Welcome to Dayton
In mid-October our friend Bryan Fite aka Angus Blitter invited the community for the ninth edition of Day-Con. Bryan’s annual security summit, which we regard as the sister event of TROOPERS, is a pretty good reason to visit lovely Dayton, Ohio.
And so we did… ERNW sent in five delegates. Delegates is Day-Con-speak for all attendees and speakers and such a subtle choice of wording sets the tone for the whole event. People seemed to be really focused and the roundtable-like setting during the talks (see above) provided a cozy atmosphere for in-depth expert chatting.
Talks, Talks, Talks
After an opening keynote by Ron Gula from Tenable Network Security another specialty of Day-Con became obvious: Lots of honest discussion! Loyal Day-Con original Bigezy didn’t let off from Ron easily and he finished up with the question: “I know what you said as a CEO of Tenable, but what do you REALLY think personally? Do you REALLY believe what you just said?” – a great start into an open discussion culture throughout the next days. Luckily most of the content was shorthanded and will be available online soon (keep an eye out for “summit notes” on the event’s website).

Line-up of speakers was pretty strong: Sergey Bratus, Jacob Torrey, Adrian Dabrowski, two of our favourite Kiwis Neilson Graeme & Vladimir “Vlad” Wolstencroft – just to name a few. As usual Sergey had his fun illustrating his latest research with animal analogies (see above). In case you wonder: His second talk on day 2 was all about ice bears with books on their back 😉 Most slides are ready to download here. Combined with the transcripts they should provide you some good insights into the content.
Looking at ERNW’s contributions Matthias Luft brought new content to the table with his “Tools of the Trade & Security Theater” talk. He was starting off with a rant on how strange it is that most businesses buy expensive security appliances without verifying the marketing promises to a sufficient level. Some simple, yet provocative questions were raised, like “Do you actually know which file types are filtered/scanned by your malware detection systems?” Towards the end of the talk Matthias opened discussion for some nifty ideas (check out last slides) how to combat those shortfalls in the future. Personally I can’t wait to see them becoming reality!
There was a huge load of variety among the talks: Adrian for example elaborated on the idea of having something like a robot.txt for your face, to control how social media websites, media in general and all those face scanning/tagging algorithms out there are allowed to deal with photos you are on. Interestingly this topic, which felt quite natural and meaningful to privacy-aware people (yep, this included all Germans among the audience!) stirred up controversy with some US-citizen in the room. Fear spread that such a mechanism would have some kind of chilling effect for photographers who already struggle to get usage permission from their subjects nowadays.
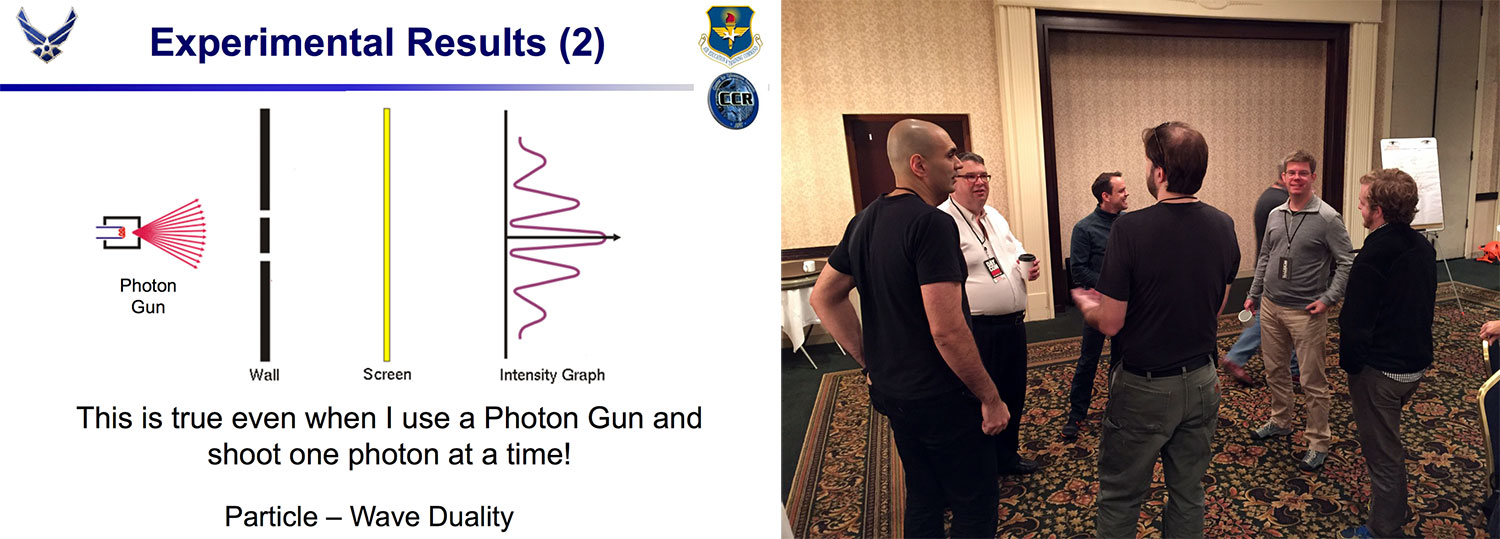
Michael Grimaila from the Air Force Institute of Technology did a great job with his “Gentle Introduction to Quantum Key Distribution“, a topic which needs a calm and seasoned guy like him. To be honest: I could listen to him again right now. The insights, illustrated with plenty of pictures were new and mind-blowing to me. Applying this to the encryption of satellite communication is another challenge in itself, which (again) provided some good follow-up discussions (see above).
On day 2, the host Brian Fite, presented his thoughts on “how to hide from robots” (which was actually this year’s PacketWars theme), covering all aspects of what might come in the future and how to react to it. Providing plenty of hands-on ideas, he also concluded with a classic “Don’t panic. Its inevitable. Prepare accordingly!” advise at the very end.
“I said some terrible things to her.” – @gramx talking about his work with @amazon alexa #daycon9 #coneofsilence
— TROOPERS Conference (@WEareTROOPERS) October 15, 2015
Something truly unexpected was presented by Graeme Neilson: He presented his journey trying to jam several robot listening services (namely: Apple’s Siri, Ok Google & Amazon’s Alexa) and common wireless networking services. 
While a white noise generator (on the right) proofed to be very effective against the unwanted listeners, he ran into some trouble to implement a jamming device for WLAN/Bluetooth/cellular services with his HackRF. Nothing which couldn’t be fixed with a high-voltage spark from a BOSCH ignition coil (on the left)… those crazy Kiwis! 😉
Fun, Fun, Fun
To cut things short: Consider joining Bryan, us and the rest of the #DayCon family next year in Dayton, Ohio. It’s worth the trip – I promise. Besides great contacts and solid contents, it’s just a very fun time to be there. If a picture is worth a thousand words, let’s end this blog post with a whole gallery! It even includes one classified snapshot of a special mission we carried out during Day-Con 9. If you want to find out more about it follow this space, or even better grab a ticket for TROOPERS16 right now. We can’t wait to start teasing about it more…
Take care & thanks for reading!
Florian