Felix Wilhelm presented in his talk various ways to attack his new target – The PA-500 which is produced by Palo Alto Networks.
He discovered vulnerabilities in 3 different exposed aspects of the device. The first vulnerability occurred inside of an unauthenticated API from the Management-Website which could only be accessed within the Admin Network. This vulnerability was a typical off-by-one Command Injection, which could be abused by reaching out to the API with a special client=wget Request.
Some Checks needed to be bypassed which could be done with about more than 1024 “A” s inside of the POST body.

Further he explained as well how the User-ID Feature can be exploited in a special scenario which can be pretty common inside of corporate Networks. The attached picture shows the potential exploitable Setup.
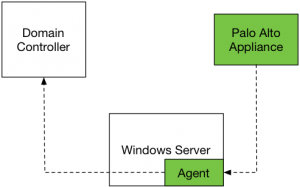
The problem lies within the User-ID probing Feature which asks the clients for their authenticated User through Netbios/WMI. This Service is potentially reached within the whole corporate Network and could lead to unauthorized access to several Resources.
The exploit was not published since it was still going through the responsible disclosure process.
The last Exploit which has the most impact hits the GlobalProtect feature which is a world exposed SSL-VPN/IPsec Service which can be also used from smartphones. This Service is implemented on top of a Web service (Appweb3 + PHP) and some functionality does not require authentication. Felix Wilhelm talked about the limited attack surface he had when he triggered the Overflow with “Ä” s which limited him to only use UTF-8 characters and the first appearance of data execution prevention (DEP) which is called eXecute Inhibit on MIPS64.
The basic mistake he illustrated with the following picture was not to sanitize a valid pure utf8 input.
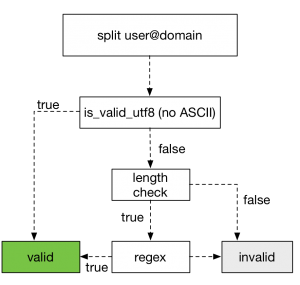
He could circumvent all Protections with some precision Heap spray and gained Code-Execution on the System which delivered him a root Shell.
To Wrap his talk up he talked about different Recommendations for the manufacturer and highlighted the professional handling on behalf of Palo Alto and was quite positive about the future development of the devices.
The slides of his Talk are here.
Cheers,
Birk
Hello,
I saw the very interesting presentation at https://www.youtube.com/watch?v=ZoCf9yWC32g and I wanted to play around with a PAN at my lab but trying to execute: test scp-server-connection initiate hostname “-oProxyCommand = chsh -s /bin/bash admin” username a password b
Always return “Server error : Pseudo-terminal will not be allocated because stdin is not a terminal.” reading more about the error I understood this is because the wrapper test command is not including the “-t -t” option to the underlaying ssh command. I am interested to know how you got around that?
Hi JA,
you can pretty much ignore that error message. The command is still executed even if you do not see the output. If you just open a new connection to the CLI using the admin user you should drop into a standard bash. However, I would recommend to add another dedicated user and change its shell instead so you can still access the normal CLI using the admin account.
-Best,
Felix
Hi there,
Great article, i’m having some fun with this myself on my lab box, what is the best way to obtain root privileges so i can create my new root user?
Thanks,
Hi,
do you have a Virtual Machine or Bare Metal?
And do you already have Bash Access to the System but running under low privileges?
If you have a Virtual Machine you can tamper with the running Memory using Snapshots. Thus you can get a root user with the Admin CLI.
If you already have standard Bash Access I suggest looking for some Privilege Escalation problems.
Cheers,
Birk
Hi Birk,
Thanks for the reply, good tip on playing with the memory in a VM – i’ll remember that for the future.
In this case i’m on bare metal:
Linux 2.6.32.27 #1 SMP x86_64 x86_64 x86_64 GNU/Linux (gcc version 4.1.1 20070105 (Red Hat 4.1.1-52.2))
vendor_id : GenuineIntel
model name : Intel(R) Celeron(R) CPU P4505 @ 1.87GHz
Yes i have a bash but low privileges and would like root.
I do have access to the HDD so tried creating a new user on the bare metal, mount HDD in another system, give new user GID:0 with /bin/bash and then try to login. On login it waits a while and re-writes the /bin/bash with /usr/local/bin/cli in passwd so knows something is up.
There is no gcc but we do have rpm,python,tftp,wget and can write to /tmp so getting files on and off is easy.
Cheers,
Mark
Hi Mark,
yeah i remember some Shadow passwd on the filesystem. But i have not looked into that directly.
You could tamper also with the /usr/local/bin/cli and try to symlink this to /bin/bash. But luckily as i gave the hint previously there were just a full disclosure on privilege escalation 🙂
Full Disclosure
This might lead you to root 🙂 this should also work on the newest versions
Cheers,
Birk