While running some SS7 pentests last year, I developed a small tool automating some of the well-known SS7 attack cases. Today I’m releasing the first version of ss7MAPer, a SS7 MAP (pen-)testing toolkit.
The toolkit is build upon the Osmocom SS7 stack and implements some basic MAP messages. At its current state tests against the HLR are ready for use, in future versions tests against VLR, MSC and SMSC will follow.
The source code of the tool is published on github, feel free to use and extend.
The tool is written in Erlang; to get it running you will need the Erlang runtime environment. It is developed for version 17.5.
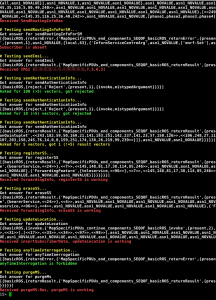
As example, the screen shot below shows the output of the tool against a HLR, testing which MAP messages are accepted and the results given back.
As you can see in the picture, the demonstrated test cases for the HLR respond to most of the MAP messages regardless the fact that we are not registered as valid provider. The tool is not configured as a serving MSC nor a roaming contractor. Some of the information gathered can be seen as critical, as the MSISD -> IMSI resolution, the over-the-air crypto keys or the ability to create supplementary services e.g. call forwarding.
The code (and its dependencies) are not that easy to compile but I tried to give a complete step by step instructions in the README file.
The messages and test cases are gathered from public SS7 research of the last years (see 1, 2) and check for known weaknesses in the SS7 domain.
The tool itself was developed under a cooperation with the Belgium provider Proximus and aims to test the secure configuration of the internal and external SS7 network access. Thanks a lot for giving us the opportunity here, we are convinced that the tool gives the research community but also telecommunication providers a new, important and (especially) open-source-based possibility for SS7 testing.
More about the tool and SS7 testing on Troopers TelcoSecDay, Telco Network Security & Network Protocol Fuzzing Workshop.
That’s it, get the code, try the tool.
Best wishes from Heidelberg.
/daniel
thanks alot for this contribution, i need to know if there any simulation tools to simulate the nodes (HLR,MSC,..etc) as we need to simulate the attacks, and dont want to test the toolkit first on live nodes.
also when will the messages/attack scenarios for VLR/MSC, and the rest of the nodes be updated?
Hi,
I have not found any software so emulate the target devices (HLR, MSC, etc.). It might be done with jSS7 (https://github.com/RestComm/jss7) but I’ve not tested this. There is an open source implementation of a SGW (https://sourceforge.net/projects/openss7gw/) that can be used to test the M3UA part of the application.
To implement further attacks I would need access to an SS7 network with the components reachable. I will likely get access to a real SS7 environment again later this year.
cheers
/daniel
Dear Daniel,
thanks for your reply, i would like to know if am testing against live nodes, do i have to get an interconnect or you can connect through ss7 thrid party access providers, and do you recommend any?
Hello
I want to know how you could get access to ss7 network.
Did you do that by Osmocom SS7 stack and connected to Real operator BTS’s ?
Hi,
yes, that’s the way we are using the toolkit.
cheers
/daniel
Did you release other part of you toolkit against VLR, MSC and SMSC?
Regards
Hi,
we are going to release more test cases in the future. At the time writing tests against MSC and SMSC are implemented, but not verified, yet.
cheers
/daniel
For support or bugs of any kind, please use the issue tracker at https://github.com/ernw/ss7MAPer/issues
cheers
/daniel
Can you explain how to using this script on windows binary (https://github.com/ernw/ss7MAPer/blob/master/releases/ss7MAPer-v0.2_win_x64.zip) ?
Or maybe need another software before run it on windows mode ?
Need your advise…
Hello Daniel,
Assuming we have the permission from a telecom operator, what do we need as hardware/OS/packages to setup a server for connection to SS7 network and how to verify the connection setup is working? Can you provide information on this?
Thanks
i have downloaded the binary from https://github.com/ernw/ss7MAPer/blob/master/releases/ss7MAPer-v0.2_win_x64.zip but still unaware of how to install it in windows machine. please guide in detail.
is it possible for having a viewing of signalisation with wireshark !?
Wireshark is able to show ss7 protocols as well.