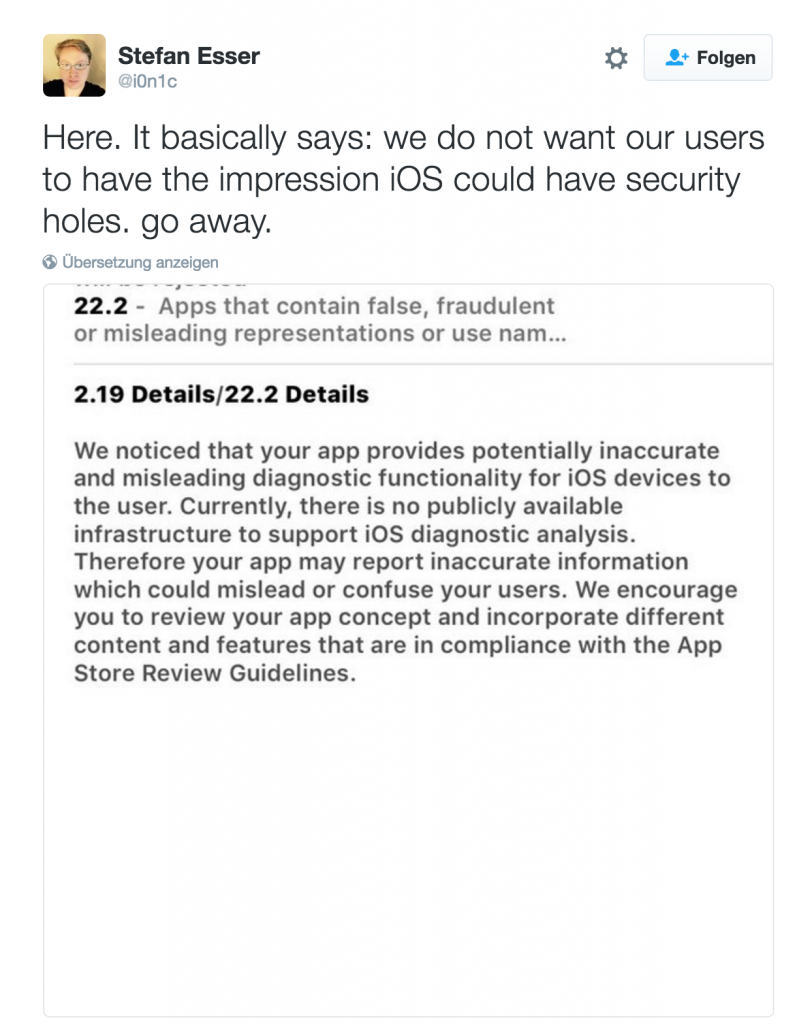
Update: Before we even could finish this blogpost Apple removed the app from the app store (http://www.iphonehacks.com/2016/05/apple-pulls-stefan-esser-jailbreak-detection-app-from-the-app-store.html). In my opinion Apple took a wrong path by locking out the app from the app store. It might not be useful for the majority of the users, but those who really need it will have a hard time to get their hands on it. I really hope Stefan will continue, and Apple will make up their mind what’s useful for their users and what is not.
All the best
Patrik & the MobSec Team of ERNW